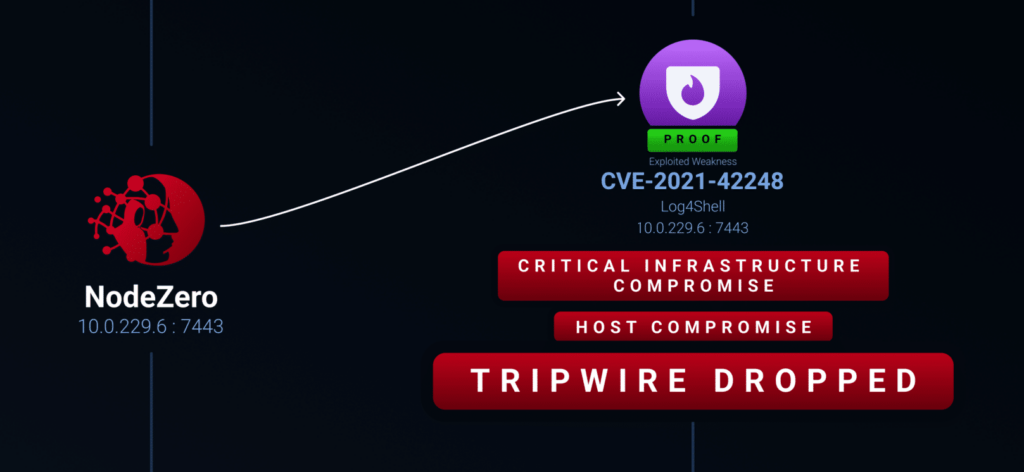
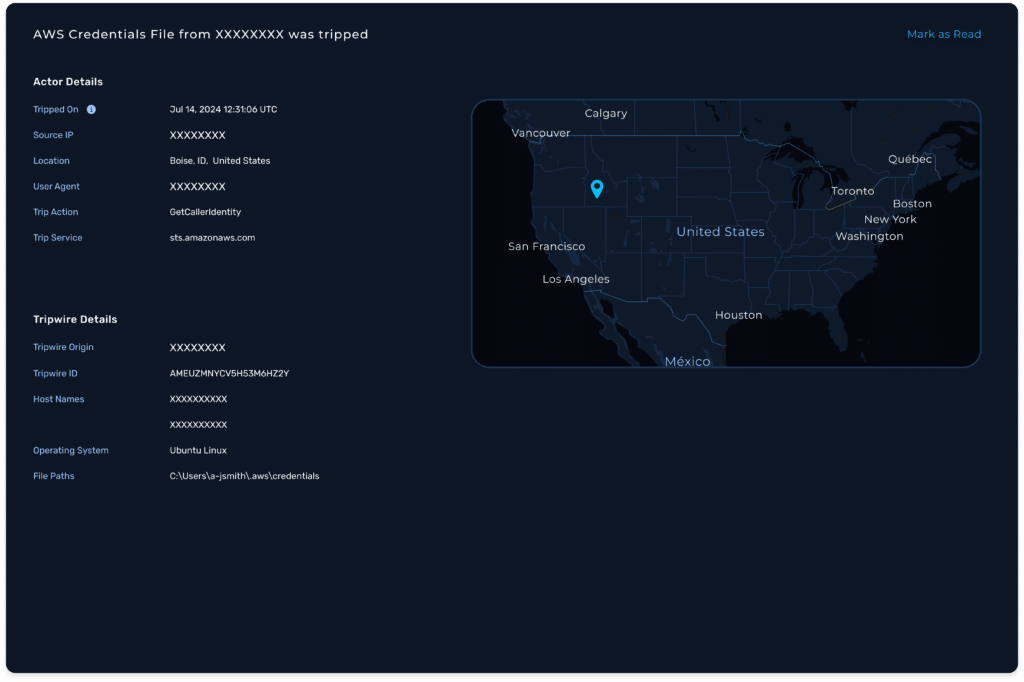
NodeZero Tripwires™
NodeZero uses pentest findings to drop expert-designed decoys as it discovers critical risk.
Tripwires alert in real time when they detect potentially malicious activity.
Bring the attacker’s perspective to threat detection.
Key Features
Smart Deployment
Tripwires (decoys and monitoring files) are automatically deployed during pentests as NodeZero exploits assets and proves critical downstream impact.
Selected Asset Coverage
Control to add overwatch against crown jewel assets or assets with lower-level risk exposure reflects your business context.
Centralized, Real-Time Alerts
Immediate, detailed alerting in the Tripwires dashboard and via your security tools of choice equips teams to contain breaches, fast.
Expert-designed deception
Enticing tripwire types and placement is backed by expert attack research to maximize decoy efficacy while minimizing noise.
Diverse Test Coverage
One-click activation within internal, external, AWS, Phishing, Insider Threat, or Rapid Response tests.
Integration with your SOC
Integrate Tripwires into your existing incident response workflow with seamless data flow into your SIEM, SOAR, and more.
How it works
Start a Pentest
Enable NodeZero to Drop Tripwires Automatically
NodeZero deploys appropriate tripwire types onto assets with critical risk as part of one-off or recurring tests, ensuring coverage as soon as exposure is discovered.
Add Coverage for Select Assets
NodeZero extends coverage to any assets—whether crown jewels or those with known-but-lower risk profiles—to proactively add detection.
Cover your window of exposure
In the real-world, organizations are never risk-free. Tripwires reduces the potential blast radius if an attacker breaks in, adding overwatch for:
Ready to connect with Horizon3.ai?
Submit the form below.