Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
SmarterTools SmarterMail Remote Code Execution via Unauthenticated Arbitrary File Upload | Critical
Read More →MongoDB Server Uninitialized Heap Memory Disclosure (MongoBleed) | Active Exploitation
Read More →WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
How Often Should You Pentest?
Annual pentesting leaves blind spots. Learn why modern threats demand frequent or continuous pentesting to stay ahead of attackers.
From Patch Tuesday to Pentest Wednesday®: Proof That Reshaped Security for a Gaming Operator
September 17, 2025
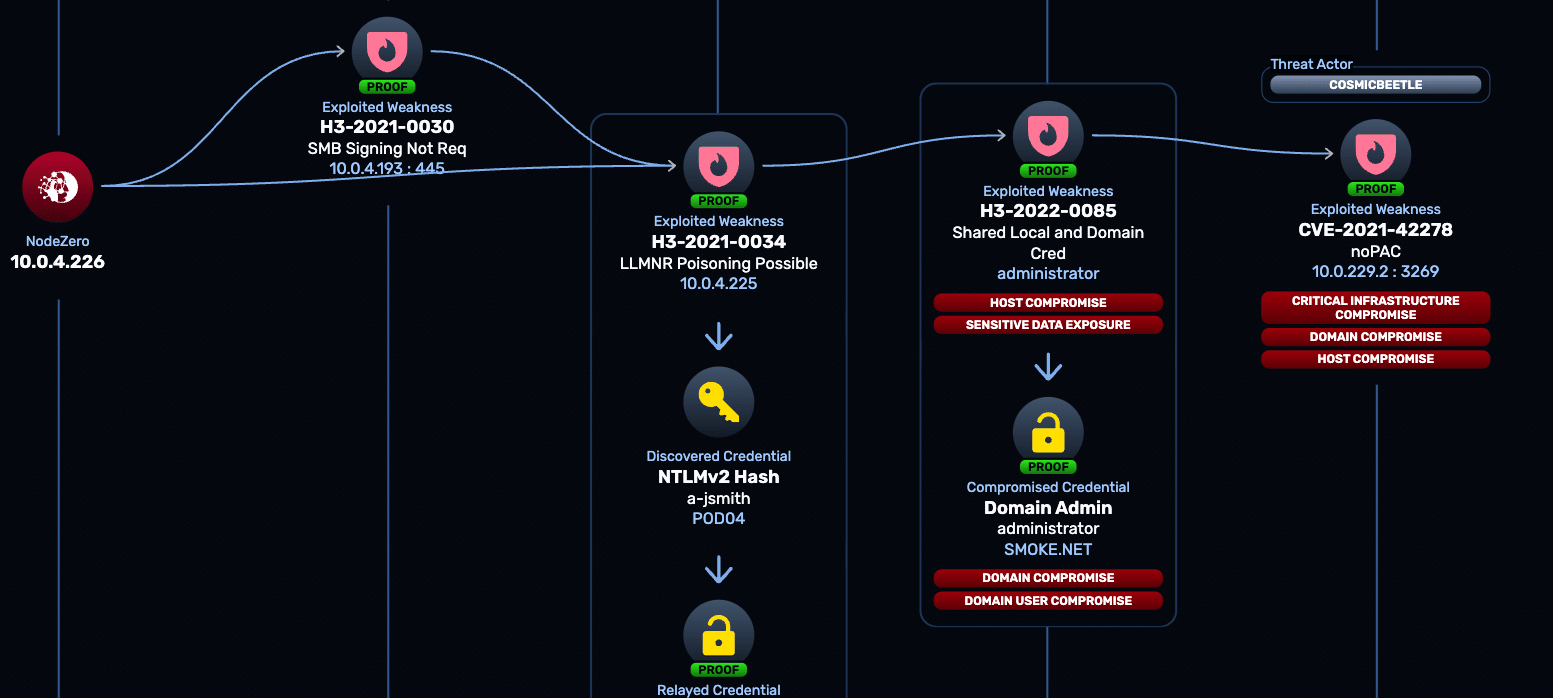
A U.S. casino's first pentest uncovers 756 weaknesses & 143 attack paths, sparking a new, proof-driven approach to security.
Threat Actor Intelligence: Known Threats, Known Weaknesses, Known Outcomes
September 12, 2025
Awareness doesn’t equal defense. Threat Actor Intelligence helps you go beyond the headline: “Are these attackers using techniques that would actually work in our environment?”
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for a Large Insurer
September 10, 2025
The simple truth is that supply chain security depends on validation, not paperwork. Pentest Wednesday is about moving from forms and annual tests to continuous testing and measurable risk reduction, replacing paperwork with proof.
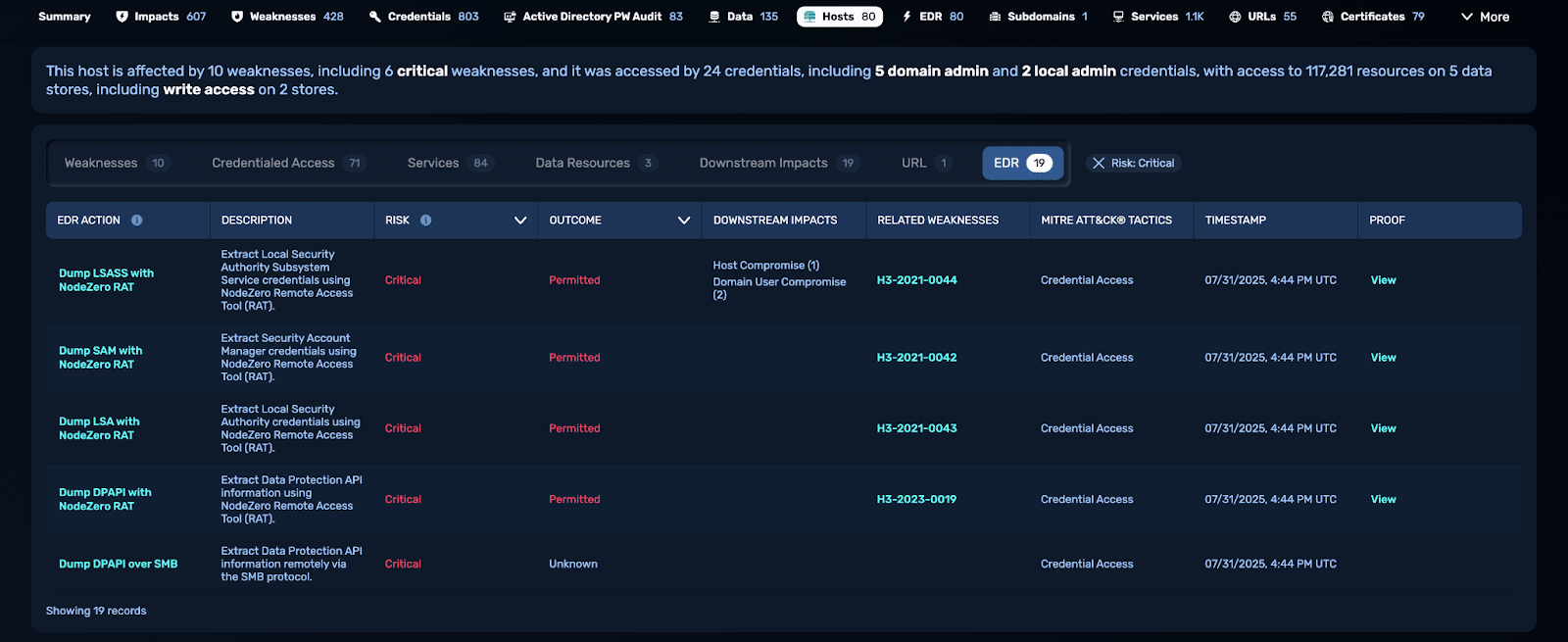
Endpoint Security Effectiveness: From Assumption to Proof
EDR and XDR platforms are positioned as the backbone of endpoint protection. They promise to detect, block, and contain threats before attackers can gain a foothold. Yet many organizations are left asking the same questions: Where is our EDR deployed? Is it configured properly? Could something be slipping through? The uncomfortable truth is that most…
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for the Defense Industrial Base
September 3, 2025
The simple truth is that supply chain security depends on validation, not paperwork. Pentest Wednesday is about moving from forms and annual tests to continuous testing and measurable risk reduction, replacing paperwork with proof.
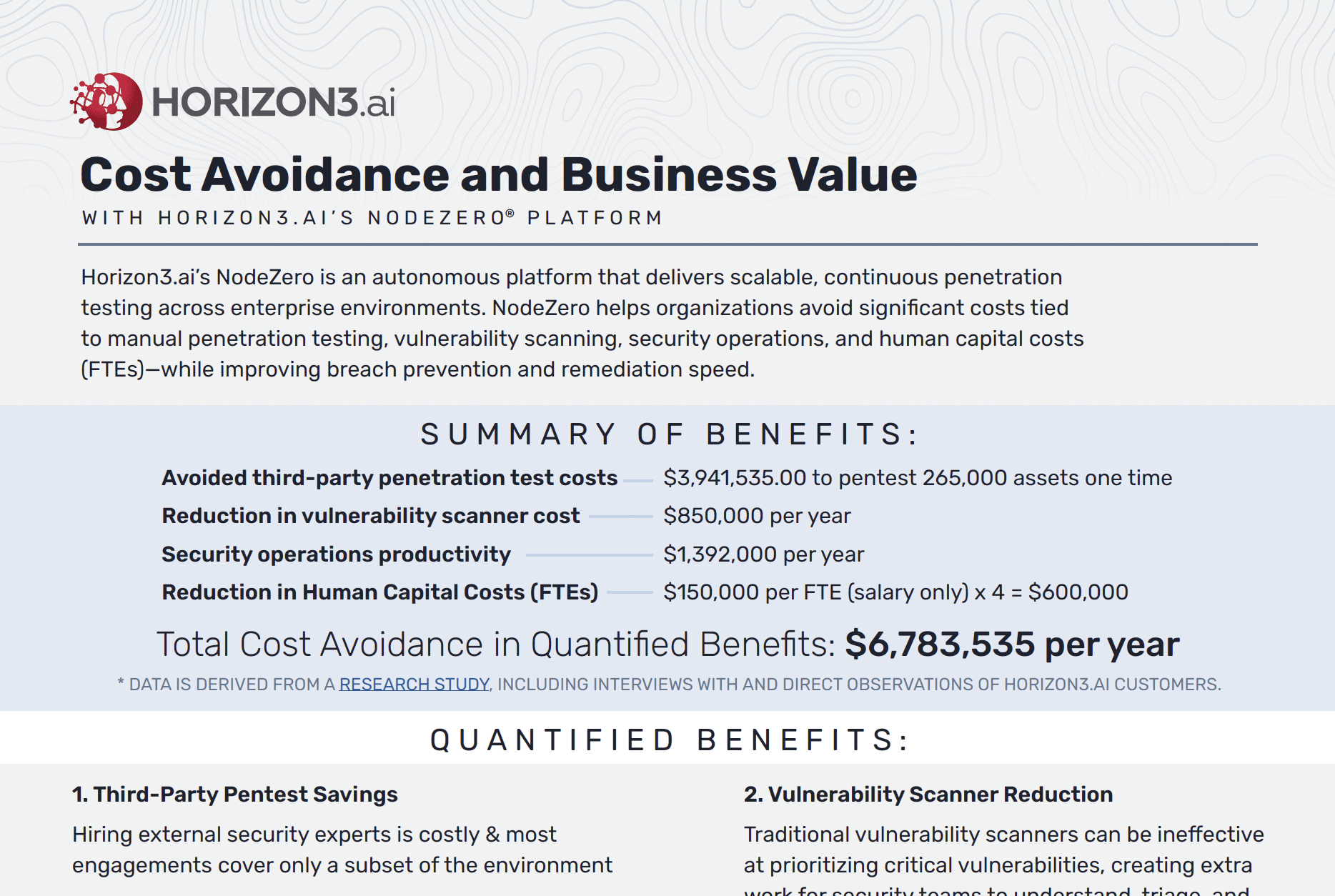
Cost Avoidance and Business Value with NodeZero®
August 29, 2025
Horizon3.ai’s NodeZero® delivers $6.78M annual cost avoidance by replacing pentests, reducing scanner costs, and boosting security ops.
From Noise to Proof: Reinventing Vulnerability Management with NodeZero®
Vulnerability management wasn’t designed to deal with real attackers. That’s the problem. Most programs drown in scan data, chase vulnerabilities with high CVSS scores with no context, and still can't answer a simple question: Are we exposed? This isn’t just another dashboard. You’ll see how NodeZero: If you're tired of measuring risk with guesswork, this…
NodeZero® for Pentesters and Red Teams
August 20, 2025
Pentesters and red teams share a common goal: improving an organization’s security posture. But their objectives, scope, and methods differ. NodeZero® helps both teams succeed by showing what’s truly exploitable, so you can cut through the noise and continuously validate your security posture.