Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
Gladinet Triofox Improper Access Control Vulnerability | Active Exploitation
Read More →WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
Demonstrating DORA Resilience in the Legal Sector
April 24, 2025
Discover how NodeZero® helps legal firms proactively reduce cyber risk with real-world attack simulation, identifying exploitable gaps and providing actionable insights to strengthen security.
Why Adversarial Exposure Validation Belongs in Every CTEM Program
April 24, 2025
Discover why Adversarial Exposure Validation (AEV) is essential to any CTEM program. Learn how continuous, automated validation strengthens security, boosts red teaming, and proves real-world risk reduction.
NodeZero® Release Recap: Spring Edition
Watch Horizon3.ai PMs demo the latest NodeZero updates—from NodeZero Tripwires™ to NodeZero Insights™, AD cracking, and new external attack techniques.
Key Insights from Over 50,000 NodeZero® Pentests Infographic
April 10, 2025
Key findings from Horizon3.ai’s Annual Insights Report, powered by NodeZero® data and a survey of 800+ CISOs and IT pros.
Unsafe at Any Speed: Abusing Python Exec for Unauth RCE in Langflow AI
April 9, 2025
CVE-2025-3248 is a critical code injection vulnerability affecting Langflow, a popular tool used for building out agentic AI workflows. This vulnerability is easily exploitable and enables unauthenticated remote attackers to fully compromise Langflow servers. The issue is patched in Langflow 1.3.0.
Speed Through Uncertainty: The Find, Fix, Verify Loop for Exposure Management
See how autonomous pentesting with NodeZero helps you find, fix, and verify cyber risks fast—no more waiting weeks for answers.
NodeZero® Release Recap: Spring Edition
April 7, 2025
Spring updates are here! Explore NodeZero’s latest threat detection, pentest, and insights features—built to stay ahead of attackers.
There’s More To Our Annual Report: The State of Cybersecurity in 2025
April 2, 2025
Discover hidden cybersecurity risks from our 2025 report. Unfiltered insights on BAS, compliance pitfalls, third-party threats & more.
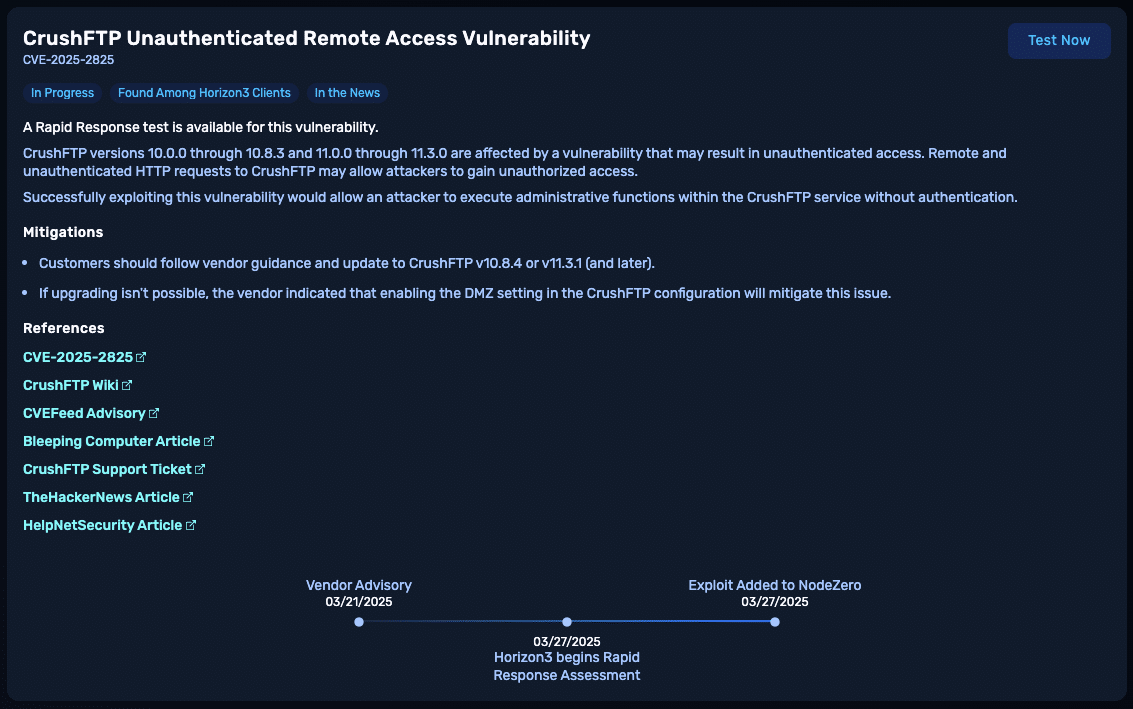
CrushFTP Authentication Bypass: Indicators of Compromise
March 27, 2025
CrushFTP auth bypass (CVE-2025-2825) could grant attackers admin access. Learn IoCs & test exposure with NodeZero. Patch now!
The State of Cybersecurity in 2025: Data-Driven Insights from Over 50,000 NodeZero® Pentests
March 26, 2025
Insights from 50K+ NodeZero®️ pentests reveal why offensive security is key in 2025. Learn how to move beyond compliance and close critical gaps.