Cutting Through the Noise: Security Insights by Horizon3.ai
SEARCH
CATEGORIES
TAGS
Shifting the Focus to Exploitability in CTEM and ASM
January 24, 2024
The Exploitable Attack Surface Keeps Expanding: Discover and Remediate Exploitable Vulnerabilities with NodeZero
Securing the Move: Cyber Resilience in the Transportation and Supply Chain Industry
January 23, 2024
Cyber protection is crucial for the transportation industry and the supply chain because it ensures the seamless flow of goods, prevents disruptions, and preserves the integrity of critical data essential for global commerce.
Five Key Outcomes of Continuous Security Assessments in Manufacturing
January 17, 2024
Manufacturers face an unprecedented array of challenges, from fierce competition to rapid technological advancements. Amid these shifts, ransomware threats have evolved into an imminent danger that can cripple manufacturers.
A Preemptive Approach to Defeat Ransomware in Healthcare
January 17, 2024
Healthcare organizations recognize they need a preemptive approach to help them discover their truly exploitable vulnerabilities, show them how to fix the issues at hand, then verify their fix worked. Discover the facts about how NodeZero is redefining healthcare security in our comprehensive whitepaper.
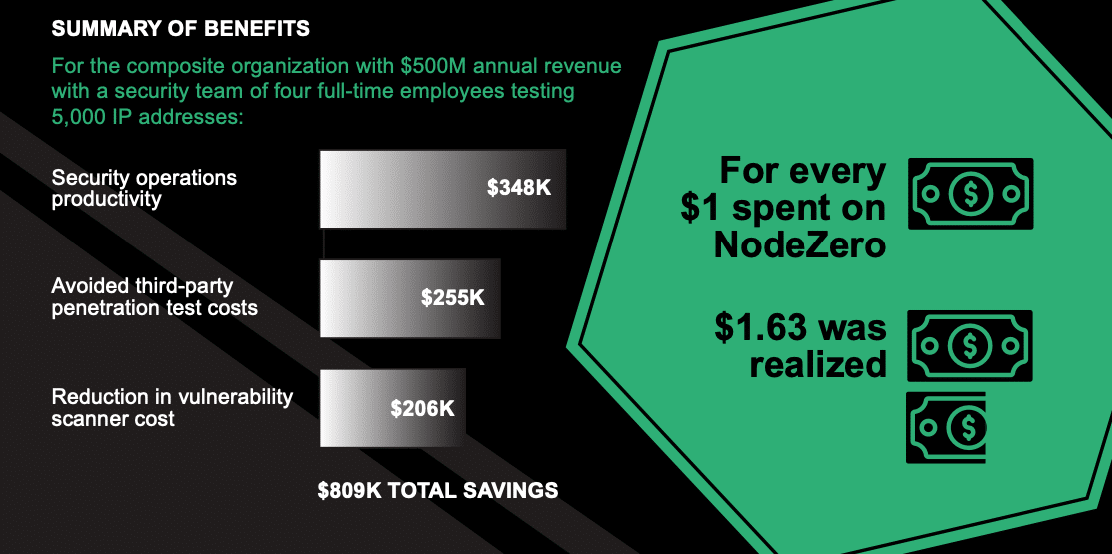
The Total Economic Impact™ Of The NodeZero™ Platform Infographic
January 10, 2024
The NodeZero™ platform helps organizations improve SecOps productivity and save on third-party pentest & vulnerability scanner costs. Learn how in the commissioned Forrester Consulting Total Economic Impact™ study. Download the Study
An Offensive Approach to Defeat Human-Operated Ransomware in Education
January 7, 2024
Educational institutions are treasure troves of valuable PII information, making them prime targets for ransomware attacks. It’s time for a paradigm shift. It’s time to go on the offensive.
Airiam: Turning Cyber Resilience into a Superpower
January 4, 2024
The first NodeZero demo was game-changing according to Airiam. “It looked amazing…it blew everything out of the water in comparison to other products.”...
Revolutionizing Cybersecurity: F12.net’s Journey with Autonomous Penetration Testing
January 3, 2024
How an MSSP Turned NodeZero into a High-Demand Service Offering
The Art Of Attack—Enhancing Defense Strategies: Unleashing The Power Of Autonomous Pen Testing | A Brand Story Conversation From Black Hat USA 2023 | An Horizon3.Ai Story With Snehal Antani
October 12, 2023
A Brand Story Conversation With Sean Martin And Snehal Antani, Co-Founder & CEO At Horizon3.ai
Enhancing Splunk Deployments with NodeZero
September 1, 2023
As security threats continue to evolve and become more sophisticated, the need for advanced security mechanisms and strategies has become paramount. Two technologies that stand out in this domain are the NodeZero platform and Splunk.