Vulnerability Risk Intelligence
View scanner results from the attacker's perspective
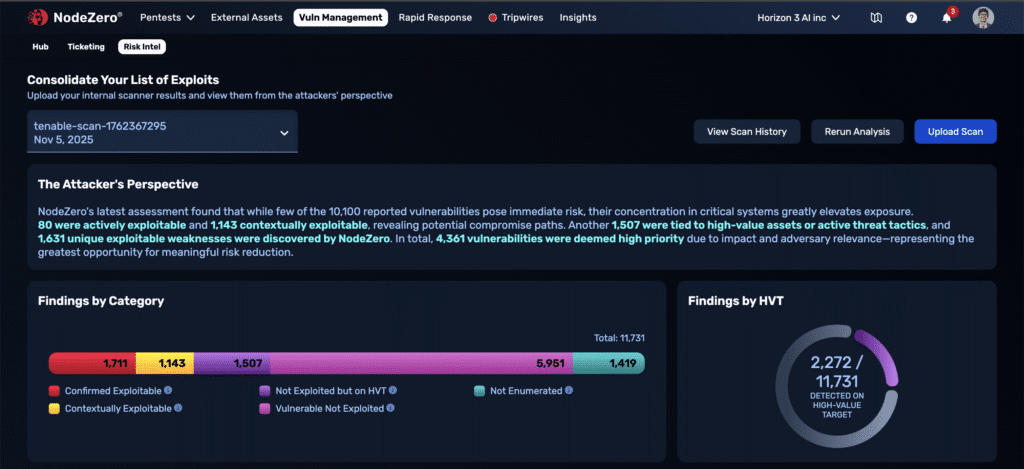
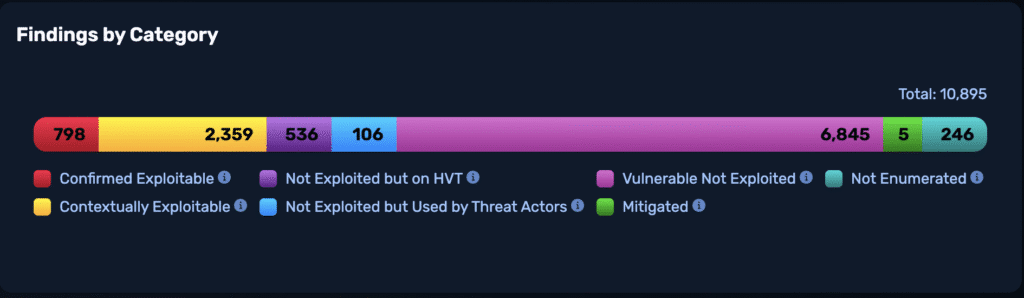
Vulnerability Risk Intelligence contextualizes vulnerability scanner data from Tenable, Qualys, or Rapid7 using attacker-validated proof-of-exploit, threat actor pressure, and, business risk inference. Avoid spreadsheet triage, save analyst time, and bring your VM, SecOps, and OffSec teams together with a prioritized list of vulnerabilities.
What it is and why it matters
Make vulnerability management risk-based and proof-first
How Vulnerability Risk Intelligence Works
Upload your exports
Drag-and-drop CSV or XML files from Tenable, Qualys, or Rapid7 into Vulnerability Risk Intelligence or POST via API. Inputs are automatically validated and scoped to the right environment.
Correlate against the attack engine
NodeZero maps each CVE to real attack paths across all pentests, deduplicating assets and correlating scanner findings with observed behavior.
Classify by exploitability
Each CVE–asset pair is automatically tagged from the attacker’s perspective:
- Confirmed Exploitable — validated with evidence.
- Contexually Exploitable — can be exploited by elite attackers under specific preconditions.
- High-Value Target Found — detected on a crown jewel asset like a domain controller.
- Threat Actor Pressure — CVE known to be abused by APTs.
- Not Exploited — not exploited in your environment.
Prove that top risks have been remediated
View exploitable vs. non-exploitable findings, mappings to threat actor behavior and high-value targets, and direct links to exploit evidence in a single view. Dispatch key risks to ticketing systems and download results for reporting workflows.
Save analyst time and spend on aggregation tools with Vulnerability Risk Intelligence
Prove, don't guess
Save spend with fewer tools
Proof efficacy to executives