Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
From Patch Tuesday to Pentest Wednesday®: Proof That Protects Healthcare
August 20, 2025
A Pentest Wednesday® Story Every security leader knows about Patch Tuesday. It’s the rhythm Microsoft set decades ago to deliver updates and fixes, and it quickly became a mainstay of IT and security operations. Teams plan change-windows around it. Vendors align updates to it. And for many organizations, Patch Tuesday has become the de facto…
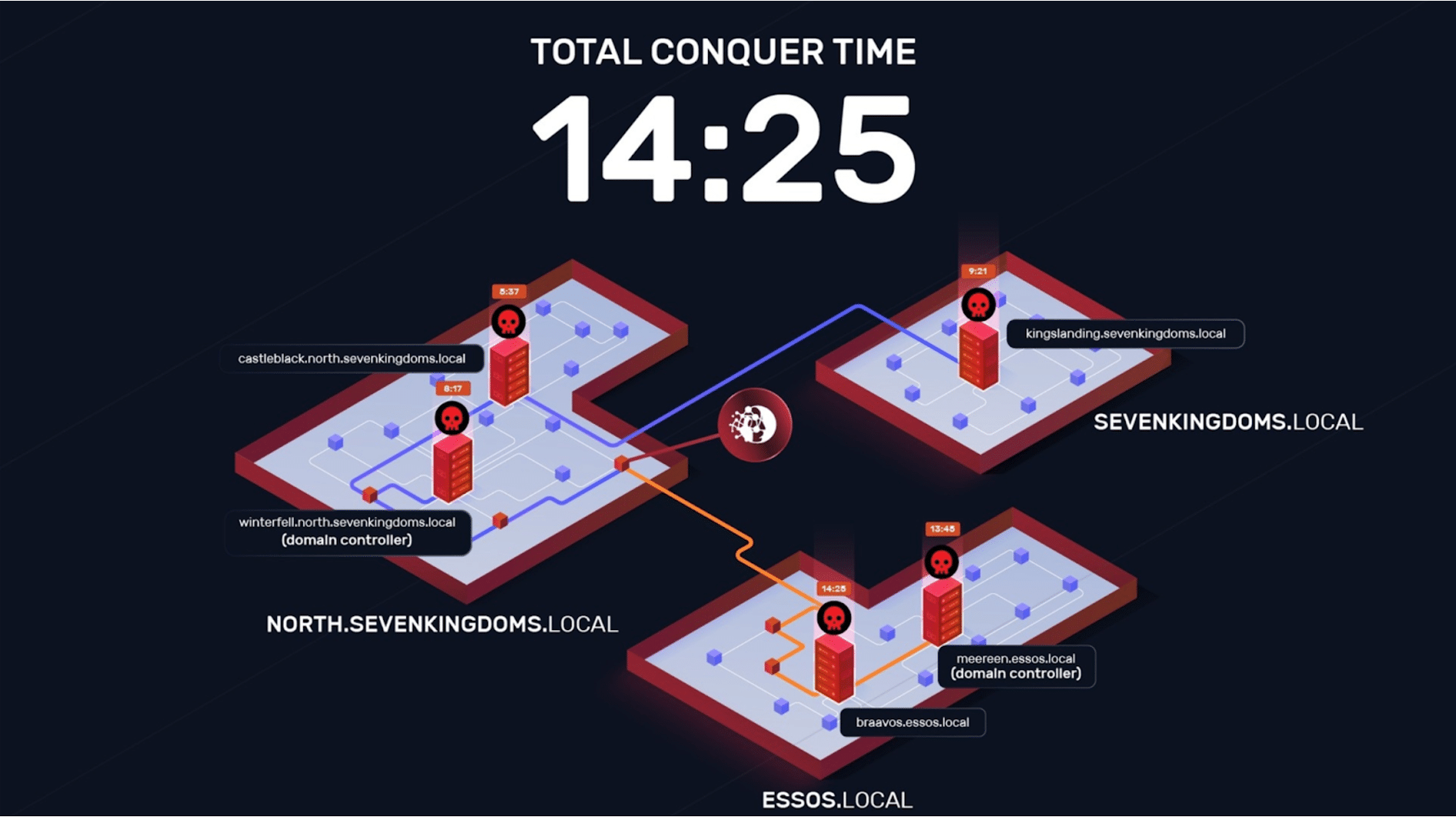
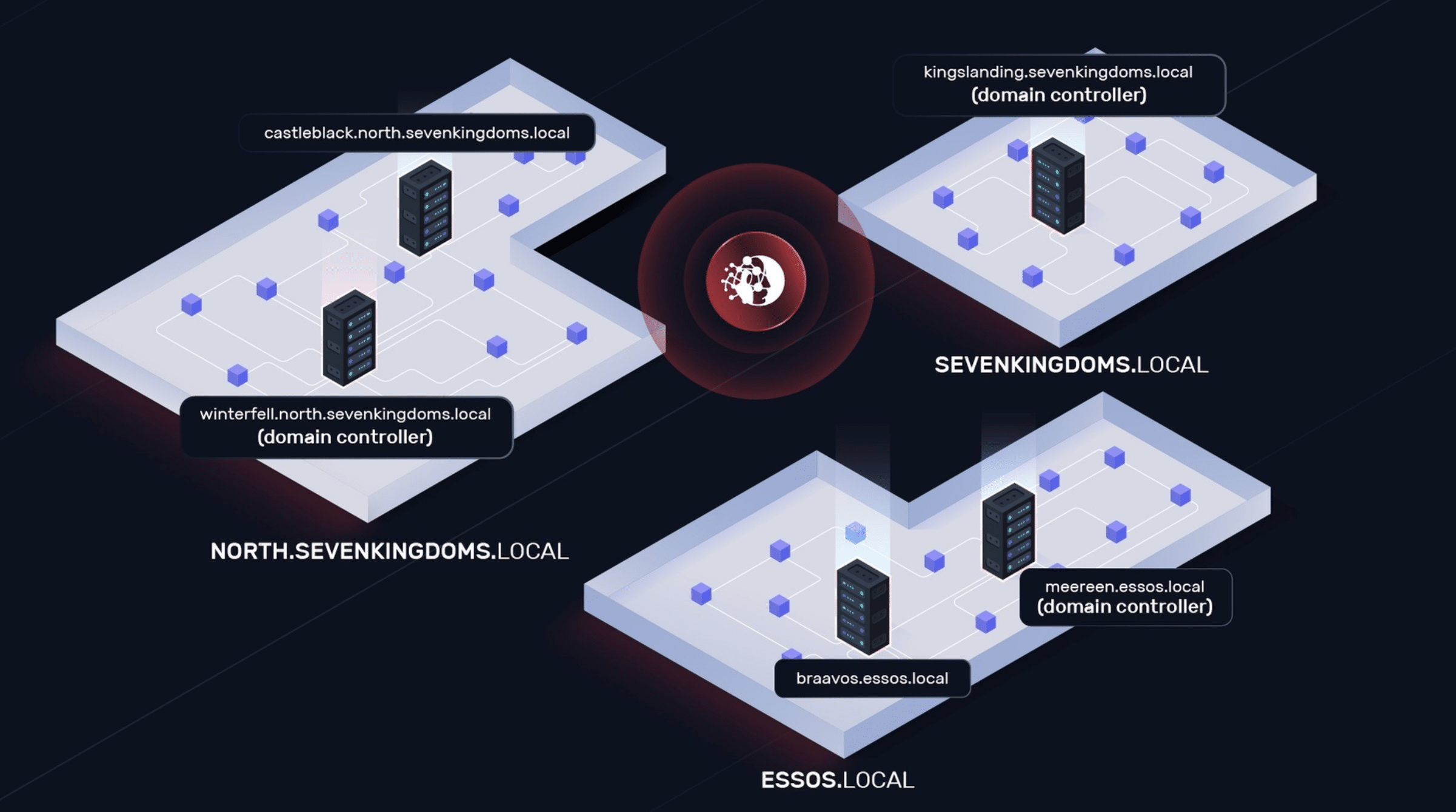
NodeZero® vs. GOAD: Technical Deep Dive
NodeZero autonomously compromised GOAD in 14 mins by exploiting common Active Directory misconfigurations.
How to Run NodeZero® vs. GOAD
GOAD (Game Of Active Directory) is an intentionally vulnerable cyber range used by pentesters and defenders to explore common attack techniques in a Windows Active Directory environment. It's chock full of real-world misconfigurations and vulnerabilites, the type we see all the time in client environments. As such, it's a great way to understand the capabilities…
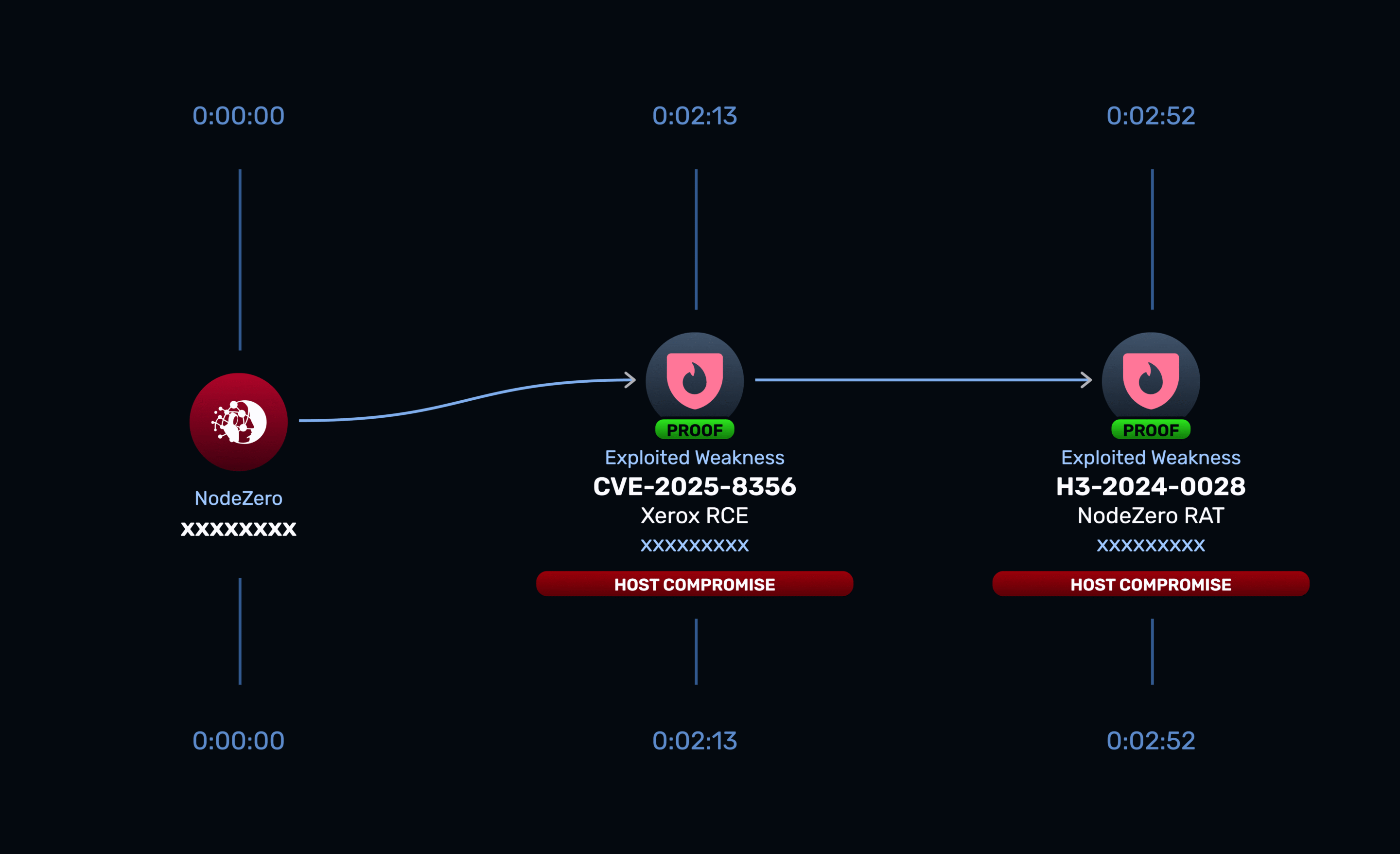
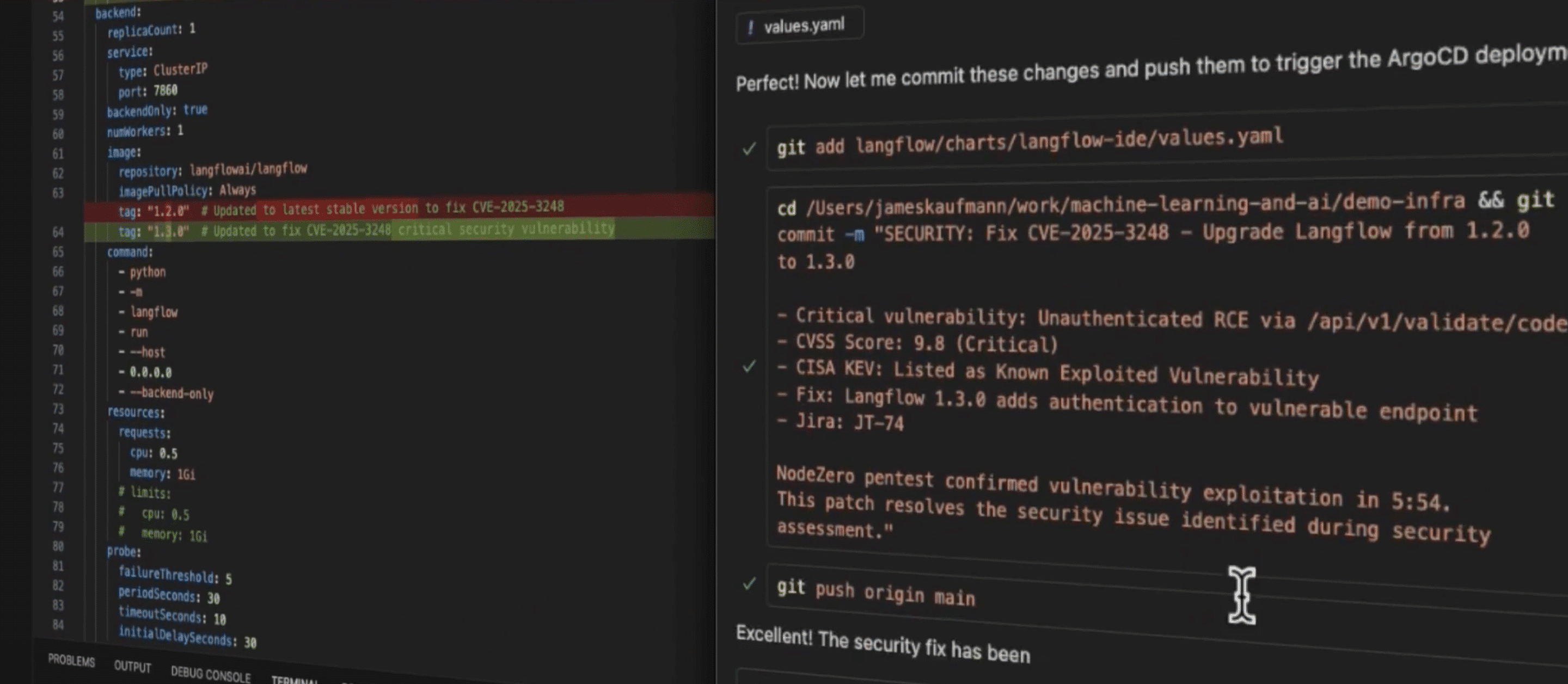
From Support Ticket to Zero Day
August 13, 2025
Examining a Critical Vulnerability in Xerox FreeFlow Core
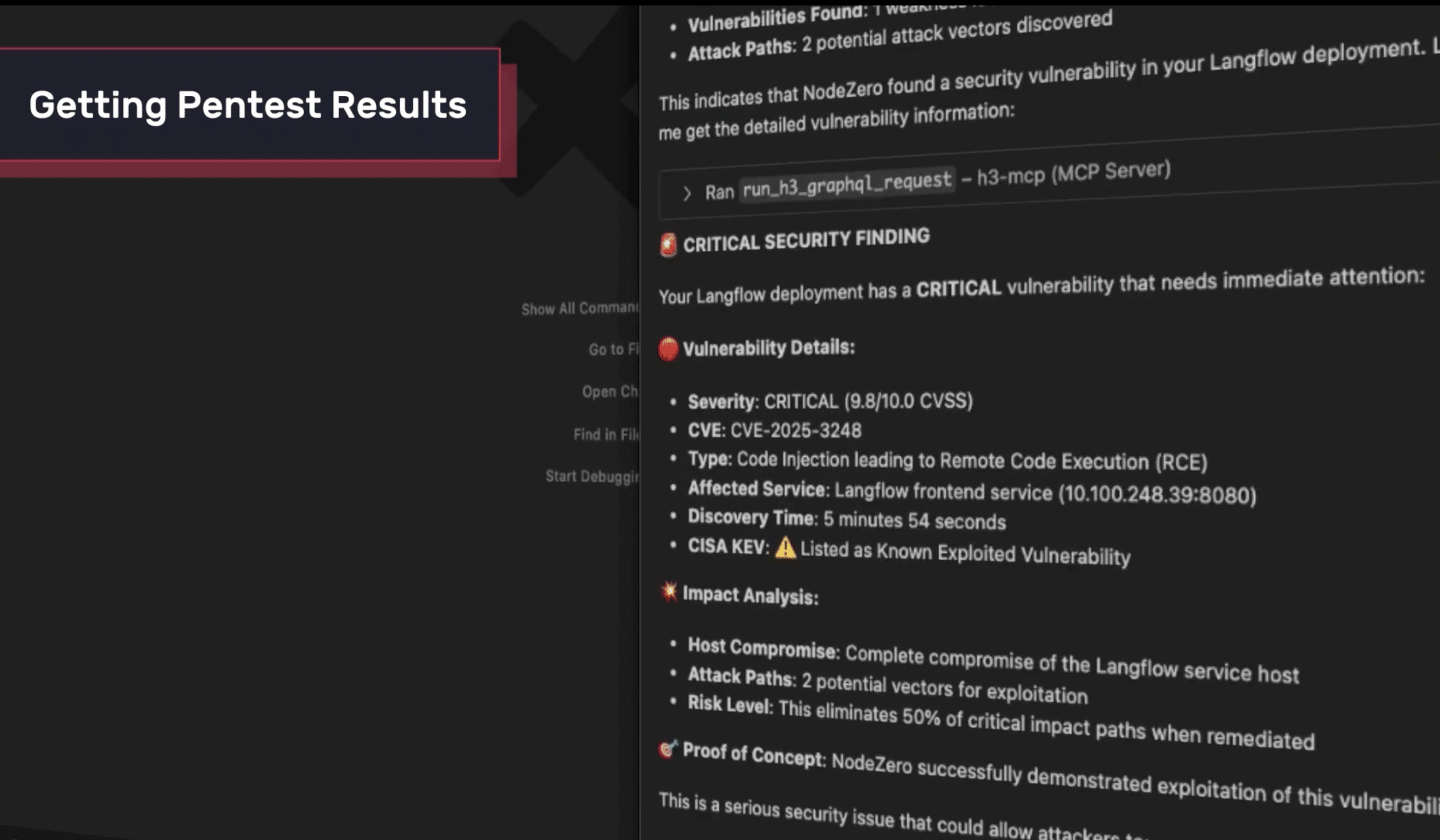
Supercharge Enterprise AI with the Attacker’s Perspective: Introducing the NodeZero® MCP Server
Enterprises are racing to harness AI to automate workflows, secure infrastructure, and accelerate decision-making. But here’s the uncomfortable truth: AI that doesn’t see your environment through an attacker’s eyes is operating blind.
Securing the NodeZero® MCP Server: Building a Safe, Agent-Ready Runtime for Enterprises
When we set out to build the first version of the NodeZero MCP Server, we had two guiding principles: Most Model Context Protocol (MCP) servers today are overpowered and underdefended. They often: We didn’t build ours that way. The NodeZero MCP Server is a constrained, API-native runtime designed to give agents safe, structured access to…
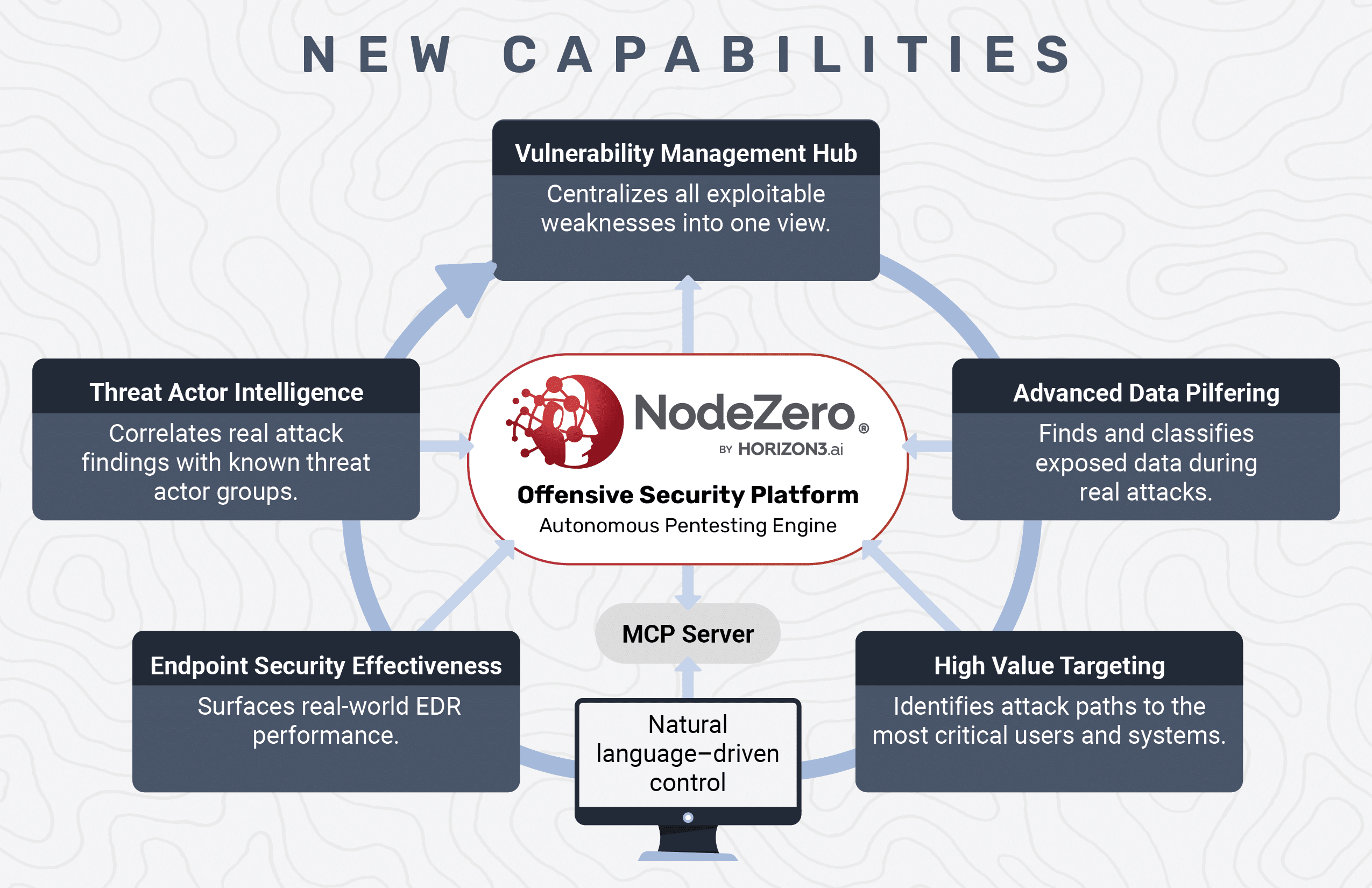
Fix What Matters Most: Six New NodeZero® Capabilities That Redefine Risk-Based Vulnerability Management
Vulnerability management started with scanning — identify assets, fingerprint software, and match scan findings to known CVEs. Then came “risk-based” approaches that promised smarter prioritization. But in practice, most programs still just patch what scores the highest. Risk is inferred, not proven. Fixes are assumed to work. And security teams are left guessing what actually…
Vulnerability Management Is Broken: There is a Better Way
July 28, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Unlocking Next-Level Security with Horizon3.ai & Optiv
Horizon3.ai and Optiv lead the charge in the ever-evolving, innovation demanding field of cybersecurity. Find out how in this webinar.
CVE-2025-5777: CitrixBleed 2 Write-Up… Maybe?
July 7, 2025
Background and Confusion On June 17, 2025, Citrix published an advisory detailing CVE-2025-5777 and CVE-2025-5349. Affected products include: On June 25, 2025, they also published an advisory detailing CVE-2025-6543. Affected products include: Of the three vulnerabilities, two of them have been receiving a bit of buzz: While we’ve developed a working exploit for one of…