Downloads
SEARCH
CATEGORIES
TAGS
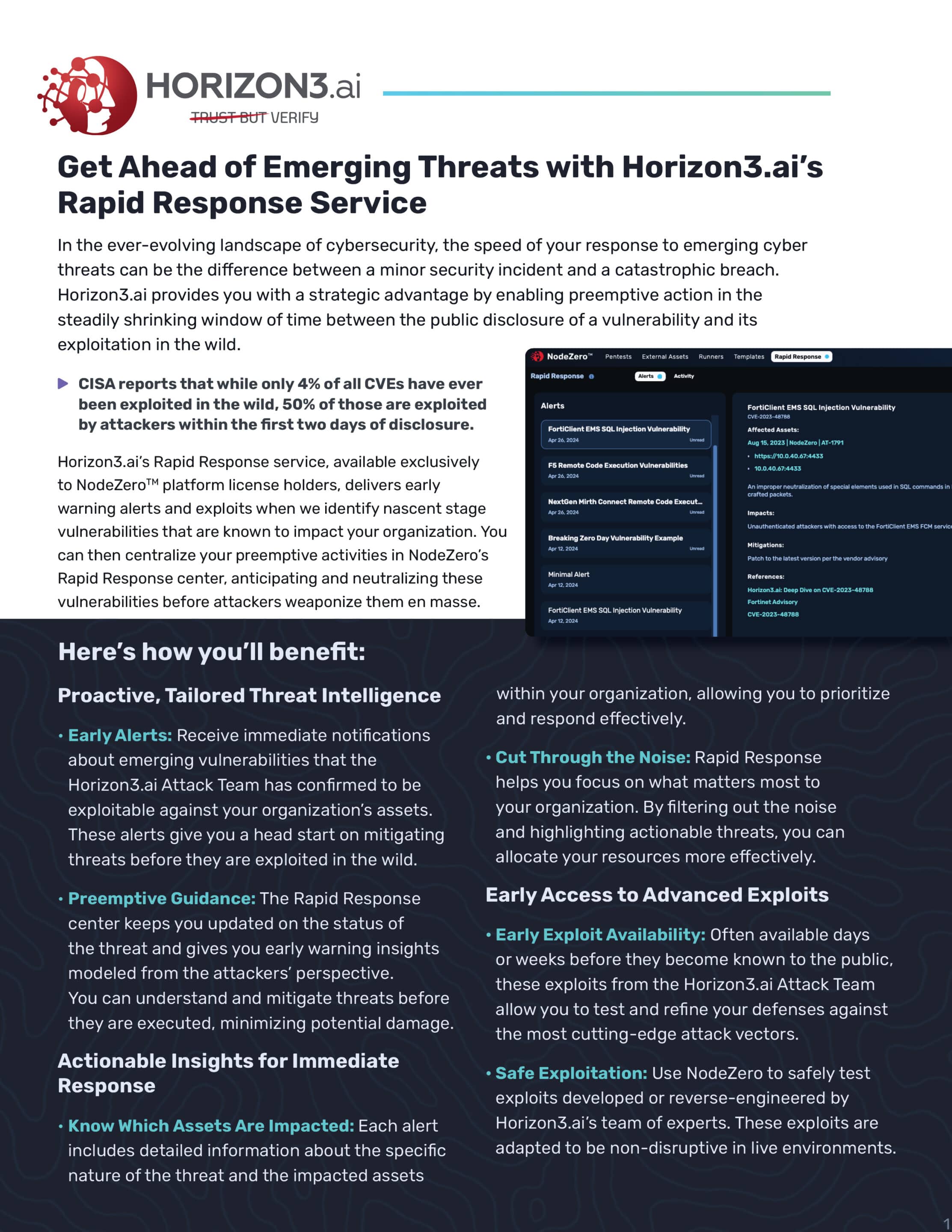
Get Ahead of Emerging Threats with Horizon3.ai’s Rapid Response Service
April 30, 2024
In the ever-evolving landscape of cybersecurity, the speed of your response to emerging cyber threats can be the difference between a minor security incident and a catastrophic breach. Horizon3.ai provides you with a strategic advantage by enabling preemptive action in the steadily shrinking window of time between the public disclosure of a vulnerability and its…
Fix What Matters: Accelerating Cyber Defense Through the Eyes of an Attacker
April 30, 2024
The emergence of new attack vectors, the steady growth of attack surfaces, and the increasing speed at which vulnerabilities are exploited underscore the critical need for proactive defense strategies.
Fortifying the Chain: A Proven Strategy for Supply Chain Defense
April 24, 2024
Understanding the Landscape of Cyber Threats and the Innovations in Third-Party Risk Management
NodeZero® Exploits
April 23, 2024
The NodeZero platform’s advanced algorithms and testing methodologies allow it to exploit a wide range of security vulnerabilities.
NodeZero™ from Horizon3.ai Optimized for MSSPs and MSPs
April 4, 2024
The NodeZero platform enables you to proactively and efficiently probe your customers’ networks for weaknesses that go beyond known and patchable vulnerabilities, such as credentials open to compromise, exposed data, misconfigurations, poor security controls, and weak policies.
SLED U.S. State, Local, & Education
April 4, 2024
State, local and education (SLED) organizations have unique pain points. Because they rely on taxpayer dollars, SLED organizations are often trying to do more with less.
Horizon3.ai Pentesting Services for Compliance
April 1, 2024
Meet compliance with expert-led pentesting and NodeZero’s continuous testing—find, fix, and verify what matters most, all year long.
NodeZero: More than a concept — a Proof of Value
April 1, 2024
See your enterprise through the eyes of an attacker - More than a concept — a Proof of Value
Horizon3.ai PCI 11.4 Pentesting Engagement
April 1, 2024
Horizon3.ai delivers sophisticated and timely penetration testing services tailored to fulfill the internal and external pentesting requirements of your cardholder data environment outlined by the Payment Card Industry Data Security Standard (PCI DSS) v4.0. Our offerings are executed with comprehensive coverage and meticulous attention to detail to fully address these stringent pentesting requirements.
Autonomous Penetration Testing with Horizon3.ai
March 28, 2024
The NodeZero platform is easy-to-use, safe for production, and scales to support your largest networks. You are empowered to test a very broad scope in a single test, orchestrate tests concurrently, and simultaneously test your enterprise from different attacker perspectives.