Attackers Don’t Think in CVEs. Neither Should You.
Horizon3.ai’s Risk-Based Vulnerability Management (RBVM) shows you which risks truly matter, combining live exploit intelligence, GenAI reasoning, and attacker pressure to help you prioritize what attackers care about most.
Request a DemoVulnerability Management Is Drowning in Noise.
Traditional scanners flood teams with thousands of generalized CVSS ranked CVEs and false positives. Point-in-time testing offers temporary clarity but no lasting confidence. Meanwhile, AI-empowered threat actors are moving faster than defenders can triage.
The result: slow remediation, wasted resources, and business leaders blind to real risk.
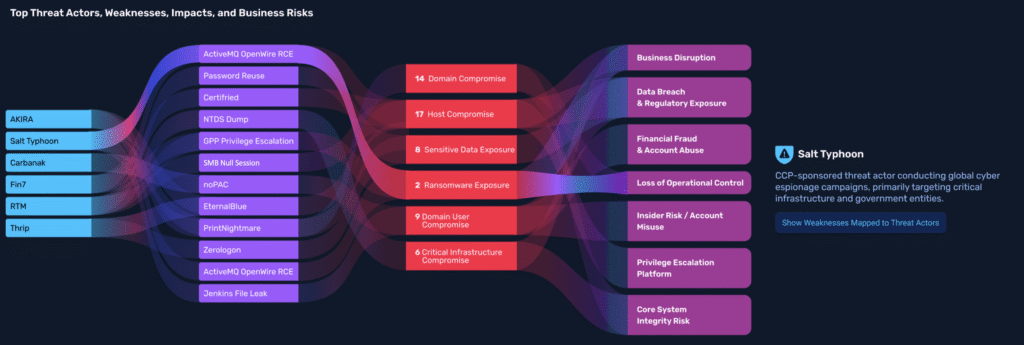
From Exploits to Impact: Risk Through the Attacker’s Lens.
Threat Actor Intelligence (TAI)
Know Who’s Coming for You.
TAI connects live attacker behavior to your environment; mapping campaigns, TTPs, and firmographic targeting into a measurable Threat Actor Pressure Index.
Prioritize based on who’s attacking you, how they operate, and where you’re exposed.
High-Value Targeting (HVT)
Find What Matters Most.
Automatically identifies and ranks your most critical systems, identities, and users — the assets attackers care about most.
GenAI reasoning ties each exploit to potential business impact, turning technical findings into clear, risk-based priorities.
Advanced Data Pilfering (ADP)
Understand Why Data Matters.
ADP goes beyond data discovery, it explains the consequence of exposure.
NodeZero automatically classifies and tags data with business-relevant risk categories like IP Theft, PII Leakage, and Regulatory Impact, giving security leaders clear evidence of what’s truly at stake.
Vulnerability Risk Intelligence (VRI)
Turn Scanner Noise into Exploit Intelligence.
Integrate results from your existing scanners and let NodeZero filter out false positives and surface what’s actually exploitable.
Correlate vulnerability data with attacker pressure and asset value to see which issues matter, right now.
Customers Are Cutting Through the Noise.
“Using HVT and ADP, we finally connected vulnerabilities to board-level risk discussions.”
“Our RBVM rollout reduced 18,000 scanner findings to 21 exploitable, business-critical paths — in one week.”
“Threat Actor Intelligence revealed exposures linked to Volt Typhoon campaigns — insights we couldn’t get from any scanner.”
