The CTEM framework has the right goals. NodeZero takes the bloat out of achieving them.
Let’s talk about YAGC (Yet Another Gartner® Category—we kid, we kid): CTEM. Truth is the cybersecurity space is overflowing with acronyms, frameworks, and categories, and, like vulnerability scanning, it can be hard to parse what matters amidst the noise.
You need to know whether it’s worth your time, and if so, what you’ll need to invest across tools, processes, and people to be successful.
Spoiler alert? Yes, it’s worth your time, and success is more approachable than you may think.
So, what is Continuous Threat Exposure Management?
First, it’s a framework, not a category, tool or solution. Gartner® created CTEM to help organizations improve their cybersecurity by being more consistent and action-oriented in their practices.
And it seems they’re bullish on the impact it will have: Gartner predicts that “by 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.”
“In an age where organizations can’t fix everything, nor can they be completely sure what vulnerability remediation can be safely postponed. CTEM is a pragmatic and effective systemic approach to continuously refine priorities, walking the tightrope between those two impossible extremes.”
Grounded in the right goals
Before we dive into the framework itself, let’s ground in the “why” behind it. According to Gartner, “the objective of CTEM is to drive consistent, actionable security posture remediation and improvement plans that business executives can understand and architecture teams can act upon.”
As we at Horizon3.ai consider CTEM, we see a number of best-practices that emerge from following the framework—all of which we agree are excellent.
Anchor security priorities to business goals
For you to be successful, your security strategy has to be intuitive for business executives. Their input on business criticality and risk tolerance will ensure you’re aligned on prioritization and acceptable outcomes.
Always be securing
Create regular, repeatable processes to continuously refine priorities as you learn. Sporadic, point-in-time testing leaves you massively exposed in a world where your attack surface and the threat landscape is constantly evolving.
…But don’t fix everything
You don’t have the resources to fix every weakness or vulnerability—and even if you did, many of the fixes would be a waste of time. In the real world, you need to know where to spend your team’s precious time, and where to make judicious decisions to either monitor a risk or accept it entirely.
The assumption that we should fix every risk to the business is old school. We now know—and have the tools to prove—what risk is consequential, and can make far better decisions on what action to take, including no action at all.”
Be a stellar cross-functional partner
Security teams can’t go it alone. You need buy-in to drive urgency and accountability against the right mitigations—because you’re often asking other teams to take action. You also need input to know when the business cost of a mitigation might be too high and require a different approach
Use learnings to optimize your security stack
Again, CTEM is a framework, not a category. As you apply the framework, you’ll get invaluable feedback on where your existing tools are working as designed and where you may need to optimize or make incremental investments.
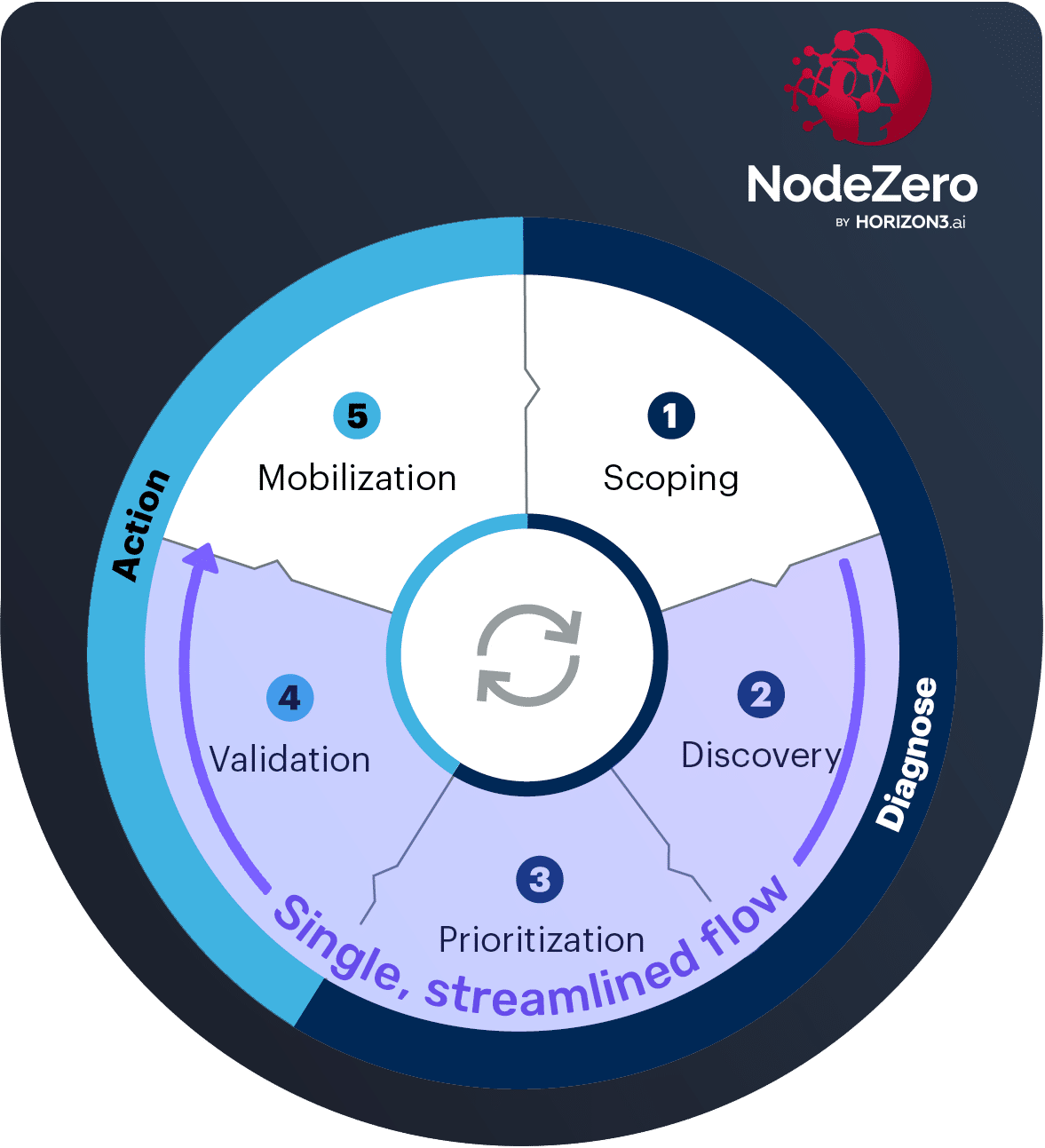
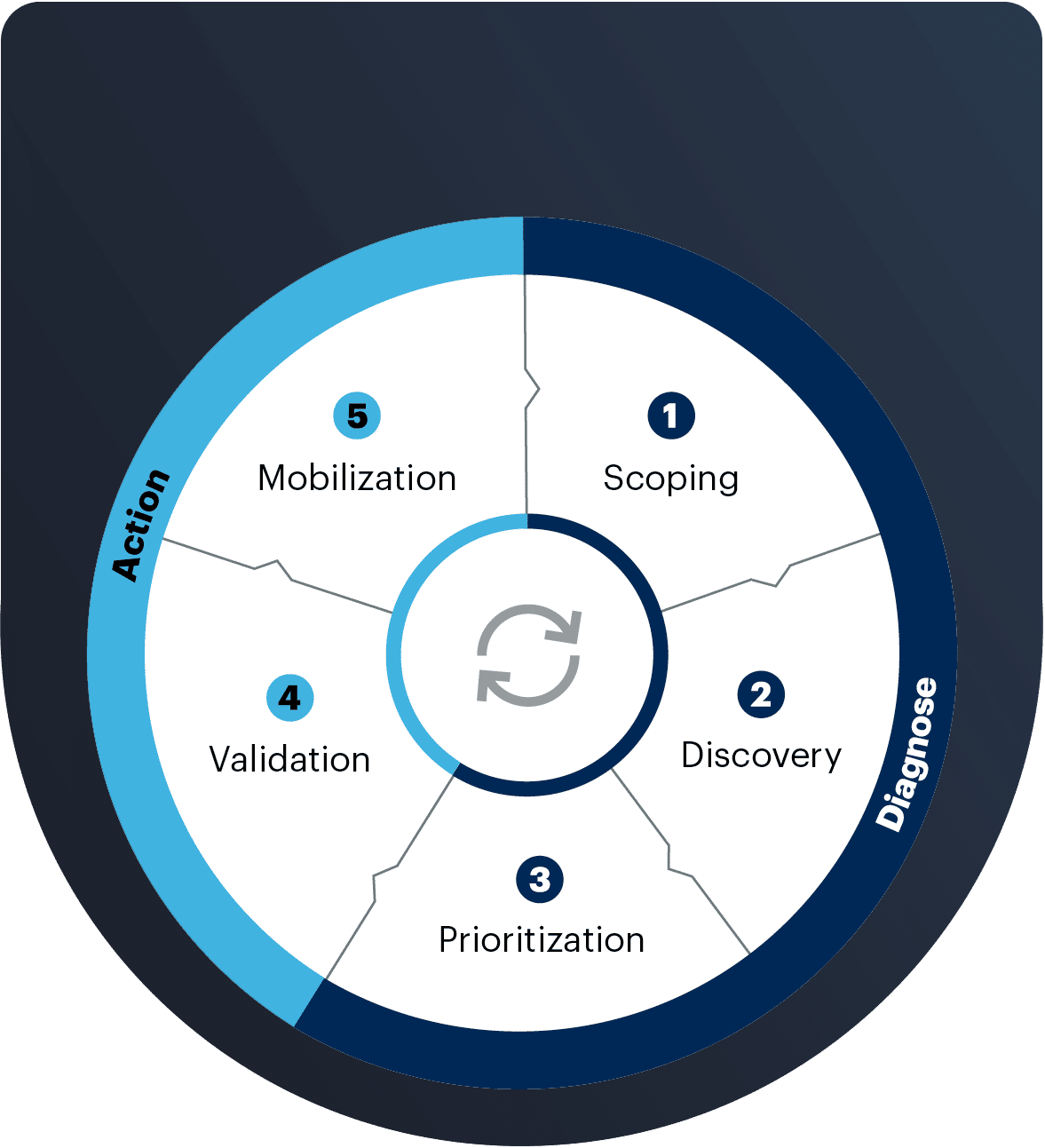
The framework—and how NodeZero gives you the fast-track
Gartner outlines a 5-stage cycle for CTEM, and while we agree with the intent behind each stage, we’ll show how NodeZero can streamline three of the stages in a big way.
👆 Click + Drag the Purple Bar
Stage 1: SCOPING
Gartner guidance:
“To define and later refine the scope of their CTEM initiative, security teams need first to understand what is important to their business counterparts, and what impacts (such as a required interruption of a production system) are likely to be severe enough to warrant collaborative remedial effort.”
Unlike vulnerability management projects, CTEM goes “beyond self-inflicted vulnerabilities and also takes the ‘attacker’s view,’ beyond the traditional common vulnerabilities and exposures (CVEs).” Scope should consider:
- Internal, on-prem, and owned assets
- External attack surface
- SaaS security posture
- Digital risk protection
- Dark and deep web sources
NodeZero approach
Scope your full infrastructure surface, on-prem, cloud and hybrid. You own the rules of engagement, scope, and unconstrained scheduling.
How NodeZero does it it:
- Full, autonomous infrastructure scoping of your production environment—known and unknown
- Per-test option to set scope or intelligently discover your environment
- Enrich assets with business context
- Findings available via API
Pairs well with
Complementary tools and compensating controls:
- CMDB
- SaaS discovery
- Network monitoring
- Network access control
- DSPM
Stages 2-4: DISCOVERY, PRIORITIZATION, VALIDATION:
Fast-tracked with NodeZero
Gartner guidance:
Discovery
Priority should be given to discovery in areas of the business that have been identified by the scoping process, although this isn’t always the driver.
Exposure discovery goes beyond vulnerabilities: it can include misconfiguration of assets and security controls, but also other weaknesses such as counterfeit assets or bad responses to a phishing test.
Prioritization
Prioritize the treatment of exposures based on a combination of the urgency, severity, availability of compensating controls, risk appetite and level of risk posed to the organization.
Confusion between scoping and discovery is often the first failure when building a CTEM program. The number of discovered assets and vulnerabilities is not success itself; accurate scoping based on business risk and potential impact is far more valuable.”
The goal of exposure management is not to try to remediate every issue identified nor the most zero-day threats, for example, but rather to identify and address the threats most likely to be exploited against the organization. Gartner goes on to guide organizations to “account for exploit prevalence, available controls, mitigation options and business criticality to reflect the potential impact.”
Validation
Validate how potential attackers can actually exploit an identified exposure, and how monitoring and control systems might react. The validation step should achieve three objectives, as stated by Gartner:
- Assess the likely “attack success’ by confirming that attackers could really exploit the previously discovered and prioritized exposures.
- Estimate the “highest potential impact” by pivoting beyond the initial footprint and analyzing all potential attack paths to a critical business asset.
- Identify if the processes to respond and remediate the identified issues can be both fast enough and adequate for the business.
NodeZero approach
Break down silos across these stages.
Prove what’s exploitable in production—and the business impact at stake. Know exactly what to fix and why.
How NodeZero does it:
- Autonomously take the attacker’s perspective, no pre-defined scripts or assumptions.
- Unlimited production testing with granular user controls for what to test, how often, when, and how aggressively
- Full suite of tests, from internal and external to IAM and segmentation
- Chains exploitable weaknesses together, maneuvering across your environment
- Maps weaknesses to impact with full visibility to attack paths to show our work—and equip you to replicate
- Priority scoring based on proven impact from production exploitation
Pairs well with
Complementary tools and compensating controls:
- Application Testing [SAST, DAST, IAST]
- SaaS testing
- Segmentation tools
- When you have compliance mandate: a vulnerability scanner
Stage 5: MOBILIZE
Gartner guidance:
Mobilize teams “to operationalize the CTEM findings by reducing friction in approval, implementation processes and mitigation deployments.”
NodeZero approach
Make—and verify—the right fixes, with precise threat detection while you’re still exposed.
How NodeZero does it it:
- Decoys intelligently placed on critical weaknesses during tests
- Precise, instructive, shareable fix actions and detailed reports
- Immediate fix verification with 1-click verify
- ITSM system integrations
Pairs well with
Complementary tools and compensating controls:
- Automated patch management
- SOAR (Security orchestration automation and response)
- Threat detection incidence response
- Data analytics platform
Our suggestions for CTEM
We’re thrilled with the momentum CTEM is gaining among security teams, and wholeheartedly believe in the goals. And? There are two meaningful ways we’d evolve the approach.
First: You don’t have to delay validation
As laid out above, we advise tackling discovery, prioritization, and validation in one fell swoop. Before NodeZero, there were two scale and cost barriers to this: manual penetration testing and inability to test in production. NodeZero solves both.
Modernize with autonomous penetration testing
Penetration testing is the gold standard for understanding true risk—but manual penetration testing simply can’t scale to meet the scope or frequency we all crave. With NodeZero, you get our expert attack team “in a box” so you can test your entire environment at regular intervals.
Test in production
Production testing has been a core principle of NodeZero from the start. We never want security teams to settle for simulated environments or a narrow sample of their environments.
A lot of security leaders are risk averse by nature and don't want to test against their production networks because they've been trained to not disrupt the business at any cost.
And that's a valid concern. However, what you lose in that process is actually understanding the real state of your production environment.”
- Naveen Sunkavally, Chief Architect, Horizon3.ai
Across more than 100K penetration tests, NodeZero has proven its three-pronged approach to making production testing practical:
- No exploits that will disrupt business are included
- All exploits that are “on” by default are extensively vetted to be production-safe
- Users have control to turn on more aggressive exploits when and where they choose
Second: Continuous exposure management demands unified insights
Perhaps implied in the CTEM framework, we’d like to see ongoing analysis and reporting as an explicit element of the cycle.
As you embrace a continuous approach, your reward is data—lots of it, from across your organization. When unified, it shows how you’re trending across exposure and operational KPIs so you know where to focus—and where your investments have paid off.
When paired with business context, this quickly becomes your storytelling superpower to create informed, aligned champions among your business stakeholders and leadership.
Accelerate your CTEM journey
As a framework, CTEM gives you a clear north star to work towards. The reward is continuously knowing where your risk lies, what to prioritize, and how to best take action cross-functionally.
The NodeZero platform accelerates your progress towards these goals with practical solutions that, while they challenge the status quo, are proven to elevate exposure management—and take <15 minutes to deploy to production. Book a personalized demo today to see the platform in action.