Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
Tech Talk: The Attackers Journey Pt. 2
This series centers around how to be an ethical hacker and the steps/processes to get there. In part 2, topics like understanding SQL injection; what SQL injection leads to; why defenders, IT Operators, etc. should care; and so much more were discussed.
SANS Webcast w/ Sponsor Horizon3.ai
Many penetration tests are only point-in-time and/or manual. In this Horizon3.ai sponsored webcast from SANS, take a First Look at how Horizon3.ai’s NodeZero takes on the pen test problem. Listen to SANS Senior Instructor Dave Shackleford and Horizon3.ai’s CEO and Co-Founder Snehal Antani discuss the platform’s highlights and why it might be right for your…
NYIS Meetup Panel, “How do you know it’s fixed?”
David Raviv, host of NYIS Meetup, Snehal Antani, CEO and Co-founder of Horizon3, Steve Ramey of Arete Advisors LLC, and Mark Rasch, computer security and privacy expert, lawyer, author, and commentator, met for a panel discussion over 'How do you know it's fixed?' Learn about: - Employing a defense strategy w/ multiple layers - Identifying…
Tech Talk: The Attackers Journey Pt.1
Join us in side-saddling on an attacker’s journey with Noah King to become an ethical hacker!
Defense in Depth
February 19, 2022
Defense in depth is a proven strategy for protecting systems and software from insider and external attacks.
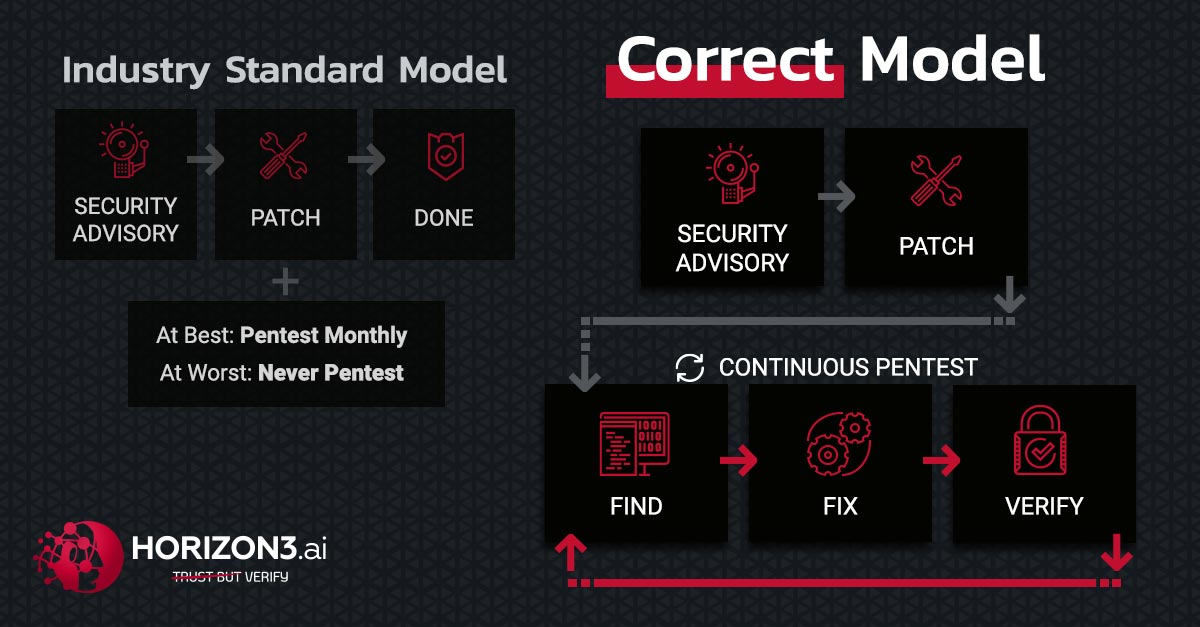
The Industry Standard Model is the Vulnerability
February 11, 2022
Which is more valuable to you; the ability to identify a problem, or the ability to solve the problem? There is a plethora of vulnerability scanning tools that do a decent job identifying vulnerabilities. Unfortunately, those tools rarely discern the possible from the exploitable.
NYIS Fireside Chat with David Raviv
On January 28, 2022, CEO and Co-founder Snehal Antani sat down with host David Raviv of NY Information Security Meetup for an insightful fireside chat. They discussed Snehal's career as former CTO of Splunk and JSOC, his inspiration for starting Horizon3, and his outlook on the future of cyber warfare. Learn about: - Employing a…
Using NodeZero to Find and Fix Log4Shell
January 6, 2022
Log4Shell is a "once-in-a-decade" type of vulnerability that will linger in environments for years to come. For a vulnerability with such a broad, lasting impact, it's important to establish a principled and disciplined approach for discovering and remediating it. NodeZero both detects and exploits Log4Shell, surfacing a wealth of information that can be used to…
Understanding Log4Shell: the Apache log4j2 Remote Code Execution Vulnerability (CVE-2021-44228, CVE-2021-45046)
December 10, 2021
Understanding Log4Shell: the Apache log4j2 Remote Code Execution Vulnerability (CVE-2021-44228)
Hack The Box – Mirai
December 6, 2021
NodeZero compromised HTB’s Mirai machine by using default SSH creds for user pi, then escalated to root via unrestricted sudo access—gaining full control.