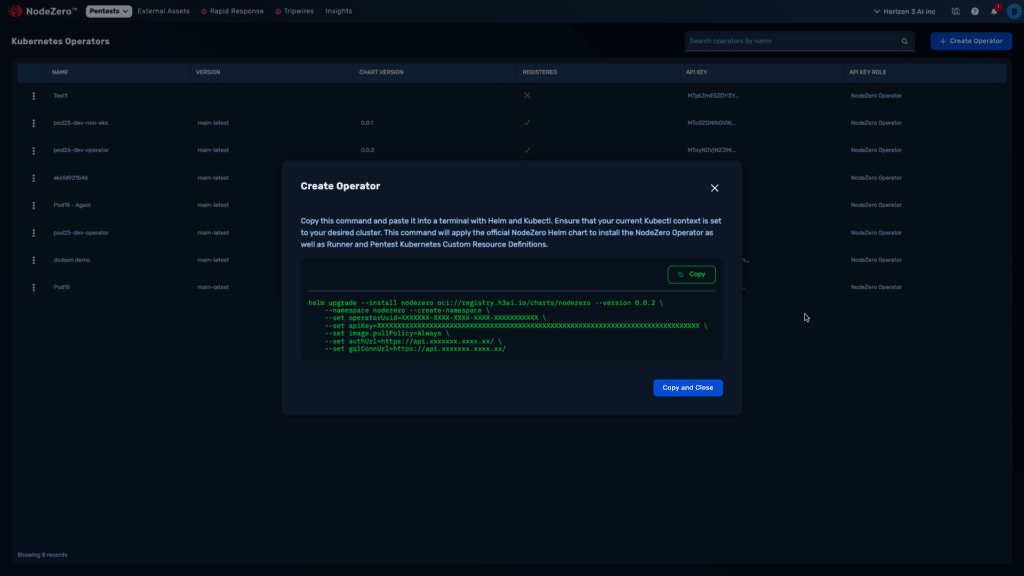
Kubernetes Pentesting
with NodeZero®
The NodeZero® platform autonomously pentests your Kubernetes clusters, continuously identifies risks, and exposes exploitable vulnerabilities like RBAC misconfigurations, container escapes, and secret exposures.
Kubernetes has become the mainstay of cloud infrastructure, but its complexity brings significant security risks. Each distribution, managed or not, – AWS EKS, Google GKE, Azure AKS, or vanilla Kubernetes – introduces unique vulnerabilities that attackers can exploit.
of organizations are either using or evaluating Kubernetes
Continuous Kubernetes Testing
Runtime Security Testing
Proactive Threat Identification

Cross-platform Attack Chaining
Ready to connect with Horizon3.ai?
Submit the form below.