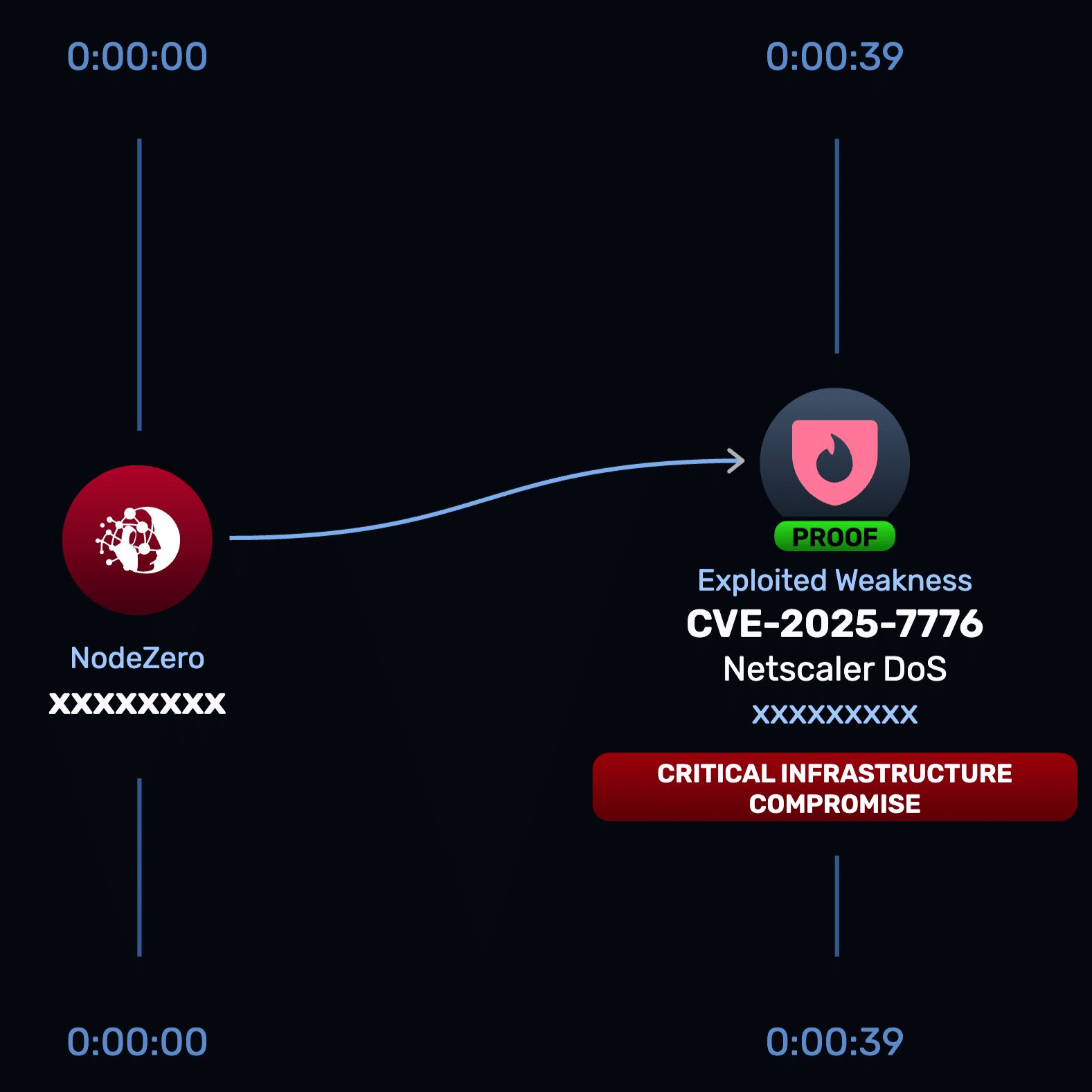
CVE-2025-7776
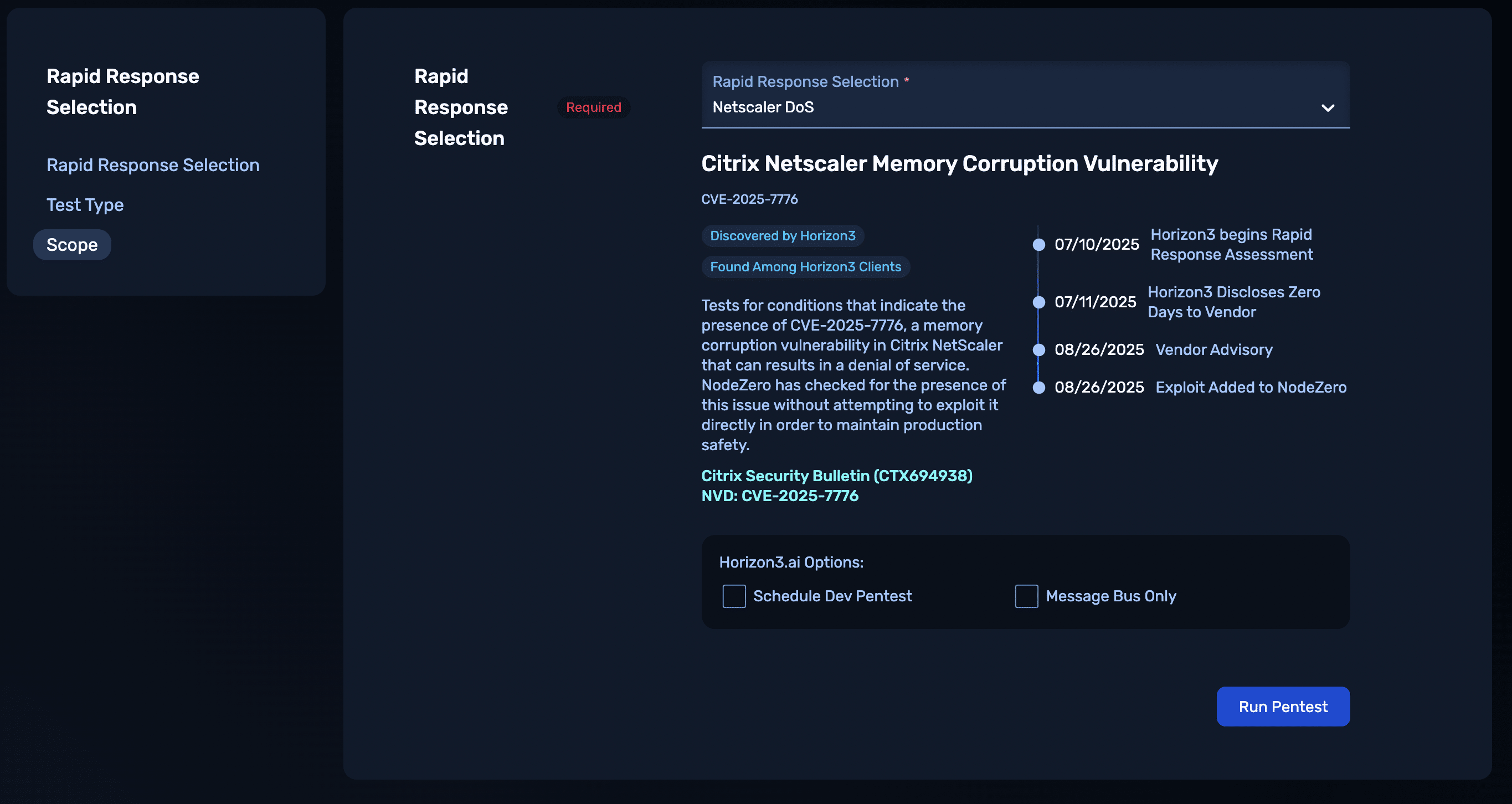
Citrix NetScaler Memory Corruption Vulnerability
Citrix NetScaler contains a memory corruption vulnerability that can cause the device and downstream applications to crash via the /broker/xml endpoint.
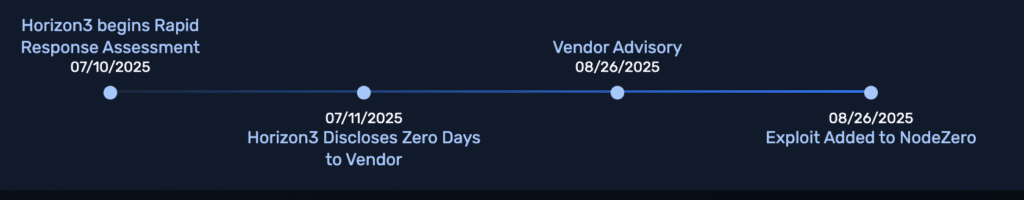
Horizon3.ai’s Attack Team discovered this vulnerability, and while real-world exploitation could allow an unauthenticated attacker to cause a denial of service to the NetScaler appliance and any downstream applications, NodeZero Rapid Response tests are safe for production. Our tests affirm exposure to this risk without crashing the service, delivering proof of impact without disruption.
Mitigations
- Update to the relevant Citrix NetScaler version as per the vendor advisory.
References
Rapid Response Test