Continuous Threat Exposure Management (CTEM) has quickly evolved from concept to cornerstone for security teams looking to improve their cybersecurity by being more consistent and action-oriented in their practices. By continuously identifying, prioritizing, validating, and remediating exposures—rather than treating vulnerabilities as an unattainable checklist—organizations reduce real risk.
In our opinion, Gartner® has since recognized two new categories of technologies that together support the CTEM framework:
- Exposure Assessment Platforms (EAPs) continuously identify and prioritize exposures across a broad range of asset classes
- Adversarial Exposure Validation (AEV) provides consistent, continuous and automated evidence of the feasibility of various attack scenarios
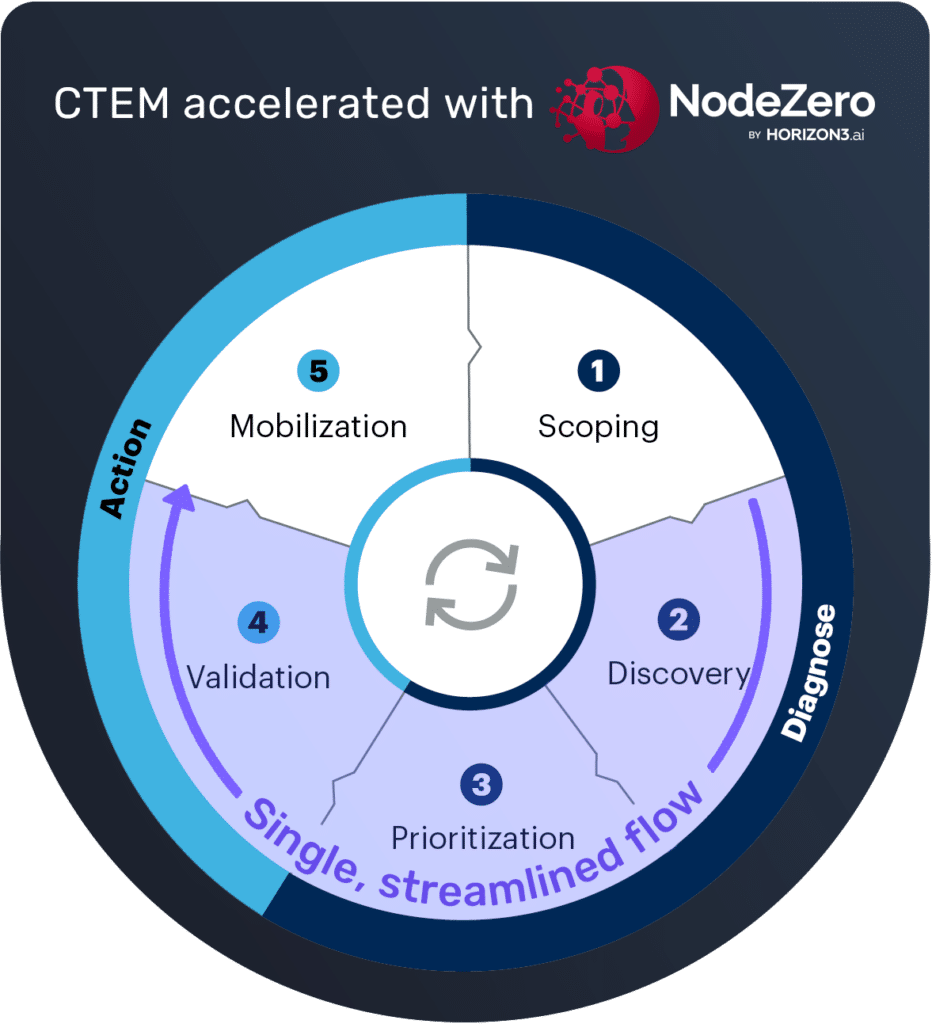
Defining Adversarial Exposure Validation (AEV)
In the recently published Gartner® Market Guide for Adversarial Exposure Validation report it states,
Validating threat exposure against attack scenarios and techniques benefits both offensive and defensive security teams. This research helps security and risk management leaders understand the key use cases of adversarial exposure validation and navigate the AEV solution market.”
We feel the recognition of Adversarial Exposure Validation (AEV) marks a critical turning point for defenders: the shift from assuming security is working—to proving whether it is.
According to the Gartner® Market Guide for Adversarial Exposure Validation report, Horizon3.ai is a Representative Vendor.
Our Perspective on Adversarial Exposure Validation
Security teams are stretched thin, yet constantly asked to deliver more confidence and accountability. AEV helps leaders:
- Validate that security investments are working—and worth the spend
- Move from sporadic to continuous testing, driven by real attacker logic
- Start or scale red teaming efforts without needing more staff
- Remediate faster and smarter, with actionable guidance and automated retesting
It’s about operating from a position of clarity, not guesswork—and making business-aligned decisions based on real proof.
Features to expect from AEV solutions
There are a number of capabilities technologies need to offer to support you in meeting the goals of Adversarial Exposure Validation. Here’s what to ask:
- How do you automate penetration testing and execute multistep attack scenarios across the enterprise?
- What threat vectors do you support with your attack scenarios?
- How frequently can you run automated attack scenarios across exposed assets?
- How do you use proven attack paths and impact across our organization to prioritize exposure?
- How often do you update attack scenarios leveraging threat intelligence?
- How do you help validate your defensive controls?
How NodeZero® Delivers on the Promise of AEV
In our opinion, vendors differ in how—and how well—they support the outcomes teams want from AEV. What we believe sets NodeZero apart is how well it equips users to understand their true cyber risk: at scale, in production, and with the dynamic perspective of an attacker.
Safe, Real-World Testing in Production
Your networks are too complex and agile to trust a sample or simulation.
- No simulations, no golden images—NodeZero tests against your live environment safely and autonomously.
- Works across cloud, on-prem, and hybrid infrastructures.
- <15-minute deployment with no agents or permanent credentials.
Unlimited, On-Demand Testing
The only way to know what’s most important today? Test as often as your environment and the threat landscape change.
- Priced per asset, not per test—run as frequently as your environment or threat landscape changes.
- SaaS-based delivery means you always get the latest features and attack capabilities without managing manual upgrades.
Dynamic, Autonomous Attack Paths
No relying on pre-scripted, brittle attack paths that lack attacker ingenuity.
- NodeZero autonomously discovers your network and takes the next-best-action, without human direction or scripting.
- Identifies and chains together vulnerabilities, weak credentials, misconfigurations, and missing controls.
- Delivers transparent attack path maps, including scripts for replication and verification.
Proof of Impact and Fast Remediation
Drive cross-team alignment and urgency with transparency and guidance.
- Each exposure is backed by proof of exploitation, not just hypothetical risk.
- Fixes are prioritized by business impact, not CVSS scores alone.
- Precise, instructive remediation steps and a 1-click verify to close the loop—and the ticket.
Continuous Threat Coverage
Stay ahead of emerging threats with a world-class attack research team in your corner.
- Our expert attack team constantly adds new capabilities, from common exploits to Zero- and N-day vulnerabilities.
- Proactive alerting and validation give you lead time to address relevant nascent threats.
Built for IT, Blue Teams, and Red Teams
Add or extend offensive expertise without adding headcount.
- Empowers IT to fix what matters with clarity and confidence.
- Uplevels defenders by providing real-world attacker insights.
- Acts as a force multiplier for internal red teams, enabling wider coverage and deeper attack emulation without the overhead.
A New Category, a Proven Solution
The Gartner® Market Guide may be new, but we feel the principles behind AEV are not. Organizations need a scalable way to continuously understand their exposure, verify the effectiveness of controls, and drive measurable risk reduction.
NodeZero was built to do exactly that—and we believe it’s doing it today.
What’s Next
If you’re building or refining your CTEM program, adversarial exposure validation shouldn’t be a bolt-on—it should be foundational.
The Gartner® Market Guide for Adversarial Exposure Validation is a must read for those embarking on CTEM initiatives.

