Threat Actor Intelligence
Reveal which adversaries match your exposures
Knowing you have a vulnerability isn’t enough. Security teams need to know who would exploit it — and what that risk means in the real world. Threat Actor Intelligence connects NodeZero® pentest results to known adversary tactics, techniques, and procedures (TTPs), helping you prioritize remediation based on threat relevance, not just CVE counts.
Adversary-aligned context, not just vulnerabilities
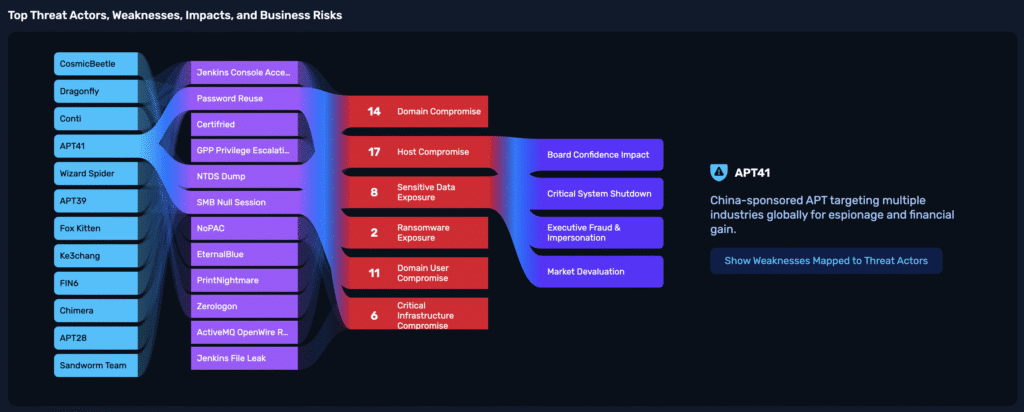
Threat Actor Intelligence links exploitable vulnerabilities in your environment to the adversaries who weaponize them. NodeZero maps every exploit to MITRE ATT&CK tactics, correlates them with threat groups, and shows how those paths lead to ransomware, data theft, or operational loss. The result is clear, adversary-driven context that turns vulnerability noise into true risk-based prioritization.
Prioritization powered by threat actor activity & business impact
MITRE ATT&CK Mapping
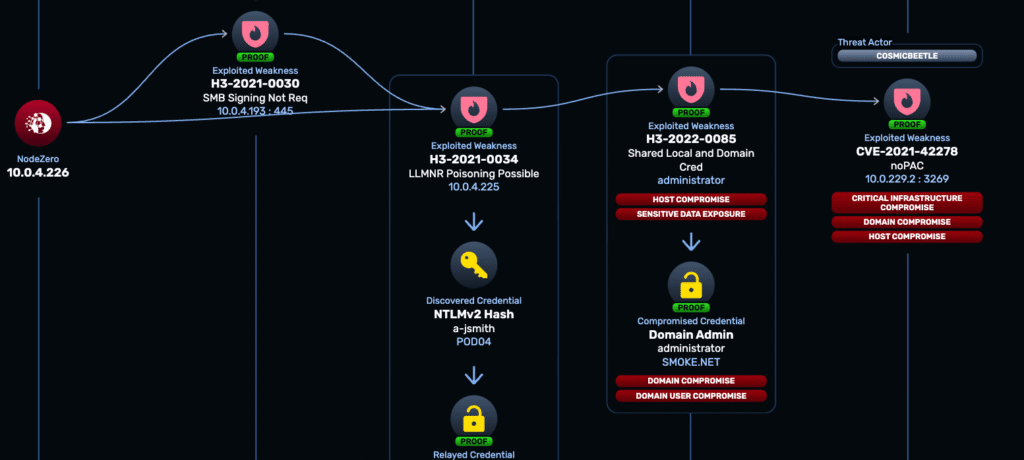
Ties every exploited vulnerability to MITRE ATT&CK tactics and techniques, showing how real attacks unfold.
Threat Actor Correlation
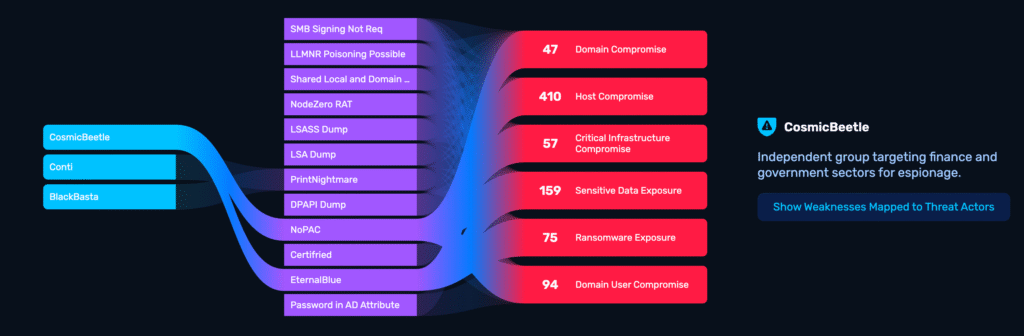
Links exploits to groups like AKIRA and Salt Typhoon for clear adversary context.
Business Impact
Illustrates how one weakness can lead to domain compromise, data theft, ransomware, or operational loss.
Risk-Based Prioritization
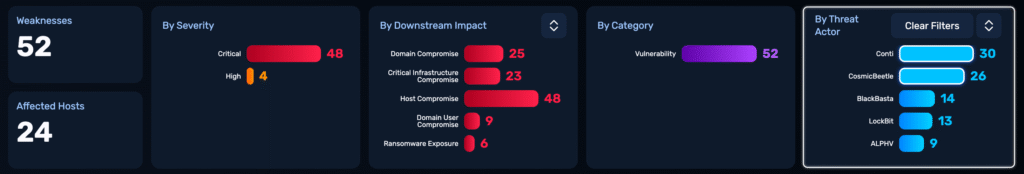
Ranks vulnerabilities by business impact, adversary activity, and exploitability.
Agentic Remediation
Integrates with MCP Server to automate, orchestrate, and verify fixes in a continuous loop
Why threat-informed intelligence changes everything
Prioritize what adversaries weaponize
Stop chasing CVE headlines. Focus on the weaknesses ransomware crews, nation-states, and financial crime groups are actively exploiting in the wild.
Map real attacks to real adversaries
Every NodeZero exploit is aligned to MITRE ATT&CK tactics and correlated with known groups like Salt Typhoon or AKIRA, revealing the tradecraft behind the threats.
Turn exploits into business risk clarity
See how a single vulnerability can escalate into domain compromise, data theft, ransomware, or fraud — with clear ties to financial, regulatory, and operational impact.
Communicate risk with confidence
Translate technical findings into business terms with threat actor mapping and attack-path visualizations that resonate with executives, boards, and auditors.