Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
NextGen Mirth Connect Remote Code Execution Vulnerability (CVE-2023-43208)
October 25, 2023
Mirth Connect, by NextGen HealthCare, is an open source data integration platform widely used by healthcare companies. Versions prior to 4.4.1 are vulnerable to an unauthenticated remote code execution vulnerability, CVE-2023-43208. If you’re a user of Mirth Connect, you’ll want to upgrade to the latest patch release, 4.4.1, as of this writing.
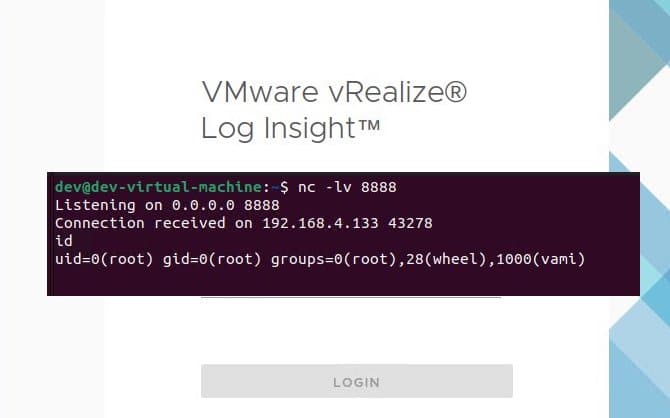
VMware Aria Operations for Logs CVE-2023-34051 Technical Deep Dive and IOCs
October 20, 2023
Introduction This report is a follow up to https://horizon3.ai/vmware-vrealize-log-insight-vmsa-2023-0001-technical-deep-dive/. Earlier this year we reported the technical details for VMSA-2023-0001 affecting VMware Aria Operations for Logs (formerly VMware vRealize Log Insight). In that report, we showed how an attacker could use three different CVEs to achieve remote code execution. During the course of that investigation, we…
Cisco IOS XE Web UI Vulnerability: A Glimpse into CVE-2023-20198
October 19, 2023
On Monday, 16 October, Cisco reported a critical zero-day vulnerability in the web UI feature of its IOS XE software actively being exploited by threat actors to install Remote Access Tools (RATs) and backdoor vulnerable devices exposed on the internet.
The Art Of Attack—Enhancing Defense Strategies: Unleashing The Power Of Autonomous Pen Testing | A Brand Story Conversation From Black Hat USA 2023 | An Horizon3.Ai Story With Snehal Antani
October 12, 2023
A Brand Story Conversation With Sean Martin And Snehal Antani, Co-Founder & CEO At Horizon3.ai
Tech Talk: Journey to OSCP
Horizon3.ai Senior Engineer Noah King discusses the journey of obtaining an Offensive Security Certified Professional (OSCP) certification. Whether you're a cybersecurity enthusiast or a beginner looking to explore the field, you'll learn tips and tricks to help you navigate the certification process, including: - How to get started in Offensive Security with little or no…
Apache Superset Part II: RCE, Credential Harvesting and More
September 6, 2023
Apache Superset is a popular open source data exploration and visualization tool. In a previous post, we disclosed a vulnerability, CVE-2023-27524, affecting thousands of Superset servers on the Internet, that enables unauthorized attackers to gain admin access to these servers. We also alluded to methods that an attacker, logged in as an admin, could use…
Enhancing Splunk Deployments with NodeZero
September 1, 2023
As security threats continue to evolve and become more sophisticated, the need for advanced security mechanisms and strategies has become paramount. Two technologies that stand out in this domain are the NodeZero platform and Splunk.
Ivanti Sentry Authentication Bypass CVE-2023-38035 Deep Dive
August 24, 2023
Introduction Ivanti has recently published an advisory for CVE-2023-38035. The vulnerability has been added to CISA KEV and is described as an authentication bypass in the Ivanti Sentry administrator interface. This new vulnerability comes on the heels of an in-the-wild-exploited vulnerability in Ivanti EPMM (CVE-2023-35078). In this post we will take a deep dive into…
Go Hack Yourself: War Stories from ~20k Pentests with NodeZero │ Security Weekly
Horizon3.ai CEO Snehal Antani discuss several real-world examples of what autonomous pentesting discovered in networks just like yours. You’ll hear more about how fast and easy it was to safely compromise some of the biggest (and smallest) networks in the world - with full domain takeover in a little more than a few hours. Learn…
Lexmark Command Injection Vulnerability ZDI-CAN-19470 Pwn2Own Toronto 2022
August 10, 2023
Introduction In December 2022, we competed at our first pwn2own. We were able to successfully exploit the Lexmark MC3224i using a command injection 0-day. This post will detail the process we used to discover, weaponize, and have some fun with this vulnerability. You can find our POC here. Printer Acquisition It was rather difficult to…