NodeZero Solves GOAD —
In 14 Minutes
Game of Active Directory (GOAD) is the closest thing to a real enterprise AD battleground. Expert humans take 12–16 hours to solve it. NodeZero did it in 14 minutes — about 50× faster — end-to-end, autonomously.
Want to run NodeZero against a GOAD?
Why this matters
Most “AI hacking” demos live in CTFs or single-host puzzles. Real breaches don’t. They span many hosts, cross trust boundaries, and rely on identity abuse and lateral movement. GOAD compresses that reality into a hard, multi-domain AD environment. Solving GOAD isn’t trivial—it’s a proxy for how offense actually works in the wild.
Why GOAD is hard (for humans and algorithms)
Multi-hop memory:
You must remember what worked three pivots ago and use it five pivots later.
Conditional execution:
Each step changes what’s possible next; you have to reprioritize in real time.
Trust boundaries:
Abuse domain trusts, SPNs, constrained delegation, legacy protocols—without breaking the environment.
Toolchain discipline:
Kerberoasting, AS-REP roasting, token replay, remote service abuse, and more—sequenced precisely.
Humans grind through this with skill and patience. LLMs alone tend to wander, repeat, or forget. NodeZero fuses graph-driven orchestration, LLM reasoning, and battle-tested toolchains to plan, adapt, and execute cleanly at speed.
NodeZero’s campaign — explained
Starting point: unauthenticated
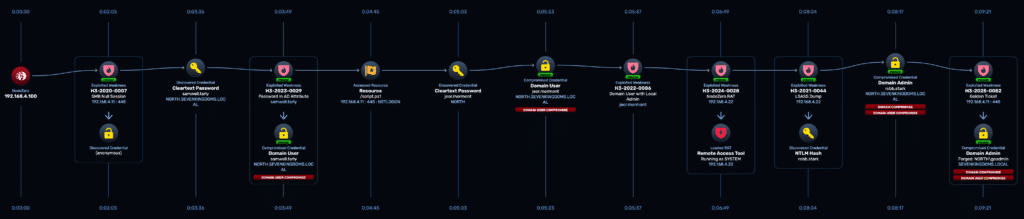
NodeZero began with no creds, no visibility, and no insider assumptions. It’s first move was exploiting anonymous access to a domain controller over SMB – just like an attacker would in the wild.
Building the chain in parallel
With that initial foothold, NodeZero moved quickly. It discovered scripts with embedded credentials, pivoted to systems where those credentials had local admin, and deployed a RAT — all while executing other tasks in parallel.
It escalated privileges, dumped LSASS, and harvested more credentials to expand access — accelerating the kill chain faster than a human red team could.
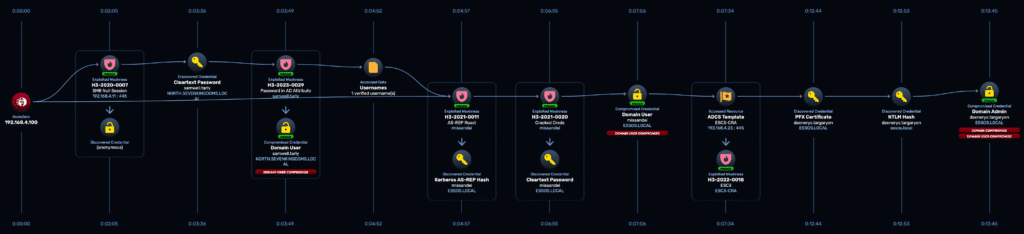
Domain compromise, then full forest takeover
NodeZero didn’t stop at one domain. It abused Active Directory Certificate Services (ADCS), exploited a vulnerable certificate template (ESC3), impersonated a domain admin, and moved laterally across trust boundaries into the parent domain.
In just 14 minutes, NodeZero had full control — without crashing systems or requiring a single manual command.
No simple attacks like exploiting CVEs or LLMNR poisoning.
Just autonomous software chaining real weaknesses into real impact.