Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
How Horizon3.ai is Supporting the DoW Cybersecurity Risk Management Construct (CSRMC)
December 17, 2025
The DoW’s new Cybersecurity Risk Management Construct demands continuous, evidence-driven security. Learn how Horizon3.ai’s NodeZero delivers real-time, attacker-validated proof to support mission resilience.
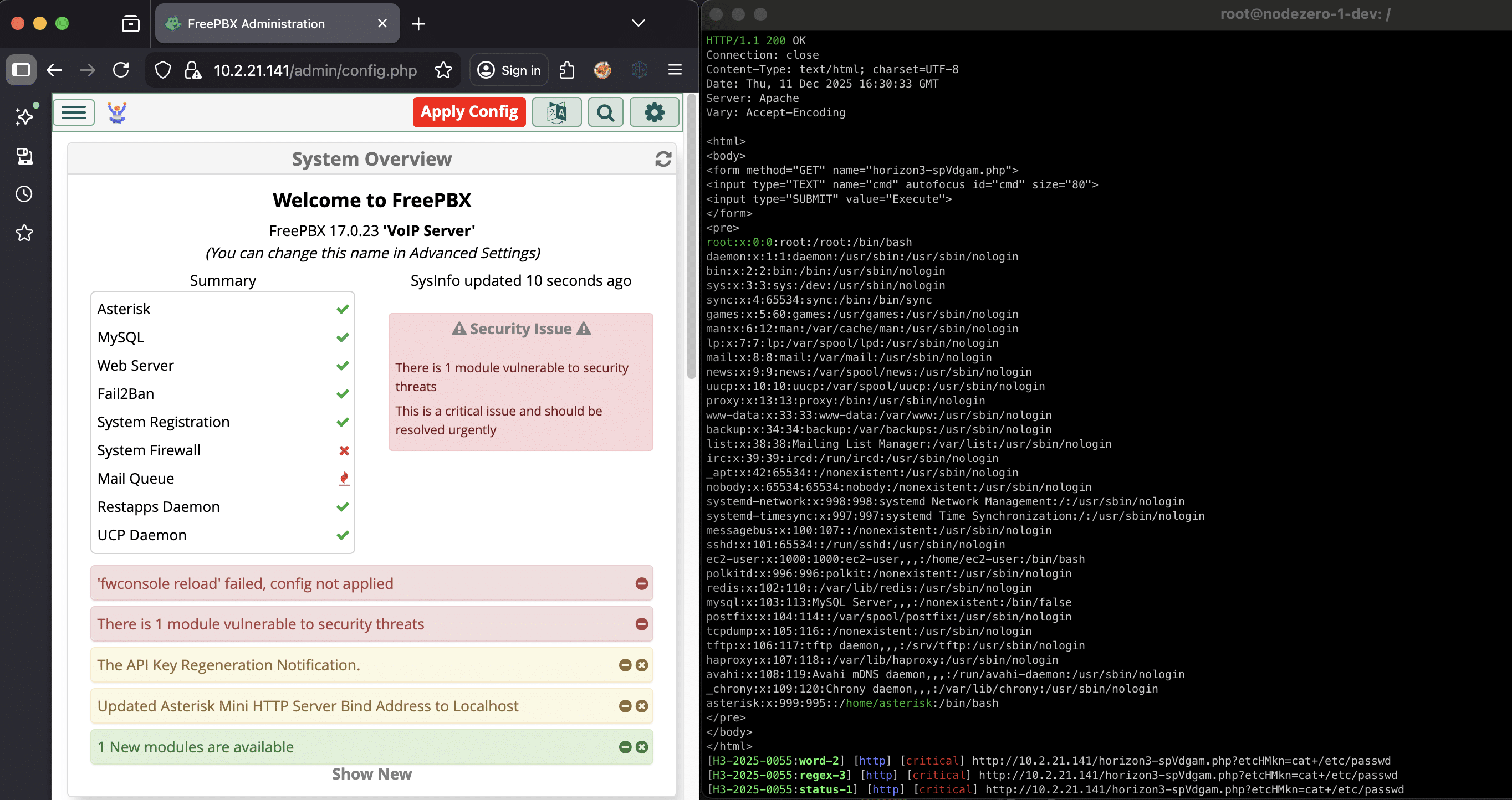
The FreePBX Rabbit Hole: CVE-2025-66039 and others
December 11, 2025
We dive into a new set of FreePBX issues beyond CVE-2025-57819: an authentication bypass in webserver mode (CVE-2025-66039), multiple SQL injections (CVE-2025-61675), and an arbitrary file upload bug leading to remote code execution (CVE-2025-61678). Together, they allow authenticated or unauthenticated attackers to achieve code execution on vulnerable FreePBX instances using risky auth settings. This write-up…
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for a Manufacturer
December 10, 2025
Patch Tuesday is a known event, but attackers are moving faster than ever. For a leading U.S. manufacturer, shifting from simple patching to continuous validation became the key to proving their fixes worked, turning uncertainty into confidence.
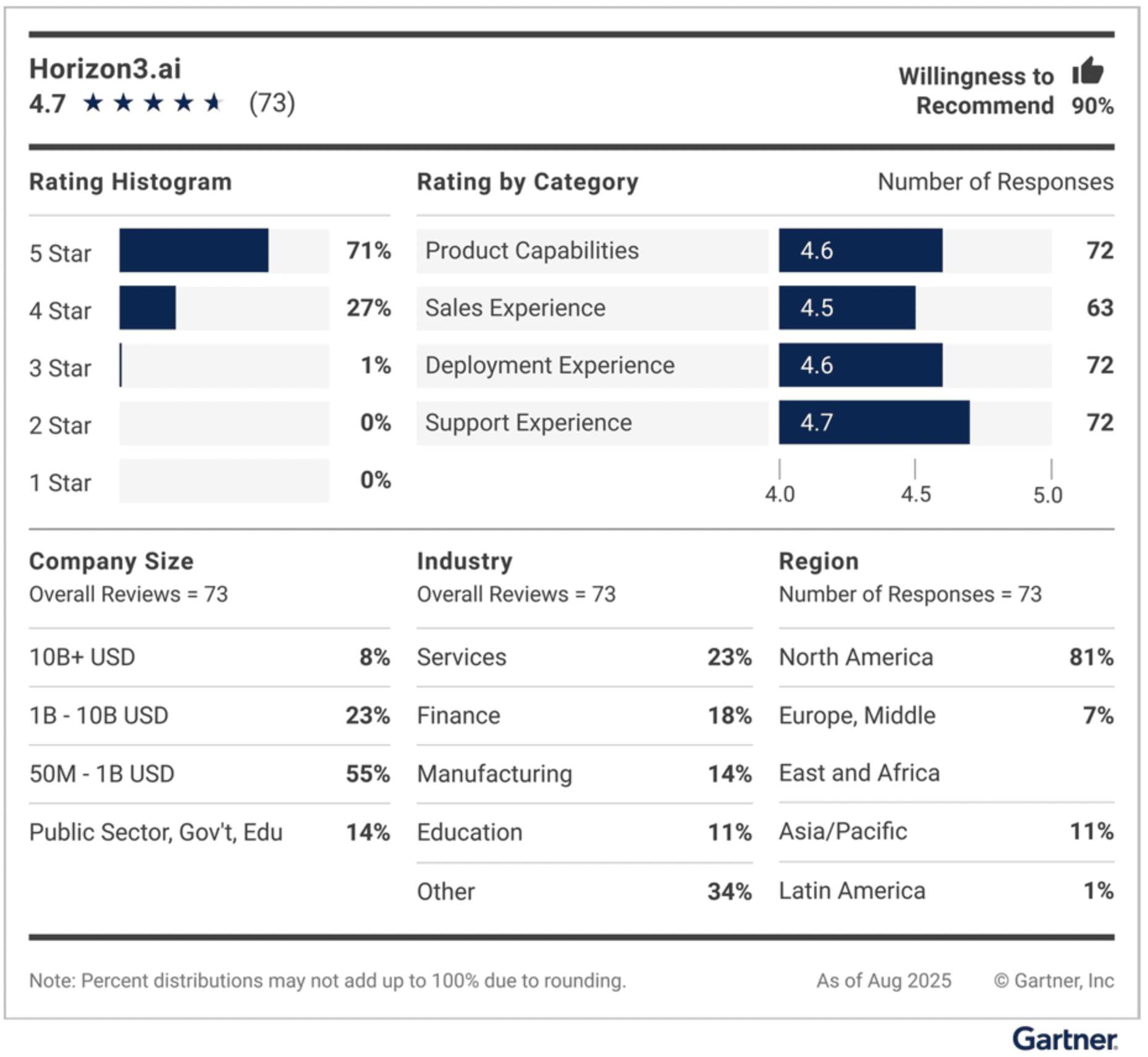
Horizon3.ai is named a Customer’s Choice in the October 2025 Gartner® Peer Insights™ “Voice of the Customer”: Adversarial Exposure Validation report
December 4, 2025
Horizon3.ai has been named a Customers’ Choice in the October 2025 Gartner® Peer Insights™ “Voice of the Customer”: Adversarial Exposure Validation report, reflecting strong peer satisfaction and real-world impact.
Introducing Threat Informed Perspectives: A More Strategic Way to Measure Security Posture
Threat Informed Perspectives give organizations a structured, attacker-aligned way to measure exposure, track real security improvement, and validate remediation over time using continuous, evidence-driven insights from NodeZero.
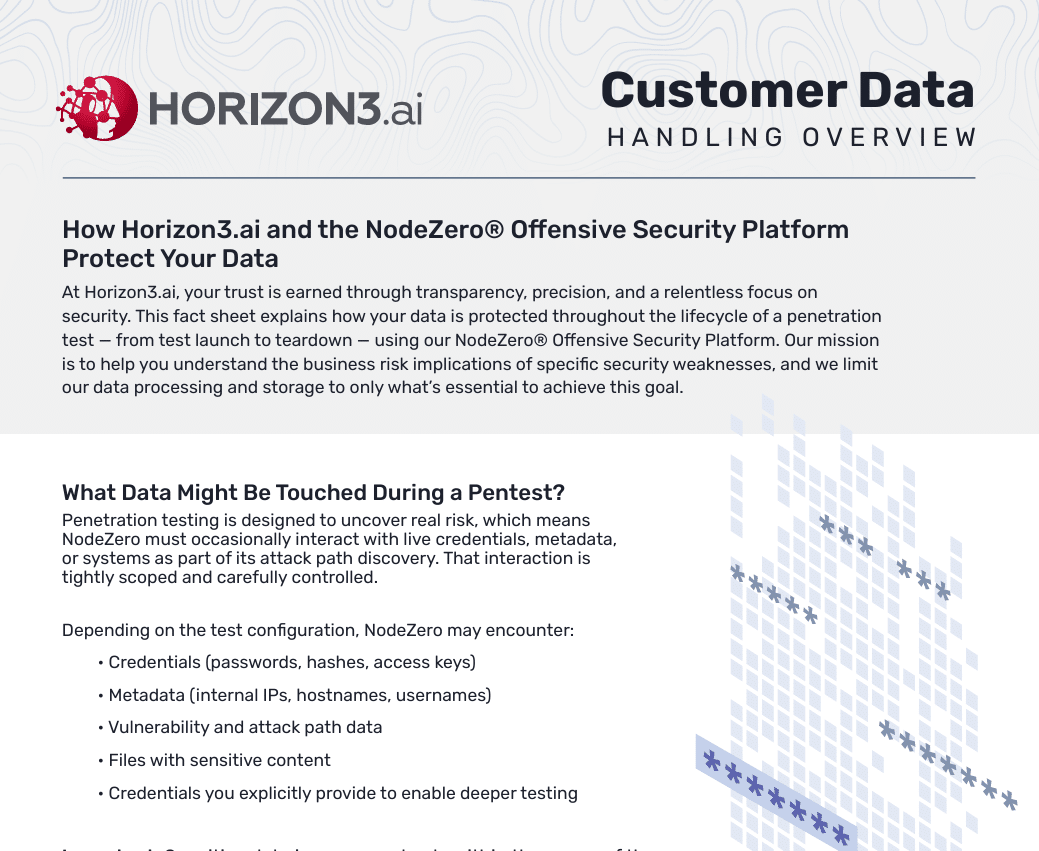
Customer Data Handling Factsheet
November 25, 2025
At Horizon3.ai, transparency and security go hand in hand. The NodeZero® Offensive Security Platform protects your data during every test — encrypting communications, limiting retention, and ensuring no sensitive data leaves your environment. Download the factsheet to see how our strict controls safeguard customer information from launch to teardown.
Endpoint Detection and Response: What It Is and How to Know Yours Is Working
November 24, 2025
EDR tools offer visibility, but visibility isn’t protection. Learn why credential-driven attacks often bypass EDR and how NodeZero validates real-world detection, blocking, and effectiveness across your endpoints.
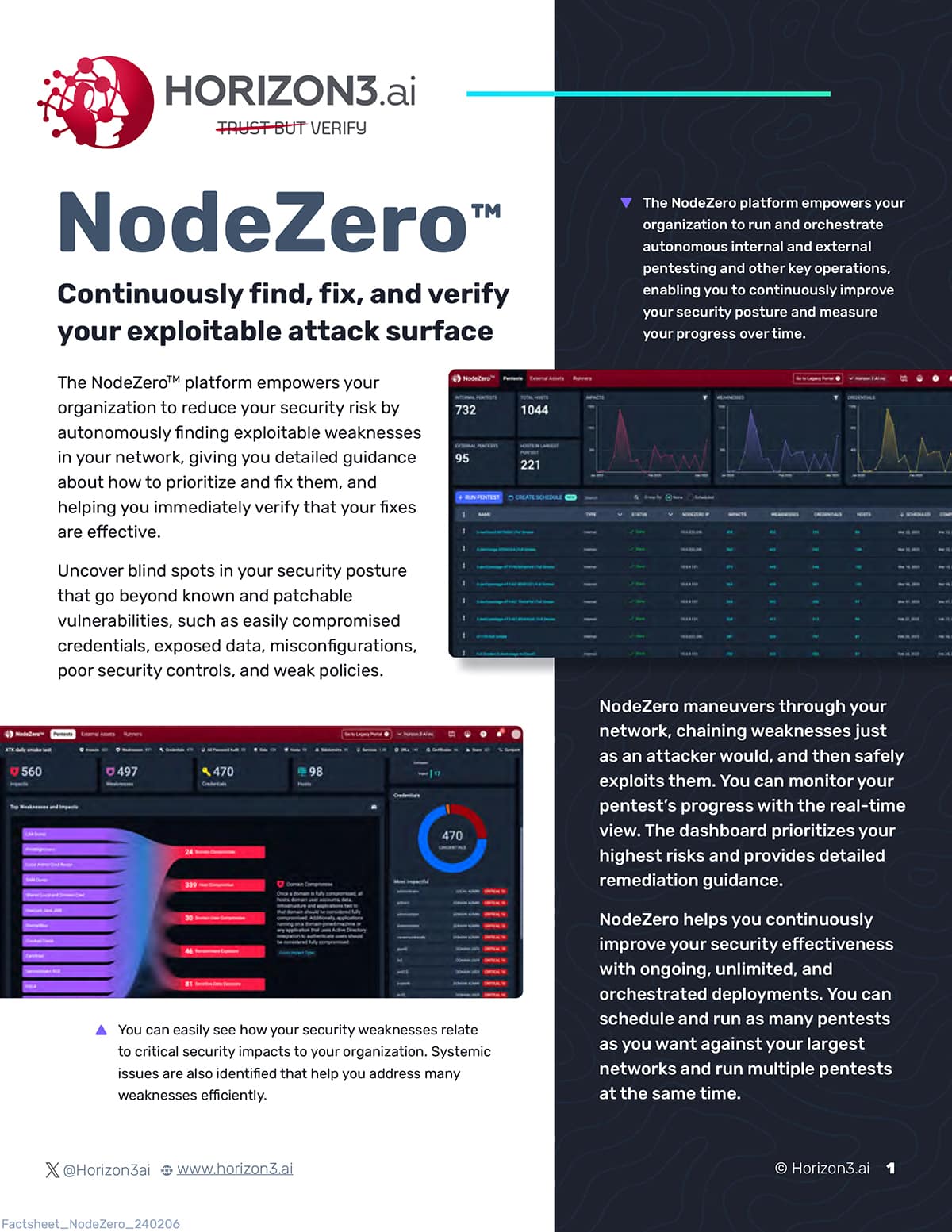
NodeZero Fact Sheet
November 24, 2025
The NodeZero platform empowers your organization to reduce your security risk by autonomously finding exploitable weaknesses in your network, giving you detailed guidance about how to prioritize and fix them, and helping you immediately verify that your fixes are effective.
Supercharging Enterprise AI with Real-World Exploitability Data: The NodeZero MCP Server Advantage
Learn how the NodeZero MCP Server supercharges enterprise AI ecosystems with attacker-validated exploitability data, continuous validation, and automated security workflows.
Prioritize What’s Proven: The NodeZero® Approach to Risk‑Based Vulnerability Management
November 18, 2025
Horizon3.ai’s NodeZero® redefines Risk-Based Vulnerability Management by connecting exploitability, business context, and attacker behavior. With new capabilities for High-Value Targeting, Advanced Data Pilfering, Threat Actor Intelligence, and Vulnerability Risk Intelligence, NodeZero moves vulnerability management from noise to proof—helping security teams prioritize, fix, and verify what truly matters.