Introduction
As someone who approaches networks with the intent to break in (ethically, of course), I know firsthand that the best way to secure an environment is to test it like a real adversary would. NodeZero, an autonomous pentesting platform, is one of the tools I use to emulate real-world attacks against a company’s environment. It’s not just about scanning for vulnerabilities—it’s about finding and using credentials, chaining weaknesses, escalating access, and seeing how far I can go or what I can find.
In this post, I’ll walk through how I personally use NodeZero from an attacker’s perspective to perform an internal or external assessment and highlight what makes it so effective.
The Attacker’s Mindset
When I run a pentest, I don’t just check for CVEs and call it a day. I’m looking for the path of least resistance—misconfigurations, exposed services, weak credentials, legacy systems, and overprivileged accounts. Each of these steps—discovery, enumeration, credential testing, privilege escalation—can be time-consuming and tedious to execute manually, often taking days or even weeks depending on the environment.
NodeZero helps automate this mindset and alleviates about 90% of that time burden. It doesn’t require preloaded knowledge about the environment—it discovers, enumerates, and pivots just like I would, but in a fraction of the time. Also, it’s autonomous, so while it’s doing its thing, I can focus on enumerating something juicy, it or I found.

My Workflow with NodeZero
Here’s how I typically use NodeZero in an engagement:
1. Initial Access (Discovery Phase): When I’m starting a pentest, the discovery phase typically involves running multiple tools to scan the network, fingerprint devices, identify services, and build an asset inventory. It’s a noisy, time-consuming process that eats up hours of work—sometimes more if the environment is large or segmented.
With NodeZero, I kick off the operation and it autonomously handles this entire process. It starts scanning and fingerprinting assets, identifying open ports, services, versions, and exposures. I don’t need to manually correlate findings or sift through nmap and enum4linux output—NodeZero builds the attack surface for me, freeing me up to think strategically about next steps. This phase used to take a full day or more; now, it’s largely hands-off and I can reallocate my time.
2. Credential Attacks: Traditionally, testing for credential-based access means building custom wordlists, launching password sprays, managing tooling like Hydra or CrackMapExec, and correlating results manually. It’s effective, but can be tedious and noisy, and success rates vary.
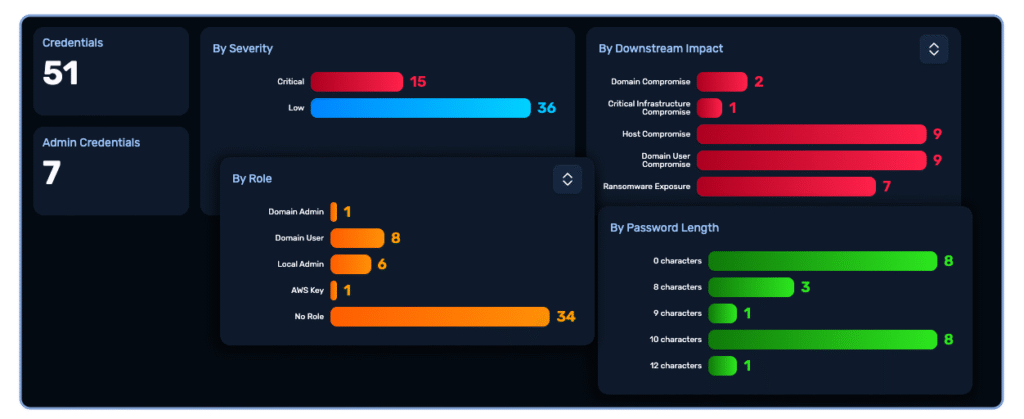
NodeZero autonomously handles this entire step. If there are exposed services like SMB, RDP, or SSH, it attempts to authenticate using default, weak, or previously compromised credentials and performs password spraying. We’ve seen an astonishing success rate with this, particularly in environments with weak password policies.
If I uncover credentials elsewhere—say through OSINT or another tool—I can inject them into NodeZero, which will then validate and use them in its attack chain. Instead of spending hours setting up and tuning attacks, I get results quickly and with far less effort. Whether it’s a local admin password reused across machines or something found in a config file, NodeZero is designed to recognize and weaponize it.
3. Privilege Escalation & Lateral Movement: After gaining access, I typically shift focus to escalating privileges and moving laterally. This can involve parsing system configs, hunting for tokens, exploiting local vulnerabilities, and deploying RATs or other tooling to pivot. It’s an advanced and sensitive stage of the engagement that takes time and care to execute well.
NodeZero handles a huge chunk of this autonomously. It looks for escalation paths, impersonates tokens, identifies misconfigs, and moves laterally on its own. We also have the ability to use an in-house-built RAT during this phase, which means I don’t have to deploy my own. That saves me both time and the operational overhead of managing persistence or evasion. I can instead focus on analyzing critical assets or digging into promising leads NodeZero uncovers.
One of the things I find most useful is how NodeZero chains together small findings into real attack paths. For example, a misconfigured share might lead to a credentials file, which leads to admin access on another box, which leads to domain compromise.
4. Proof of Exploitation: Traditionally, after finding a vulnerability, I need to exploit it manually, capture output, and take screenshots to show the risk to stakeholders. This is a major differentiator between basic vulnerability scanning and real pentesting. A vuln scanner might say something is exploitable, but it doesn’t validate whether mitigations are in place. Without proof, you can’t fully understand risk.

NodeZero relieves me of that burden. It doesn’t stop at identifying a vulnerability—it exploits it, captures command output, and takes screenshots to prove impact. It collects the same kind of proof I would manually—but faster and more reliably. That allows me to shift my energy toward deeper analysis instead of spending hours validating each finding.
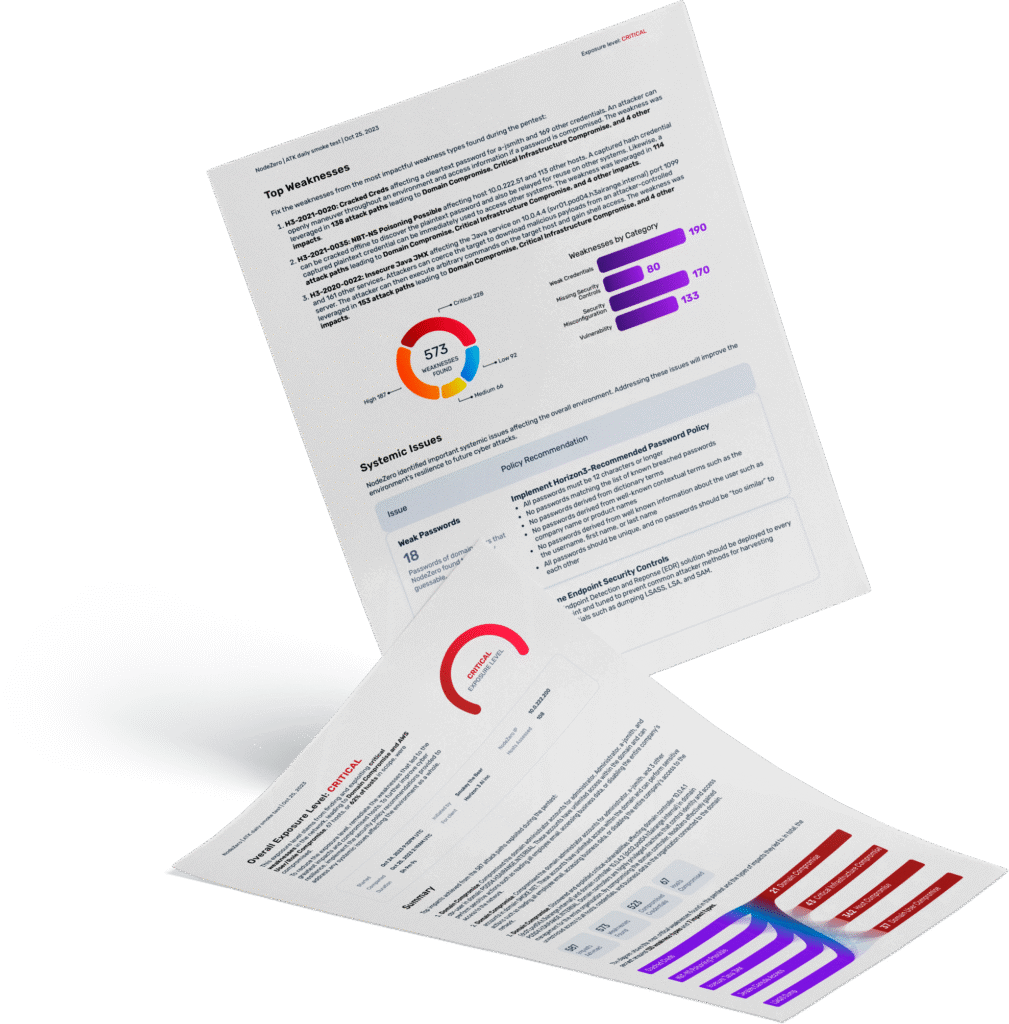
5. Reporting & Remediation: As a pentester, this is the final—and often most painful—step. I used to spend days or weeks compiling all the data, writing narratives, inserting evidence, and formatting the report. This is the deliverable the client sees, so it has to be both professional and accurate. But it’s a time sink.
NodeZero changes the game here. It autonomously generates a detailed report that outlines the attack paths, exploited vulnerabilities, collected evidence, and includes remediation recommendations. While I still review and customize it, I’m no longer starting from a blank slate. This is the actual product that gets delivered to the customer, and it’s arguably the most important part of the entire process. The time I save here is significant, and I can instead focus on writing impactful summaries or tailoring the output for different audiences.
The remediation guidance is practical, often actionable as-is, and cuts down on the back-and-forth explanations that usually follow a pentest report.
A Real Example
I was performing a pentest engagement in an environment with about 2600 hosts, and with no prior knowledge of the network, I started by letting NodeZero autonomously perform the discovery phase. To my surprise, due to the speed of discovery, NodeZero found default credentials to an app running on a Windows host.
In that Windows host, it found a different set of credentials in a config file for a database. It then used those credentials to SSH into a different Linux host. At this point, NodeZero’s Linux post-enumeration capabilities weren’t fully implemented yet, but I continued with host enumeration manually and found a typical `smb.credentials` file, which contained credentials used to automatically map SMB shares on Linux systems.
To my disbelief, the file contained credentials (yes, I’m being sarcastic here). I didn’t yet know whether they were valid or valuable, but I decided to inject them into NodeZero. Astonishingly, those credentials were domain admin creds. With these, NodeZero was able to use them to uncover everything about the environment, and everything those domain admin creds had access to.

This all happened within 20 minutes—just 20 minutes after starting the operation—using an autonomous platform and myself as an anonymous entity in the network with no prior knowledge or credentials. Since that engagement, my team and I worked on developing and enhancing NodeZero’s capabilities so that it can now perform this entire process autonomously in every customer’s environment.
I would also like to highlight here that not a single CVE was exploited in order to achieve this result. Weak passwords and misconfigurations can possibly pose a greater risk to an organization.
Why This Approach Works
What makes NodeZero different from traditional scanners is its ability to behave like a real attacker. It’s not just a list of CVEs—it’s a step-by-step emulation of how someone like me would break into your systems. And because it’s autonomous, it allows me to focus more on analyzing the impact and building a narrative, rather than spending hours on recon.
NodeZero acts as a force multiplier during engagements. It’s like having a team of pentesters working alongside me—hundreds of co-pilots, all contributing their expertise in real-time. While I focus on analyzing the high-value findings or digging deeper into specific attack paths, NodeZero autonomously handles the more repetitive, time-consuming tasks. This not only speeds up the process but also ensures that no stone is left unturned. The efficiency it brings makes me feel like I’m scaling my capabilities, and that’s invaluable when tackling complex, large environments.
Every time I run it, I learn something new about the environment—and so does the client.
Final Thoughts
Using NodeZero, I can demonstrate real-world risk to organizations in a way that static reports and compliance scans can’t. By thinking like an attacker—and letting NodeZero do the same—we uncover what really matters: how someone could break in, what they could take, and how to stop them.

Wyatt Wilson
Senior Cybersecurity Expert | Penetration Tester | NodeZero Developer
With over 27 years of experience in the cybersecurity and penetration testing industry, I’ve worked on a wide variety of engagements. My expertise lies in offensive cyber security where I spent 20 years in the military and the past 4 years with Horizon3.ai. I specialize in red teaming and vulnerability assessments. I am also a developer behind NodeZero, Horizon3.ai’s autonomous pentesting platform that mimics real-world attacks to provide deeper insights into network security.
Certifications:
– Certified Information Systems Security Professional (CISSP)
– Offensive Security Certified Professional (OSCP)
– GIAC Penetration Tester (GPEN)
– GIAC Certified Incident Handler (GCIH)
– Certified Ethical Hacker (CEH)
– CompTIA Security+
Feel free to reach out or follow along for more insights on offensive security, red teaming, and practical cyber defense strategies.

