Blogs
SEARCH
CATEGORIES
TAGS
Vulnerability Management Is Broken: There is a Better Way
July 28, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Vulnerable vs. Exploitable: Why Understanding the Difference Matters to Your Security Posture
June 25, 2025
Scanning and patching aren't enough. Learn the critical difference between being vulnerable and being exploitable—and why it's the key to preventing real-world breaches.
Achieving FedRAMP® High: What It Means and Why It Matters
June 23, 2025
NodeZero Federal™️ is now FedRAMP High Authorized—bringing trusted, autonomous pentesting to high-impact federal and compliance-driven environments.
What is Offensive Security?
June 20, 2025
Explore the evolution, tools, and tactics of offensive security—from early pentests to modern adversary emulation and Zero Trust validation.
Horizon3.ai Raises $100M to Cement Leadership in Autonomous Security
June 12, 2025
Rewriting Cybersecurity Rules. Led by veterans and ethical hackers, Horizon3.ai's NodeZero platform is transforming how organizations defend against threats.
Using NodeZero® to Uncover the Paths Attackers Take, Before They Do
May 2, 2025
Discover how NodeZero emulates real attackers to uncover critical attack paths, escalate access, and deliver proof—fast and autonomously.
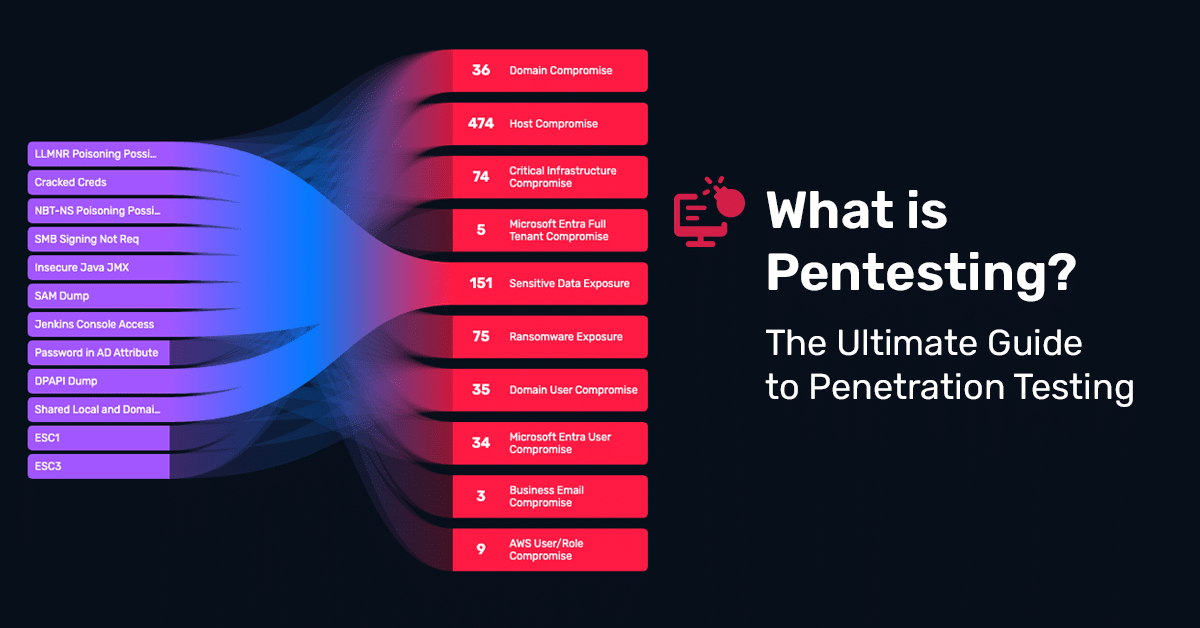
What Is Pentesting? The Ultimate Guide to Penetration Testing
April 30, 2025
Learn how pentesting goes beyond scans to validate real risk, meet compliance, and stay ahead of threats with Horizon3.ai’s ultimate guide.
The Duty to Know: Why Security Leaders Can’t Afford Ignorance
April 28, 2025
Security leaders can’t afford blind spots. Learn why proving security effectiveness is now a must—and how to meet the Duty to Know.
Why Adversarial Exposure Validation Belongs in Every CTEM Program
April 24, 2025
Discover why Adversarial Exposure Validation (AEV) is essential to any CTEM program. Learn how continuous, automated validation strengthens security, boosts red teaming, and proves real-world risk reduction.
NodeZero® Release Recap: Spring Edition
April 7, 2025
Spring updates are here! Explore NodeZero’s latest threat detection, pentest, and insights features—built to stay ahead of attackers.