Don’t Chase Vulnerabilities. Manage Exploitable Risks.
Move beyond endless patch lists to risk-based security that keeps attackers out.
See a Demo





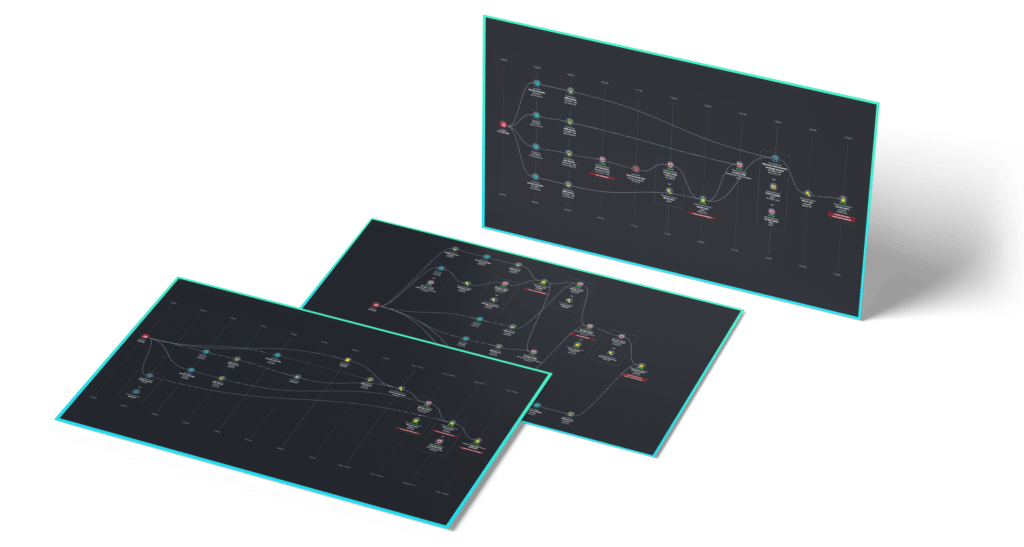
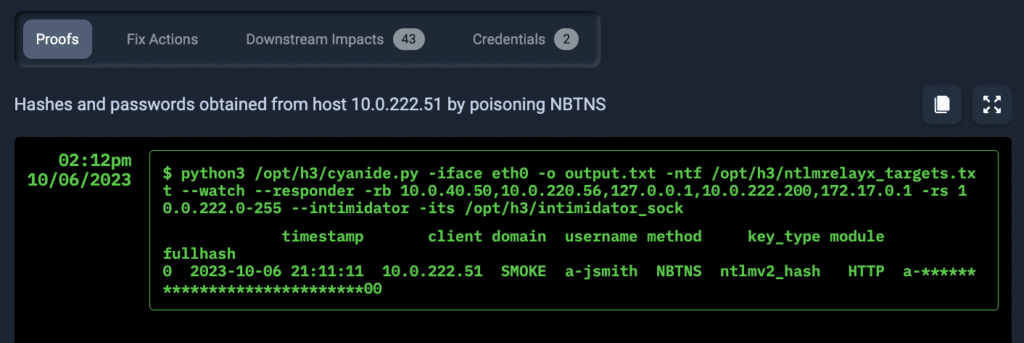
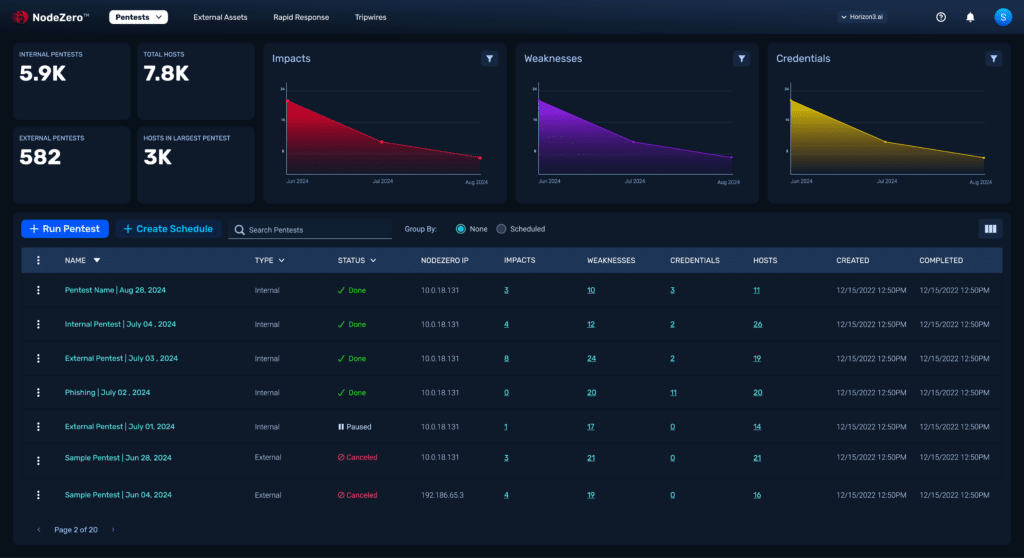
Avoid False Positives with Clear Attack Paths and Proof of Exploits
NodeZero® chains together misconfigurations, dangerous product defaults, exploitable CVEs, ineffective security controls, and harvested credentials across hosts into an easy-to-understand attack path. It provides proof-of-exploit, showing exactly how an attacker can compromise your system.
Save Time with Prioritized Remediation Guidance and 1-Click Retesting
Prioritized impacts show what to fix first and how to do it efficiently. Save time with detailed remediation guidance and a Fix Action report, highlighting fixes that solve the most issues for maximum return on effort. After remediation, use 1-Click Verify to ensure your fixes are effective.

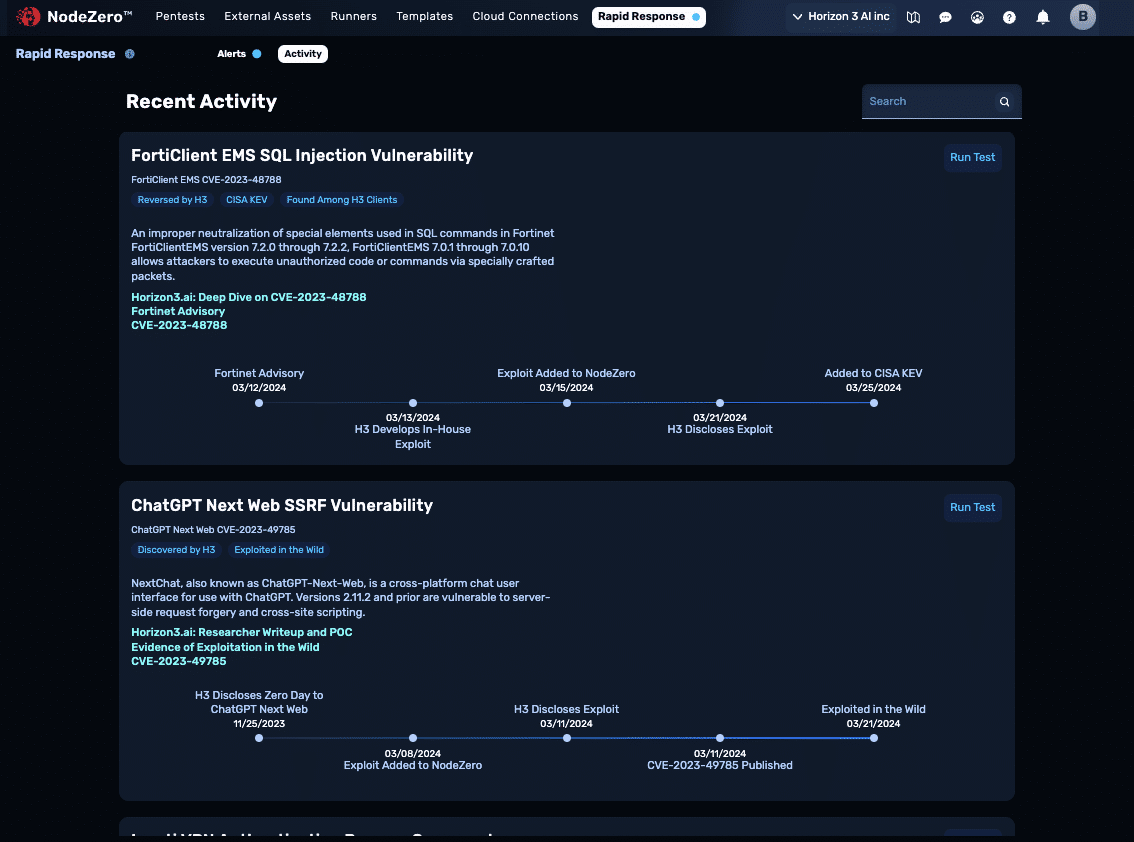
Get Ahead of Emerging Threats
With Nodezero’s Rapid Response™ testing begin finding, fixing, and verifying N-day vulnerabilities in your environment before they are widely exploited. If the Horizon3.ai team discovers a zero day, you will be notified PRIOR to public disclosure if your environment is impacted.
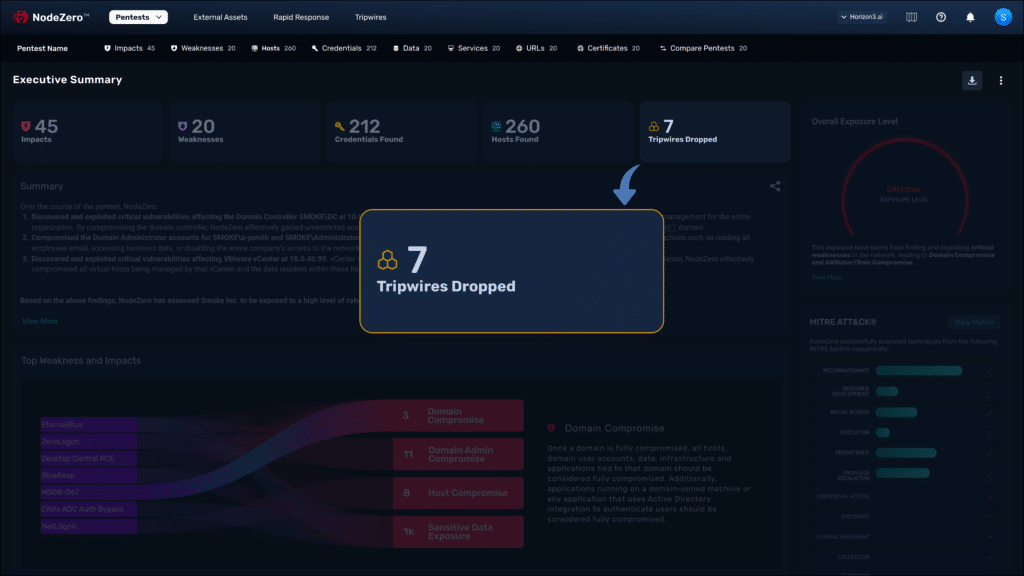
Auto Deploy Tripwires
NodeZero Tripwires™ will automatically deploy decoys—such as fake files and fake credentials—on hosts and fileshares that NodeZero successfully compromised during an autonomous pentest, creating an early warning network for your exploitable attack surface.
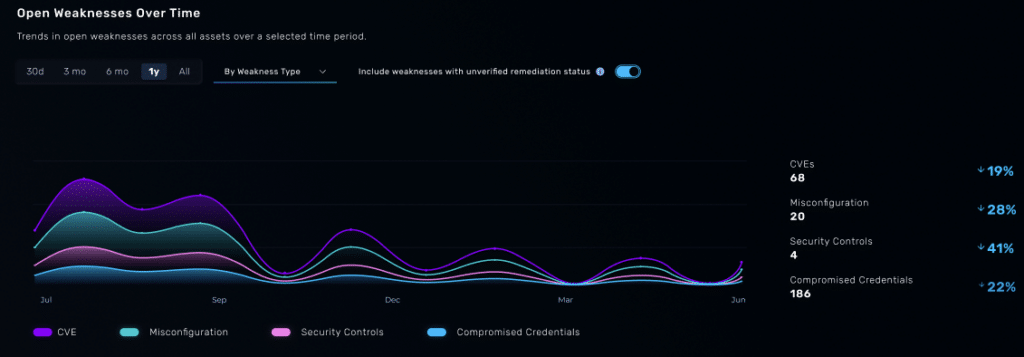
Improve your Posture Over Time
With each pentest, NodeZero learns, adapts, and enhances its capabilities—continuously evolving to provide sharper insights into your vulnerabilities. By comparing past and present results, you can track your security posture over time, identify trends, and make data-driven improvements.
Discover how Horizon3.ai's NodeZero platform can help you find and fix exploitable weaknesses before attackers do.
Request your personalized demo today and see how autonomous pentesting can strengthen your security posture.