Security Practitioner
SEARCH
CATEGORIES
TAGS
ManageEngine CVE-2022-47966 Technical Deep Dive
January 19, 2023
Introduction On January 10, 2023, ManageEngine released a security advisory for CVE-2022-47966 (discovered by Khoadha of Viettel Cyber Security) affecting a wide range of products. The vulnerability allows an attacker to gain remote code execution by issuing a HTTP POST request containing a malicious SAML response. This vulnerability is a result of using an outdated…
ManageEngine CVE-2022-47966 IOCs
January 13, 2023
Introduction The recent ManageEngine CVE-2022-47966 is a pre-authentication remote code execution vulnerability. Depending on the specific ManageEngine product, this vulnerability is exploitable if SAML single-sign-on is enabled or has ever been enabled. ManageEngine products are some of the most widely used across enterprises and perform business functions such as authentication, authorization, and identity management. Given the nature…
Get the Most From TrendMicro Apex One EDR with NodeZero
December 12, 2022
Learn how you can use NodeZero to get the Most From TrendMicro Apex One EDR, ensuring you stop, alert, log, and detect activity by bad actors.
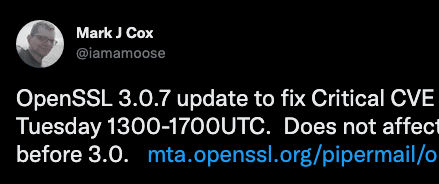
OpenSSL Critical Vulnerability: Should You Be Spooked?
October 26, 2022
On Tuesday, October 25 a new OpenSSL hot-fix release was announced which will patch a critical vulnerability that exists within the v3.0.X branch. OpenSSL 3.0.7 will be released on Tuesday, November 1 and in tandem the details of the vulnerability and its associated CVE will be made public. OpenSSL is an open source project that…
Horizon3.ai Breaks Down Fortinet Vulnerability
Horizon3.ai Breaks Down Fortinet Vulnerability Zach Hanley, Horizon3.ai Chief Attack Engineer, and James Horseman, Exploit Developer, join John Furrier of theCUBE to discuss Fortinet CVE 2022 40864.
FortiOS, FortiProxy, and FortiSwitchManager Authentication Bypass Technical Deep Dive (CVE-2022-40684)
October 13, 2022
Fortinet recently patched a critical authentication bypass vulnerability in their FortiOS, FortiProxy, and FortiProxySwitchManager projects (CVE-2022-40684). This vulnerability gives an attacker the ability to login as an administrator on the effected system. To demonstrate the vulnerability in this writeup, we will be using FortiOS version 7.2.1
Putting Your Security to the Test with NodeZero
Putting Your Security to the Test with NodeZero with Anthony Pillitiere and Clayton Dillard / CEO Legion Cyberworks.
FortiOS, FortiProxy, and FortiSwitchManager Authentication Bypass IOCs (CVE-2022-40684)
October 11, 2022
Introduction The recent FortiOS / FortiProxy / FortiSwitchManager CVE has been reportedly exploited in the wild. We would like to provide additional insight into the vulnerability so users can begin to determine if they have been compromised. In this post we discuss enabling logging and IOCs for FortiOS 7.2.1. These steps will likely work on…
Vulnerable ≠ Exploitable: A lesson on prioritization
September 13, 2022
Pen testers, vulnerability scanners, and installed agents alert on potential vulnerabilities and breaches. You receive a list, or a notification, and you respond. Ever wonder how much of your time and effort is being wasted fixing things that don’t actually matter?
Are Your Kubernetes Clusters Configured Properly?
August 31, 2022
Researchers recently discovered some 900,000 Kubernetes clusters that were potentially exposed to malicious scans and data theft during a threat-hunting exercise.