Proof over theory —
Validate what attackers can actually exploit, not what models predict.
The missing piece? Validation.
The NodeZero® Offensive Security Platform makes CTEM practical by running live attacks in production, proving which exposures matter, and verifying that defenses and remediations actually work.
CTEM starts with Scoping—mapping your real attack surface across networks, identities, and cloud workloads. But most tools show yesterday’s snapshot, not today’s reality.
NodeZero builds a live graph across networks, cloud, identities, and endpoints — showing the true attack surface an adversary would exploit.
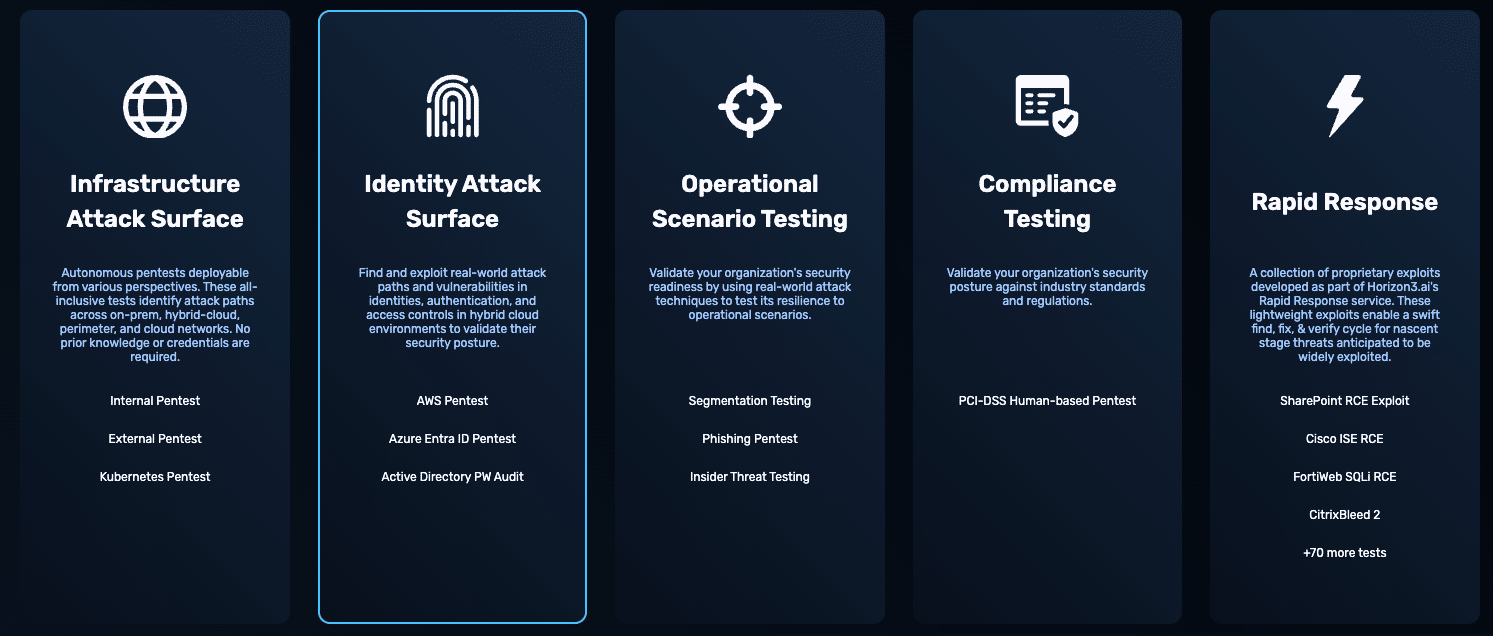
Beyond CVEs, NodeZero finds weak or reused credentials, misconfigurations, and chained weaknesses. Advanced Data Pilfering surfaces buried credentials and sensitive business data that scanners miss, then feeds them into attack paths to show true impact.
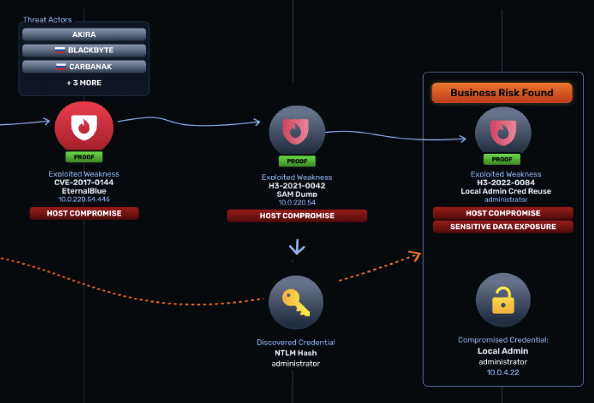
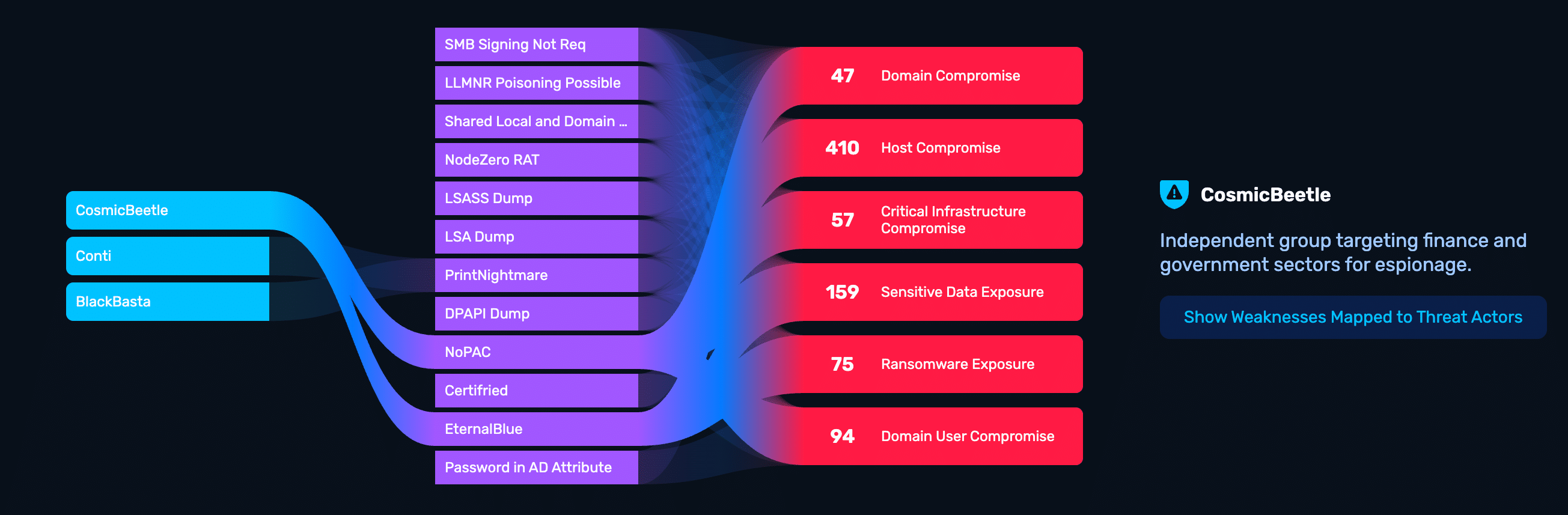
High Value Targeting highlights crown-jewel paths to executives and critical systems. Threat Actor Intelligence maps observed techniques to known adversary TTPs, so teams focus on exposures attackers would actually exploit — including CISA Known Exploited Vulnerabilities (KEVs) weaponized in NodeZero within hours.
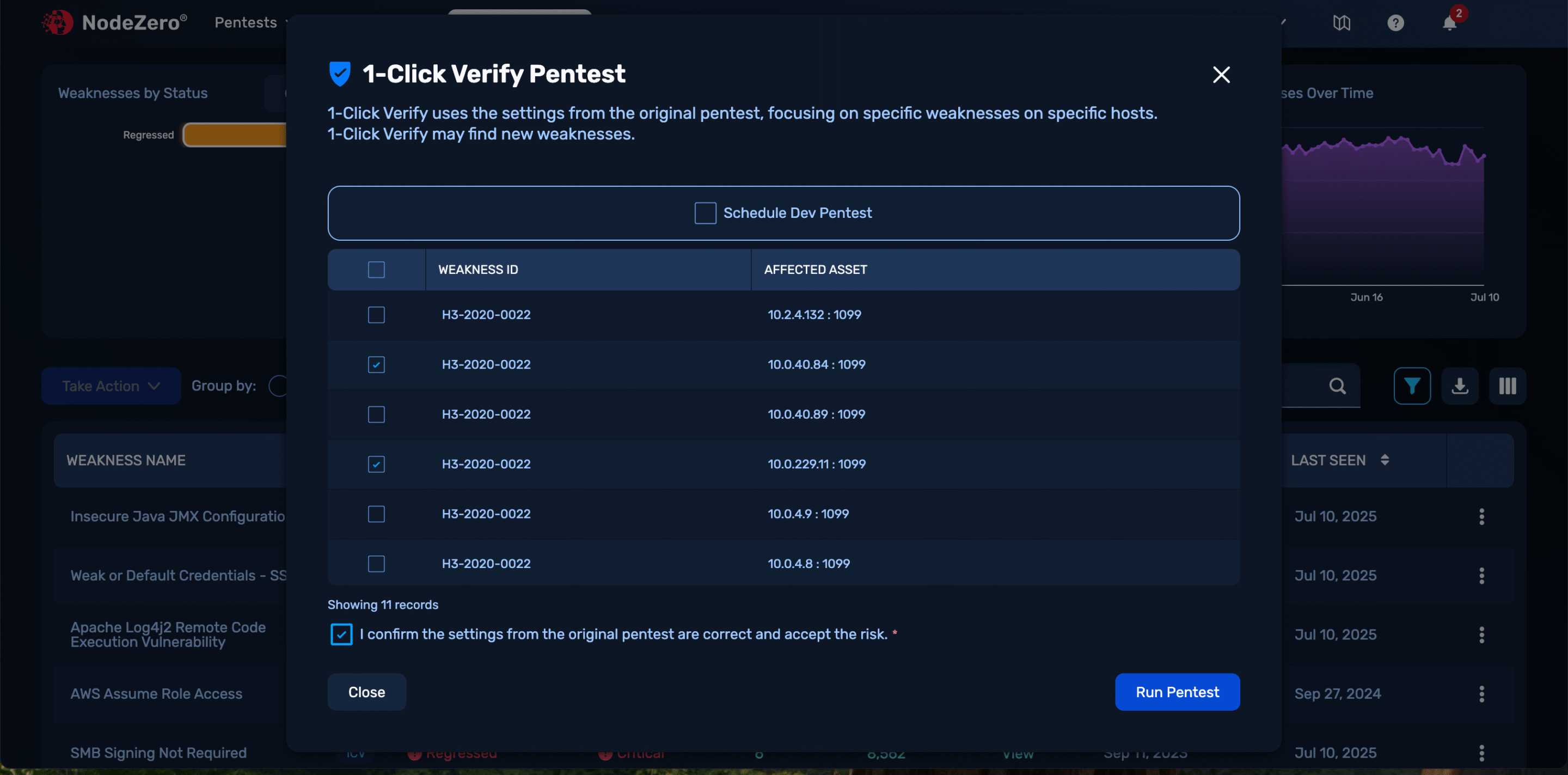
Run real-world tests against controls. Endpoint Security Effectiveness shows whether EDRs respond in production, while one-click retests confirm remediations work, reducing both Mean Time to Mitigate (MTTM) and Mean Time to Remediate (MTTR).
The Vulnerability Mangement Hub centralizes validated weaknesses, attack paths, and fix actions. Integrations with ServiceNow, SIEM, and SOAR push proof-backed workflows into the tools your teams already use.
From foundational concepts to advanced implementation, we’ve compiled our top CTEM content to help you build a more proactive security posture.