Cutting Through the Noise: Security Insights by Naveen Sunkavally
SEARCH
CATEGORIES
TAGS
Ticket to Shell: Exploiting PHP Filters and CNEXT in osTicket (CVE-2026-22200)
January 22, 2026
CVE-2026-22200 is a severe vulnerability affecting osTicket, a popular open source helpdesk and ticketing system. This vulnerability enables anonymous attackers to read arbitrary files from the osTicket server, and in some cases execute arbitrary code. This issue is patched in osTicket 1.18.3 / 1.17.7.
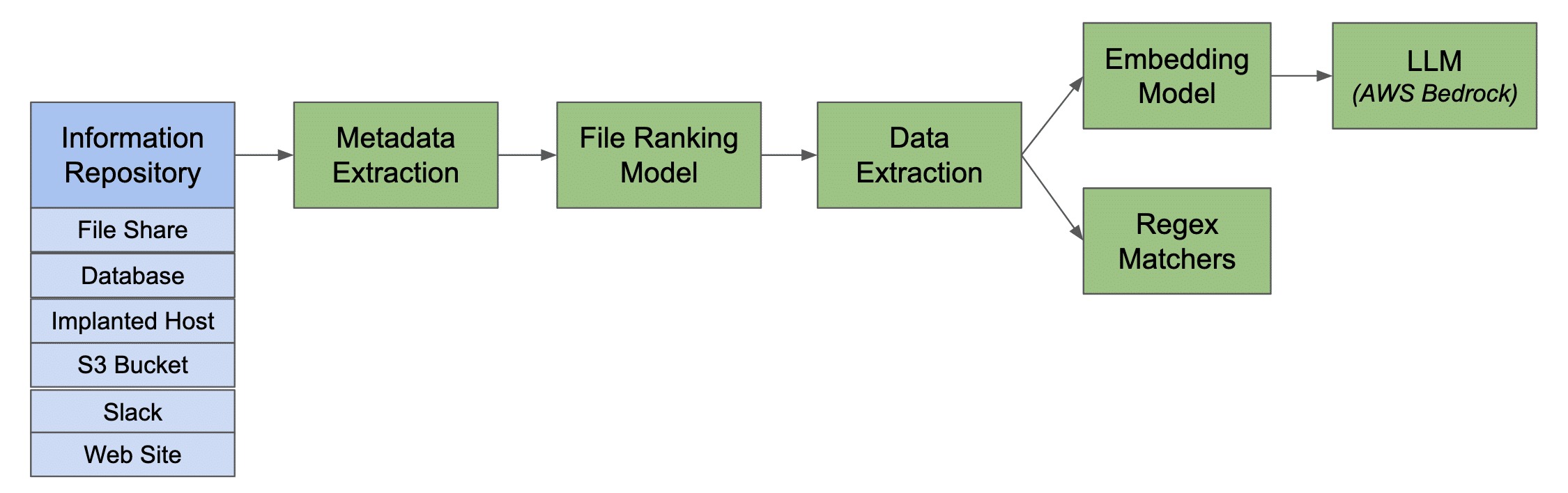
Introducing NodeZero® Advanced Data Pilfering: View Your Data Through the Eyes of an Attacker
NodeZero’s Advanced Data Pilfering uses LLMs to find hidden credentials and classify compromised files—revealing attacker paths and the real business risk in unstructured data.
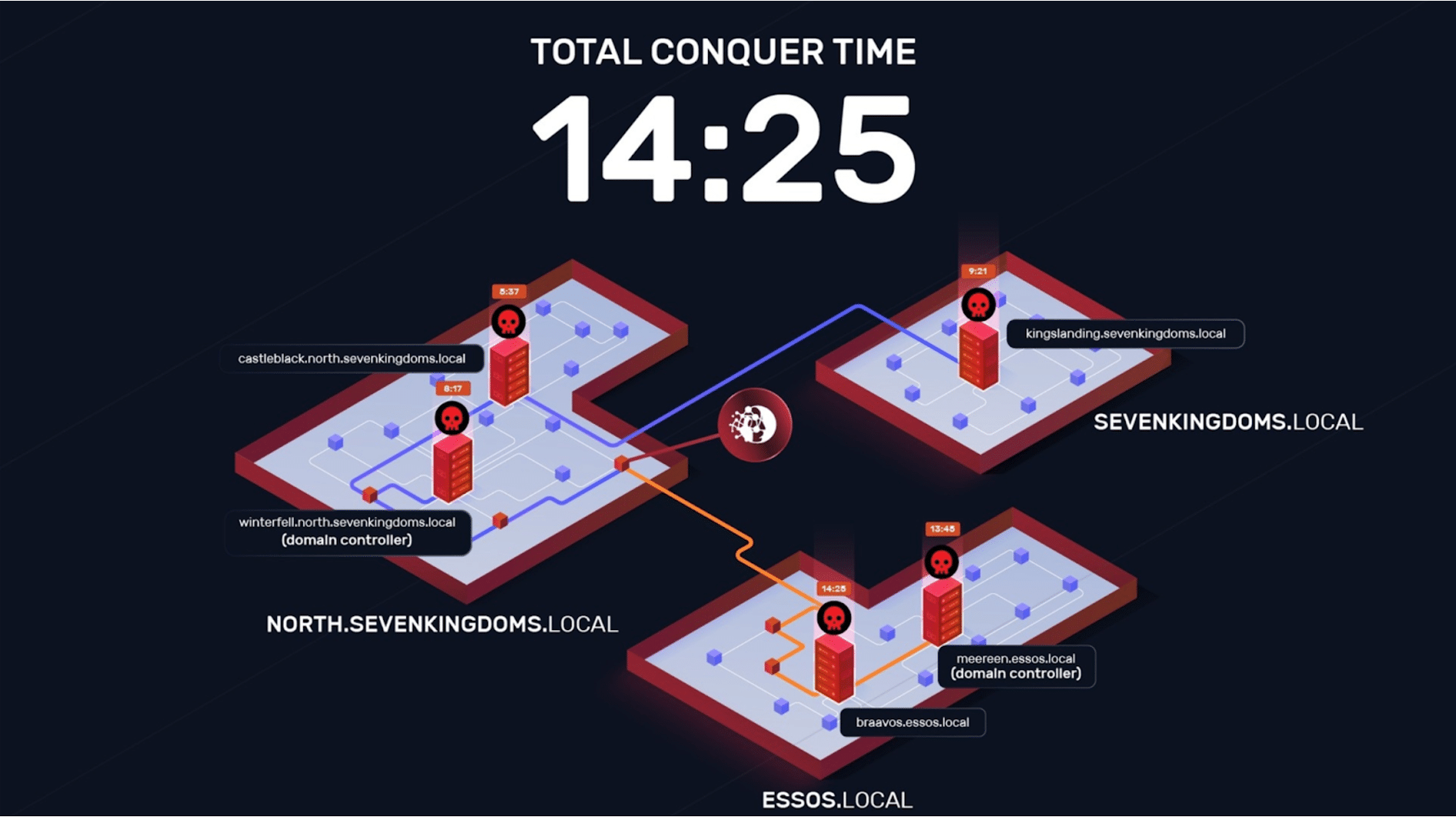
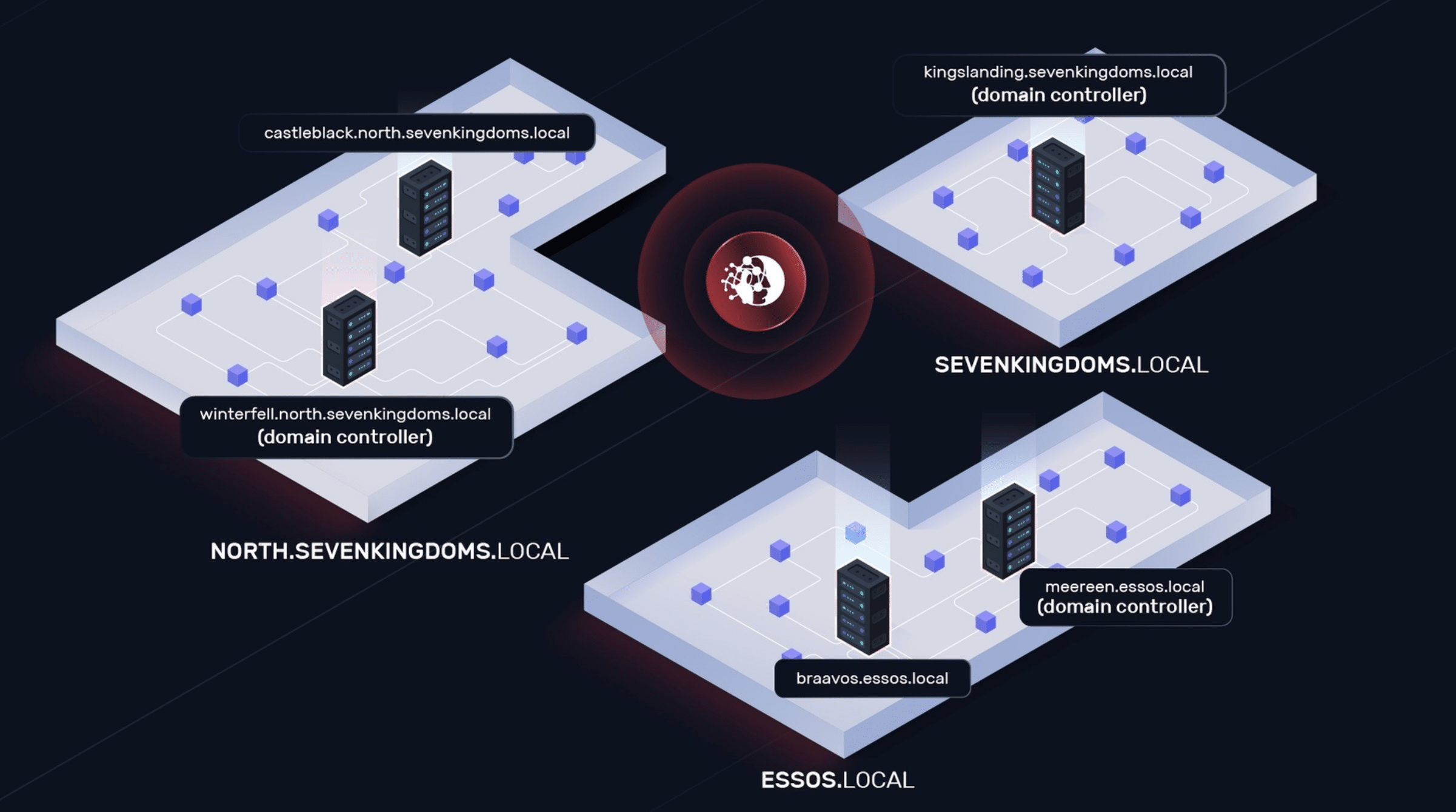
NodeZero® vs. GOAD: Technical Deep Dive
NodeZero autonomously compromised GOAD in 14 mins by exploiting common Active Directory misconfigurations.
How to Run NodeZero® vs. GOAD
GOAD (Game Of Active Directory) is an intentionally vulnerable cyber range used by pentesters and defenders to explore common attack techniques in a Windows Active Directory environment. It's chock full of real-world misconfigurations and vulnerabilites, the type we see all the time in client environments. As such, it's a great way to understand the capabilities…
Unsafe at Any Speed: Abusing Python Exec for Unauth RCE in Langflow AI
April 9, 2025
CVE-2025-3248 is a critical code injection vulnerability affecting Langflow, a popular tool used for building out agentic AI workflows. This vulnerability is easily exploitable and enables unauthenticated remote attackers to fully compromise Langflow servers. The issue is patched in Langflow 1.3.0.
Critical Vulnerabilities in SimpleHelp Remote Support Software
January 13, 2025
SimpleHelp remote support software is susceptible to critical vulnerabilities that could allow full takeover of SimpleHelp servers. Users of SimpleHelp should upgrade to the latest version ASAP.
NTLM Credential Theft in Python Windows Applications
August 23, 2024
This post walks through the vulnerabilities we disclosed affecting Gradio, and our work with Hugging Face to harden the Spaces platform after a recently reported potential breach.
Traccar 5 Remote Code Execution Vulnerabilities
August 23, 2024
This post walks through the vulnerabilities we disclosed affecting Gradio, and our work with Hugging Face to harden the Spaces platform after a recently reported potential breach.
Exploiting File Read Vulnerabilities in Gradio to Steal Secrets from Hugging Face Spaces
June 14, 2024
This post walks through the vulnerabilities we disclosed affecting Gradio, and our work with Hugging Face to harden the Spaces platform after a recently reported potential breach.
NextChat: An AI Chatbot That Lets You Talk to Anyone You Want To
March 11, 2024
NextChat a.k.a ChatGPT-Next-Web, a popular Gen AI ChatBot, is vulnerable to a critical server-side request forgery (SSRF) vulnerability.