Security Practitioner
SEARCH
CATEGORIES
TAGS
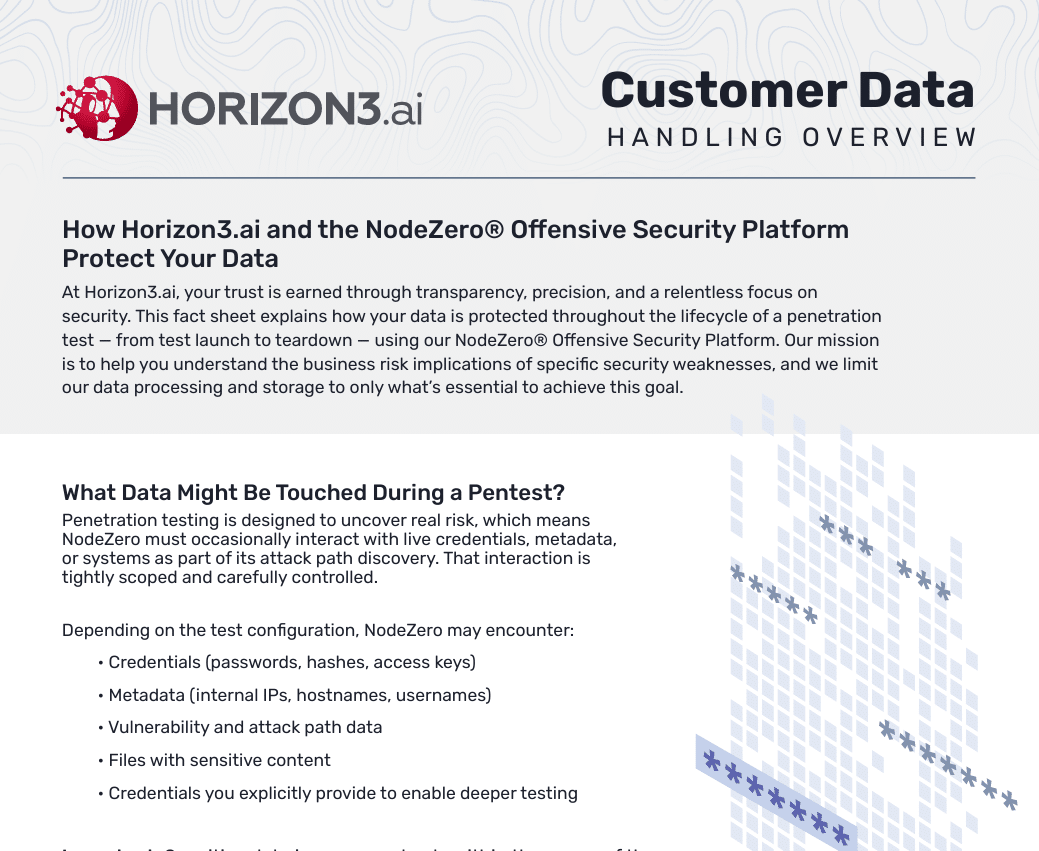
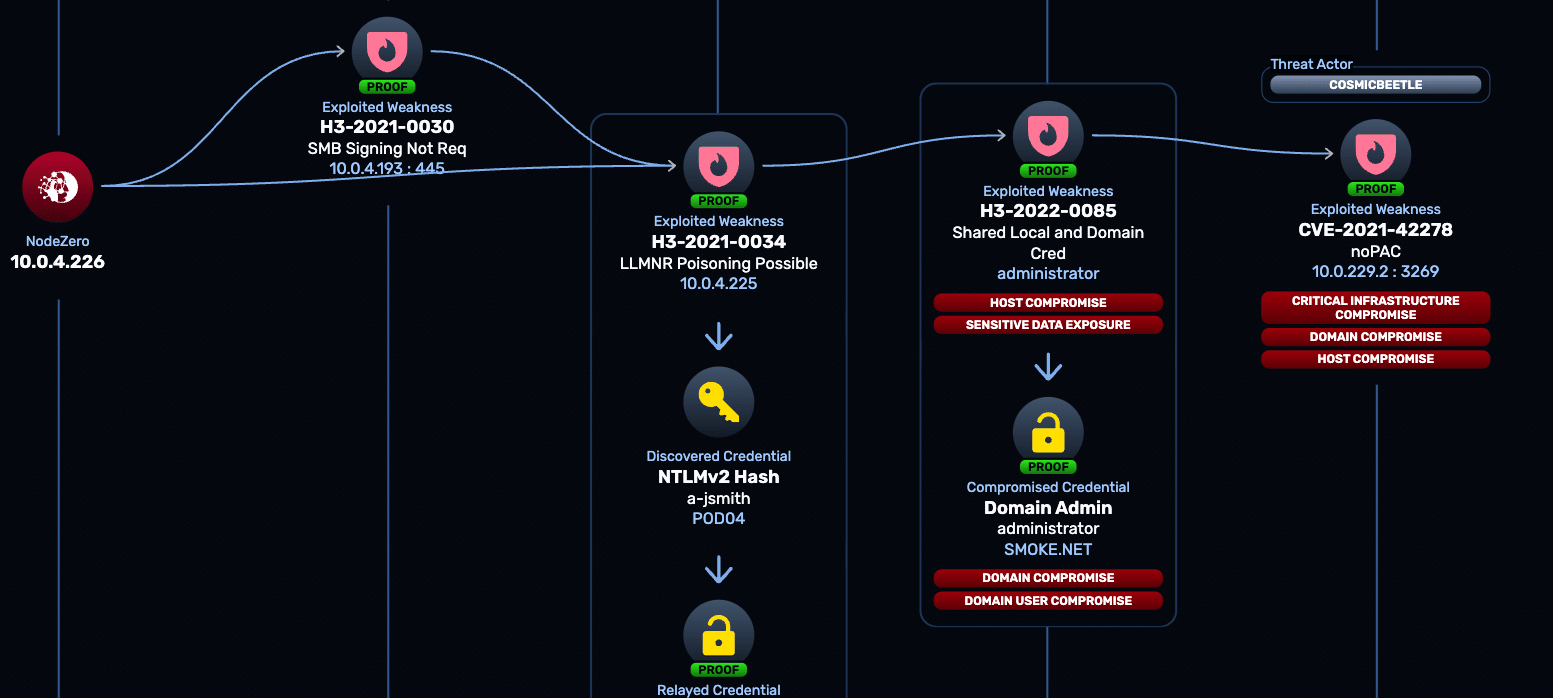
Customer Data Handling Factsheet
November 25, 2025
At Horizon3.ai, transparency and security go hand in hand. The NodeZero® Offensive Security Platform protects your data during every test — encrypting communications, limiting retention, and ensuring no sensitive data leaves your environment. Download the factsheet to see how our strict controls safeguard customer information from launch to teardown.
Supercharging Enterprise AI with Real-World Exploitability Data: The NodeZero MCP Server Advantage
Learn how the NodeZero MCP Server supercharges enterprise AI ecosystems with attacker-validated exploitability data, continuous validation, and automated security workflows.
From Awareness to Assurance: Turning Cybersecurity Awareness Month into a Year-Round Practice
October 29, 2025
Cybersecurity awareness training builds knowledge—but not proof. This post shows how to evolve from education to validation by continuously testing your defenses with NodeZero®. Discover how real-world verification closes policy gaps, exposes hidden risks, and transforms one month of awareness into year-round assurance your security truly works.
Threat Actor Intelligence: Known Threats, Known Weaknesses, Known Outcomes
September 12, 2025
Awareness doesn’t equal defense. Threat Actor Intelligence helps you go beyond the headline: “Are these attackers using techniques that would actually work in our environment?”
NodeZero® for Pentesters and Red Teams
August 20, 2025
Pentesters and red teams share a common goal: improving an organization’s security posture. But their objectives, scope, and methods differ. NodeZero® helps both teams succeed by showing what’s truly exploitable, so you can cut through the noise and continuously validate your security posture.
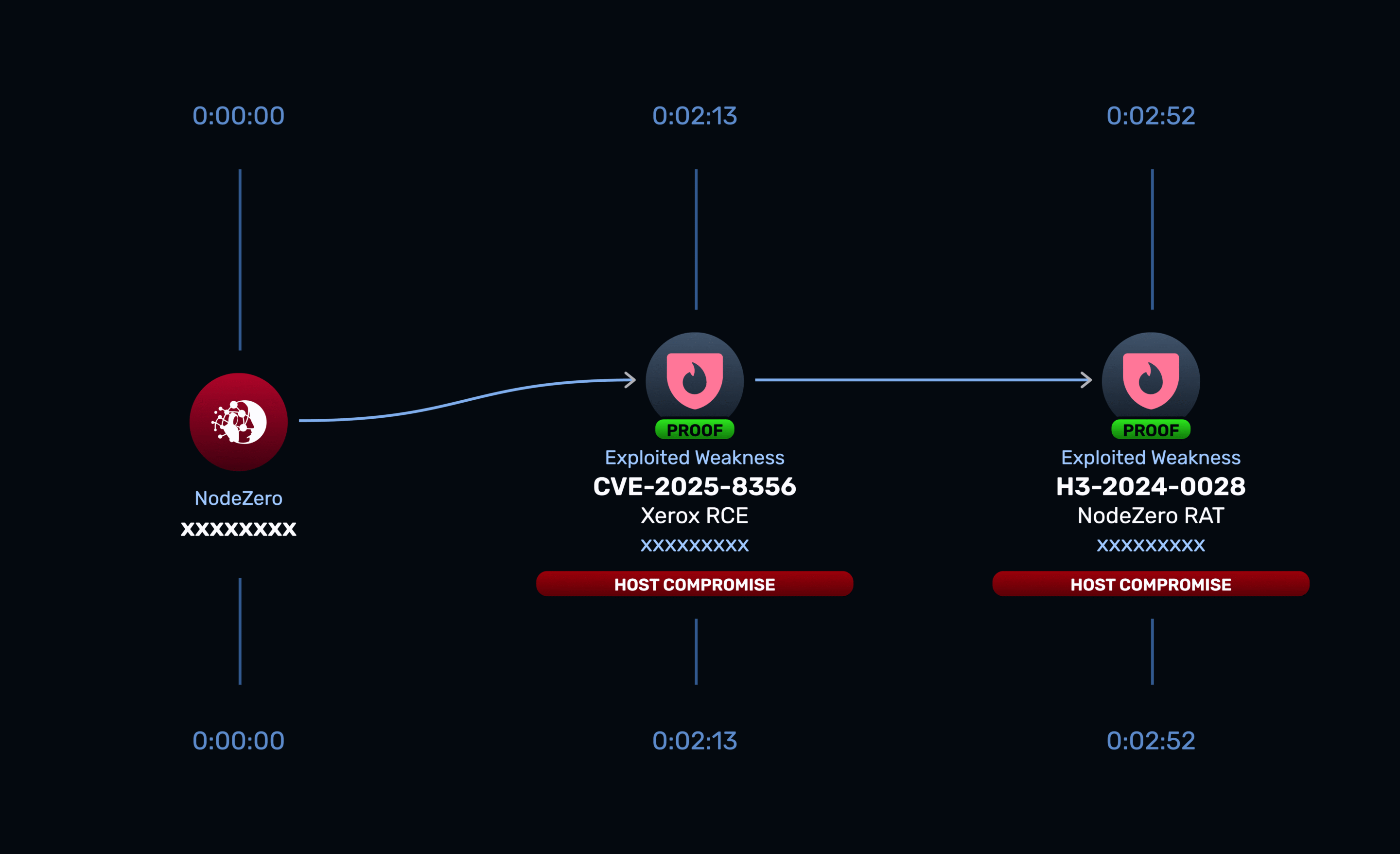
From Support Ticket to Zero Day
August 13, 2025
Examining a Critical Vulnerability in Xerox FreeFlow Core
Vulnerability Management Is Broken: There is a Better Way
July 28, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Unlocking Next-Level Security with Horizon3.ai & Optiv
Horizon3.ai and Optiv lead the charge in the ever-evolving, innovation demanding field of cybersecurity. Find out how in this webinar.
CVE-2025-5777: CitrixBleed 2 Write-Up… Maybe?
July 7, 2025
Background and Confusion On June 17, 2025, Citrix published an advisory detailing CVE-2025-5777 and CVE-2025-5349. Affected products include: On June 25, 2025, they also published an advisory detailing CVE-2025-6543. Affected products include: Of the three vulnerabilities, two of them have been receiving a bit of buzz: While we’ve developed a working exploit for one of…
Unmasking Risk: The CISO’s 100-Day Guide to Autonomous Testing, Security Validation, and CTEM
July 1, 2025
A practical 100-day guide for CISOs to mature security fast with autonomous testing and CTEM—prioritize risk, drive action, and stay ahead of threats.