CVE-2025-31324
SAP NetWeaver Visual Composer Metadata Uploader
A critical vulnerability, CVE-2025-31324, has been identified in SAP NetWeaver. Threat actors are actively exploiting this flaw to upload JSP web shells via the “/developmentserver/metadatauploader” endpoint, potentially leading to unauthorized file uploads and code execution.
Affected systems include those running SAP NetWeaver, particularly government agencies and enterprises. Because SAP solutions are often deployed on-premises, the onus is on the users to apply security measures. Failure to promptly update and patch systems significantly increases the risk of compromise.
Mitigations
- Follow the vendor’s guidance for updating to the latest version.
- Restrict access to /uddi/ URLs to internal network traffic, especially if upgrading isn’t feasible.
- Post-mitigation check for indicators of compromise.
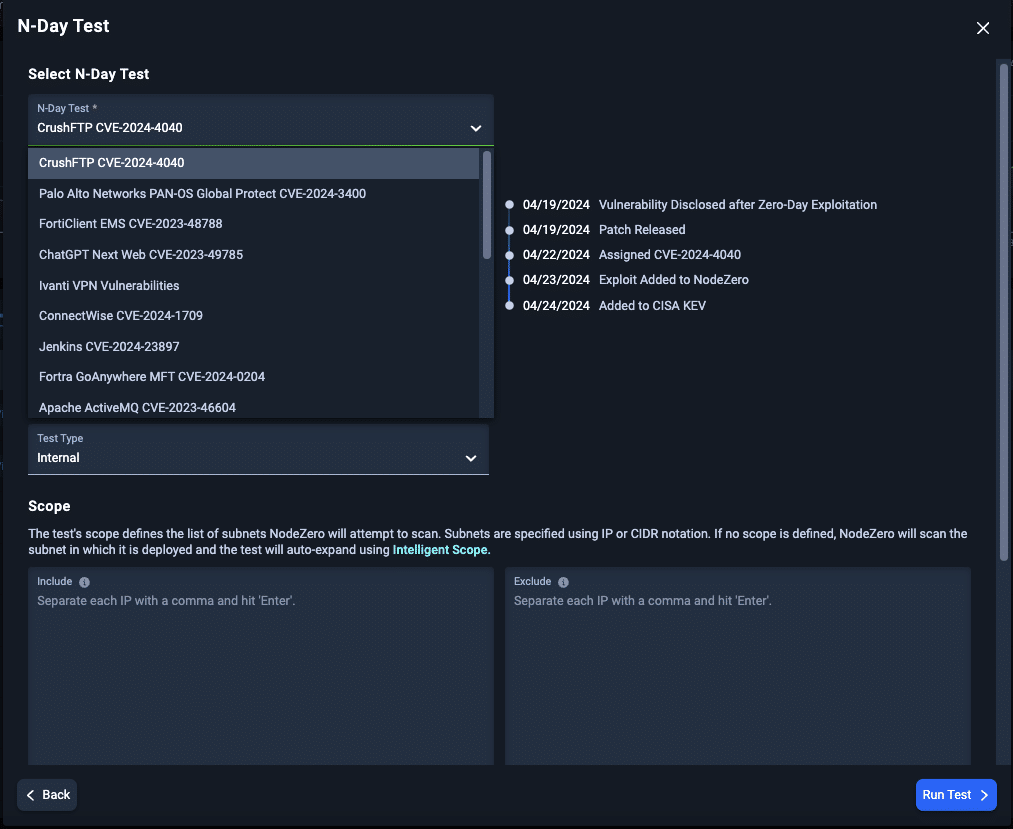
Rapid Response N-Day Testing
🔗 NIST Detail
🔗 New Critical SAP NetWeaver Flaw Exploited to Drop Web Shell, Brute Ratel Framework

