A Pentest Wednesday® Story
Every security leader knows about Patch Tuesday. But as attackers move faster and chain exploits together in hours (if not minutes), organizations are realizing patching is only part of the solution. What matters most is proving those fixes work in their own environments.
Here’s what that shift made possible for one U.S. manufacturer.
Outcomes at a Glance
- Cut critical vulnerability remediation from weeks to hours
- Reduced exposures from High to Medium in 40 days at a key site
- Eliminated 94 exploitable attack paths
- Achieved a 100% reduction in network-level compromise scenarios
- Standardized weekly internal and external testing with NodeZero
That’s the essence of Pentest Wednesday™: moving beyond vendor-driven updates to organization-driven validation. For one U.S. manufacturer, that transition became the difference between guessing and knowing.
Impact
A leading U.S. manufacturer, founded over 100 years ago, has long prided itself on resilience. As a key supplier of essential products across North America, the company soon realized that protecting its operations and reputation meant going beyond routine compliance requirements.
Manufacturing has been the most targeted industry for cyberattacks four years running, according to IBM, with ransomware, extortion, and data theft driving major losses. Despite years of investment in security, this manufacturer faced the reality of a sprawling network built over decades of operations and acquisitions.
Groups like Scattered Spider were proving that adversaries could bypass controls and weaponize misconfigurations in hours. Annual, point-in-time pentests were never going to keep pace.
Background
Like many organizations, this manufacturer relied on defensive technologies and annual pentests to meet compliance. The periodic pentest reports provided a snapshot in time but little proof of what really mattered. When introduced to continuous, offensive testing with NodeZero®, their first reaction was skepticism.
Horizon3.ai’s Customer Success team helped shift that perception through regular working sessions, walking through findings, validating fixes, and building a repeatable testing cadence. Instead of static reports, the manufacturer now had a cycle of action and verification.
“I am pleasantly surprised at how NodeZero has delivered on its promises. It’s really starting to show its value, and we’re now putting it in our tool belt as something we rely on weekly.” — Director of Technology Services, leading U.S. manufacturer
As testing expanded, NodeZero uncovered inherited risks across multiple sites, including through acquisitions. Miscommunication from asset owners had left issues undiscovered, from Active Directory misconfigurations to systems unpatched for nearly two years, and even misconfigured email gateways. These findings reinforced why point-in-time tests could never keep pace with modern threats.
Mitigation
The shift happened in July 2025 when Citrix Bleed 2 (CVE-2025-5777) was added to CISA’s Known Exploited Vulnerabilities list. Unlike a typical CVE that can sit in a patch queue, KEVs demand immediate action because exploitation in the wild is already confirmed.
Soon after receiving a Horizon3.ai Rapid Response Flare Alert, followed by outreach from their Customer Success Manager, the manufacturer launched a targeted Rapid Response test for the Citrix vulnerability shown below. Rapid Response lets customers quickly validate whether emerging vulnerabilities are truly exploitable in their own environments, without running a full pentest.
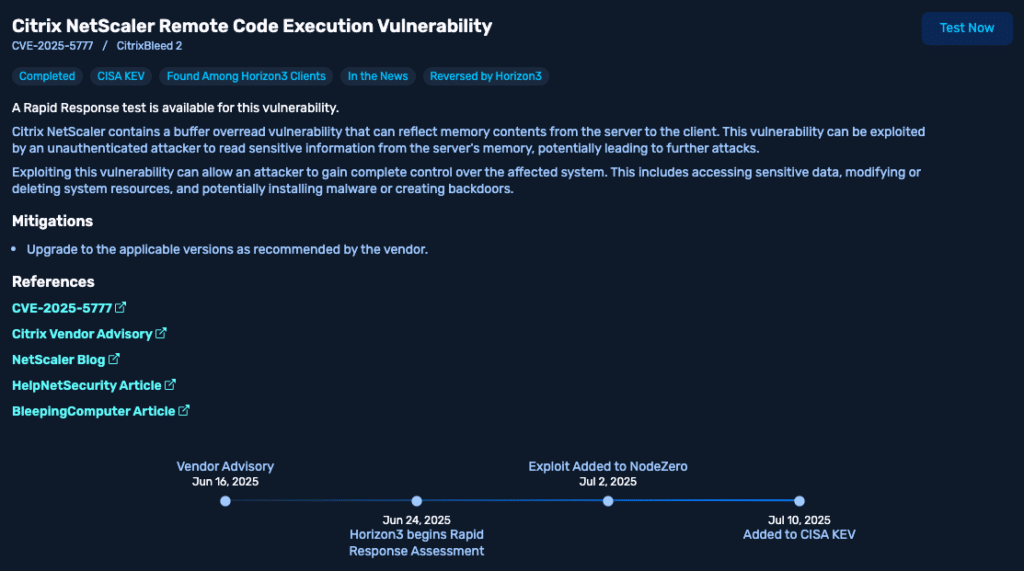
The test confirmed the customer’s Citrix implementation was exploitable. Because Horizon3.ai released the test on July 2, eight days before CISA added it to the KEV catalog on July 10, the customer was able to detect and fix the issue before the vulnerability became widely weaponized.
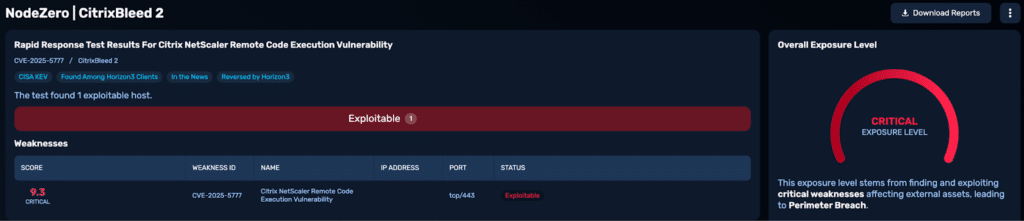
NodeZero confirmed the Citrix implementation was exploitable, resulting in a path to a full perimeter breach.
Within three hours, the team:
- Confirmed exploitation with NodeZero
- Applied the Citrix patch
- Retested and verified the exposure was closed
Attackers routinely sweep networks for KEVs within hours of disclosure. By detecting and fixing this one in a single morning, the team removed a highly exploitable opening.
It allowed the team to move decisively, turning a known exploitable risk into a confirmed remediation all in the same day.
Citrix Bleed 2 and the Limits of Patching
On July 10, 2025, CISA added Citrix Bleed 2 (CVE-2025-5777) to its Known Exploited Vulnerabilities (KEV) catalog after confirming active exploitation in the wild. Federal agencies were given 24 hours to patch affected Citrix NetScaler ADC and Gateway systems — underscoring how quickly regulators now expect organizations to respond.
For enterprises across industries, Citrix Bleed 2 highlighted a central issue: patching alone doesn’t prove risk is closed. Executives and regulators expect evidence that exposures are eliminated, not just assurances that patches were applied.
Groups like Scattered Spider were already exploiting Citrix Bleed 2 in ransomware campaigns, showing why continuous validation is essential to safeguard sensitive environments.
“We got the Horizon3.ai email early that morning saying we were likely at risk, and then your Customer Success Lead followed up to make sure we saw it, which was actually really cool. We then decided to start weekly external tests, which aligns with the best practices you mentioned.” — Director of Technology Services, leading U.S. manufacturer
Remediation
What began as uncertainty turned into a new operating model for the manufacturer:
- Weekly internal and external pentests established as standard practice
- Real-time validation of critical exposures, reducing remediation from weeks to hours
- Full coverage of every asset, with NodeZero used as an audit tool to track new and decommissioned systems
- Adoption of advanced features including Endpoint Security Effectiveness to validate endpoint controls and uncover blind spots, and Risk Based Vulnerability Management to tie scanner-identified vulnerabilities to real exploitability and business impact using attacker evidence.
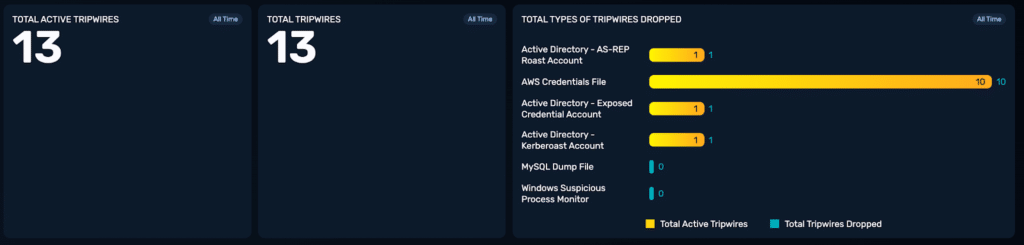
- Proactive deployment of NodeZero Tripwires™, placing more than ten on key network services and three within Active Directory. Tripwires monitor high-value assets and alert the team if attacker behaviors such as password spraying, lateral movement, or AD enumeration are detected.
“Most pentesting companies just say, ‘Here’s what’s wrong with your stuff, fix it, and leave.’ But you’ve been making sure everything is proper with the test itself, and then some.” — Director of Technology Services, leading U.S. manufacturer
Beyond the new testing cadence, the manufacturer also used NodeZero to support M&A security validation at its midwestern site. In just 40 days, they reduced exposures from High to Medium, eliminated 94 attack paths, and achieved a 100% reduction in network-level compromise scenarios.
NodeZero also surfaced risks that had gone unreported by network admins: from misconfigured Active Directory to systems left unpatched for years. These findings drove broader changes: analyzing vulnerability data through NodeZero’s Vulnerability Management Hub, strengthening identity defenses with ITDR testing, and enforcing new patch management protocols.
Today, the company isn’t just running tests. It’s using NodeZero as a strategic part of its security program.
Conclusion
For this manufacturer, the lesson was clear: patching is necessary, but proof is decisive. Moving from monthly to weekly testing created a culture of validation that pushed their security program beyond compliance and into resilience.
Patch Tuesday applies the fixes. Pentest Wednesday proves the risk is closed.

