Pentesters
SEARCH
CATEGORIES
TAGS
Using NodeZero® to Uncover the Paths Attackers Take, Before They Do
May 2, 2025
Discover how NodeZero emulates real attackers to uncover critical attack paths, escalate access, and deliver proof—fast and autonomously.
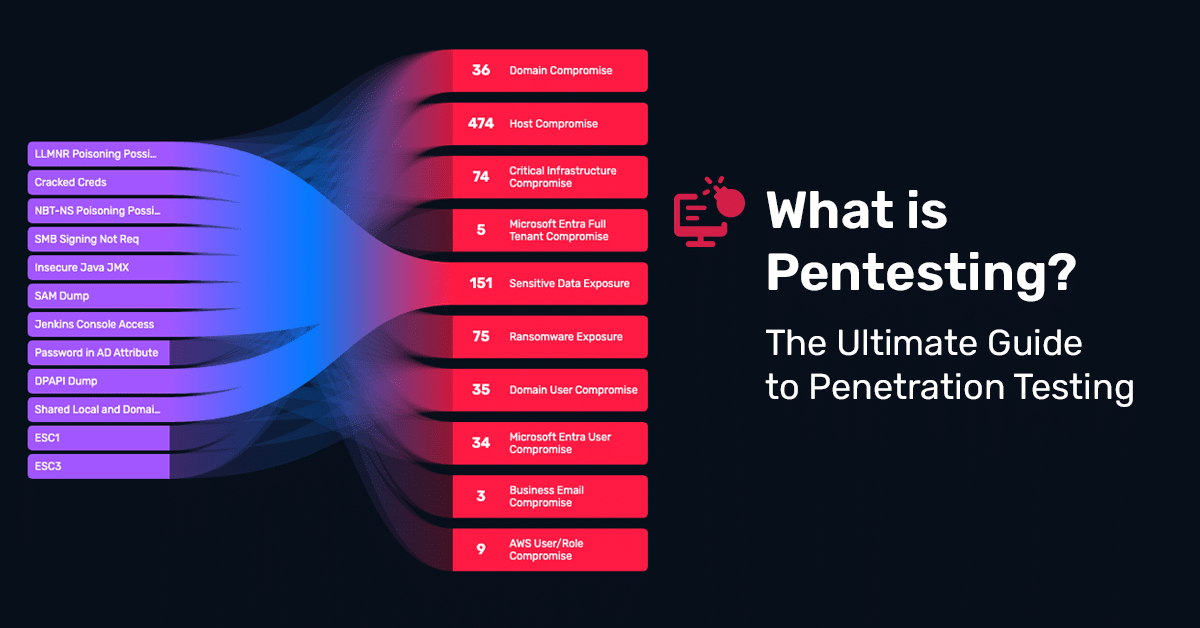
What Is Pentesting? The Ultimate Guide to Penetration Testing
April 30, 2025
Learn how pentesting goes beyond scans to validate real risk, meet compliance, and stay ahead of threats with Horizon3.ai’s ultimate guide.
Ivanti Endpoint Manager – Multiple Credential Coercion Vulnerabilities
February 19, 2025
Critical Ivanti Endpoint Manager vulnerabilities revealed—learn about CVE exploits and mitigation.
VMware vRealize Log Insight VMSA-2023-0001 Technical Deep Dive
January 31, 2023
Introduction The recent VMware VMSA describes four new CVEs affecting VMware vRealize Log Insight, reported by ZDI. Three of these CVEs can be combined to give an attacker remote code execution as root. This vulnerability is exploitable in the default configuration for VMware vRealize Log Insight. We have successfully reproduced this exploit and would like…
Metrics That Matter: An Attacker’s Perspective on Assessing Password Policy
December 1, 2022
After compromising a Windows domain controller, one of the actions that NodeZero, our autonomous pentest product, performs is dumping all domain user password hashes from the Active Directory database. This is a common attacker technique, and the resulting dump is highly valuable to attackers. But did you know that this data is a great source…
Verifying Credentialed Access to Your Hybrid Cloud Sprawl Matters More Than Ever
November 1, 2022
Verifying credentialed access to your hybrid cloud sprawl matters more than ever. See example attack paths to understand risks to AWS cloud.
The Undeniable Effectiveness of Password Spray
October 20, 2022
One of the most effective techniques NodeZero employs for initial access is password spray. It's a primitive technique, basically guessing passwords, and when it works it feels like magic. Yet we see it work time and time again in various pentests conducted by NodeZero. In this post we'll talk about what password spray is and…
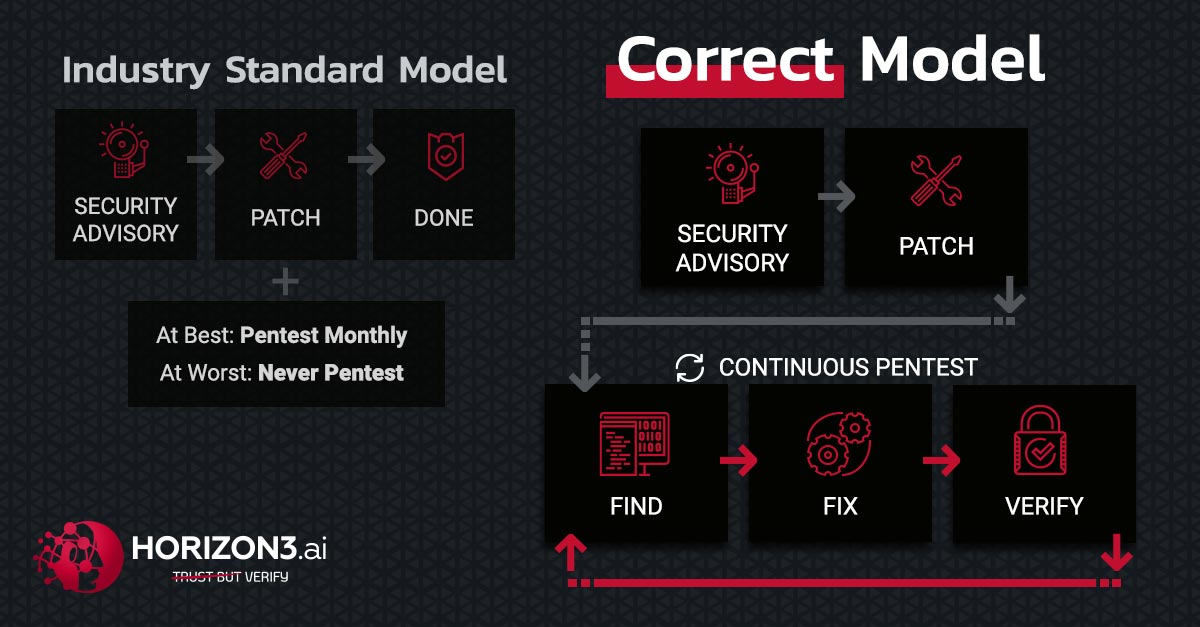
The Industry Standard Model is the Vulnerability
February 11, 2022
Which is more valuable to you; the ability to identify a problem, or the ability to solve the problem? There is a plethora of vulnerability scanning tools that do a decent job identifying vulnerabilities. Unfortunately, those tools rarely discern the possible from the exploitable.
Hack The Box – Mirai
December 6, 2021
NodeZero compromised HTB’s Mirai machine by using default SSH creds for user pi, then escalated to root via unrestricted sudo access—gaining full control.
Hack The Box – Jerry
September 16, 2021
The Jerry machine from the Hack The Box platform nicely illustrates the danger of weak and default credentials.