Vulnerability management started with scanning — identify assets, fingerprint software, and match scan findings to known CVEs. Then came “risk-based” approaches that promised smarter prioritization. But in practice, most programs still just patch what scores the highest.
Risk is inferred, not proven. Fixes are assumed to work. And security teams are left guessing what actually matters.
Horizon3.ai is changing that.
With NodeZero®, we’ve redefined Risk-Based Vulnerability Management (RBVM) to focus on what attackers can actually exploit, what adversaries are actively using, and what happens when they succeed. Our model is grounded in proof, not prediction.
The Horizon3.ai RBVM Model
In terms of “Risk”, our approach is built on these three core principles:
- Exploitable Attack Surface – What can attackers actually compromise?
- Threat Actor Pressure – Which adversaries use those same techniques?
- Precise Business Impact – What happens when they succeed?
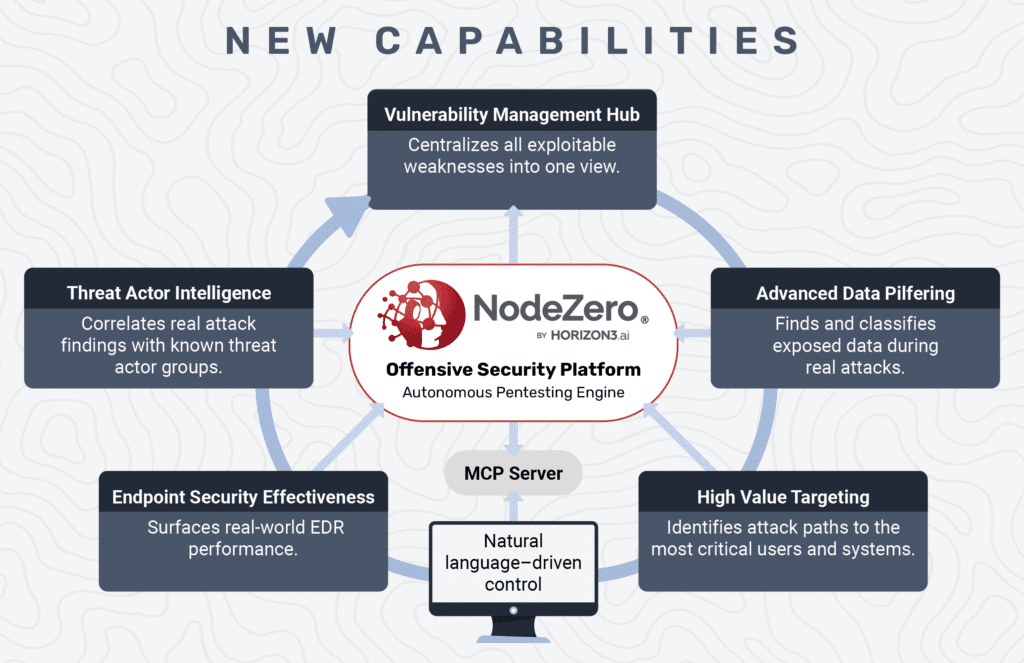
Six Capabilities — One Operational System
Horizon3.ai has just announced six new NodeZero capabilities that form a complete system for operationalizing Risk-Based Vulnerability Management. Under the three core principles mentioned above are the following:
NEW CAPABILITIES
Vulnerability Management Hub
Centralizes all exploitable weaknesses into one view.
Threat Actor Intelligence
Correlates real attack findings with known threat actor groups.

Offensive Security Platform
Autonomous Pentesting Engine
Advanced Data Pilfering
Finds and classifies exposed data during real attacks.
Endpoint Security Effectiveness
Surfaces real-world EDR performance.
MCP Server
↑Natural language–driven control
High Value Targeting
Identifies attack paths to the most critical users and systems.
Horizon3.ai’s approach isn’t just about improved prioritization. It’s a complete operational model for measuring, managing, and eliminating real-world risk. Let’s look a little closer at these new capabilities.
The Six New NodeZero Capabilities Explained
Endpoint Security Effectiveness (ESE)
Validates whether EDRs detect real-world attacker behavior like credential dumping, privilege escalation, and lateral movement in production.
Advanced Data Pilfering (ADP)
Finds, classifies, and validates sensitive, exploitable data using LLMs to assess what attackers can steal and how they’d use it.
Threat Actor Intelligence (TAI)
Correlates NodeZero’s discovered attack paths to known adversary TTPs (e.g., Cozy Bear, FIN7). Helps prioritize risk based on real-world threat alignment, not just CVEs.
High-Value Targeting (HVT)
Automatically identifies and tests access paths to crown-jewel users and systems with no tagging or manual tuning required.
Vulnerability Management Hub (VMH)
Only surfaces vulnerabilities and weaknesses proven to be exploitable through real attack paths, and tracks remediation with fix verification.
MCP Server (MCP)
Enables natural-language control of NodeZero for automating vulnerability remediation workflows. Trigger retests, query status, or launch new ops instantly, powering our closed-loop Find–Fix–Verify approach to mitigating risk.
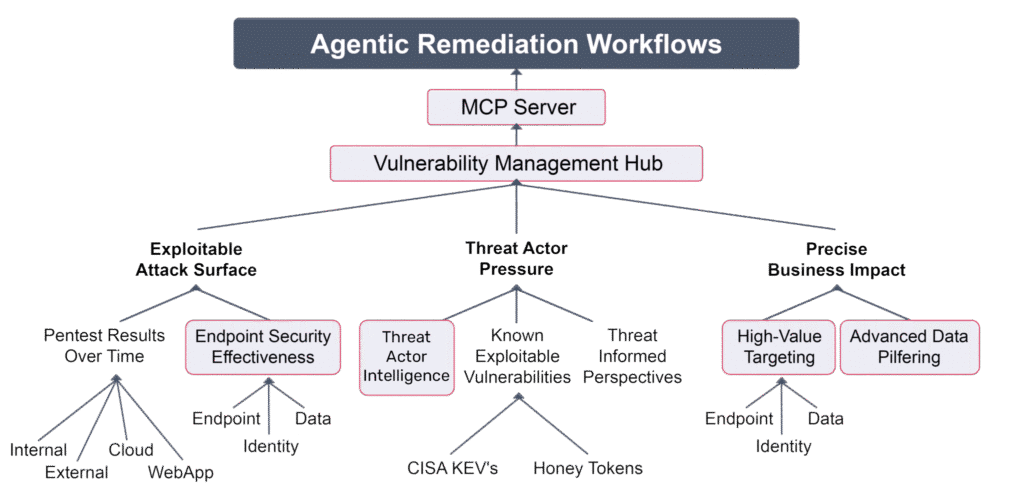
Capability Alignment: How They Map to the RBVM Model
| Core Principle | Capability | What It Answers |
| Exploitable Attack Surface | Endpoint Security Effectiveness | Are endpoint defenses working? |
| Precise Business Impact | Advanced Data Pilfering | What valuable data could be stolen? |
| Threat Actor Pressure | Threat Actor Intelligence | Who uses these tactics in the real world? |
| Precise Business Impact | High-Value Targeting | What matters most if compromised? |
| Consolidates discovered risks | Vulnerability Mgmt Hub | What has been exploited, not just detected? |
| Provides workflow automation | MCP Server | How do we automate remediation and verification? |
The NodeZero Find–Fix–Verify Loop
Traditional RBVM treats remediation as the finish line, assuming a patch was applied and calling the risk resolved. But assumptions don’t stop attackers.
NodeZero flips that model by anchoring every action in proof. It starts by showing what’s truly exploitable, guides remediation with full context, and only closes the loop when the risk is confirmed as “remediated”.
This loop isn’t theoretical. It’s the operational backbone of how modern security teams measure outcomes, validate fixes, and prove impact. Here are some more details about how this loop works:
1. FIND
NodeZero executes real attacks across your environment to uncover exploitable weaknesses, not just theoretical CVEs.
2. FIX
NodeZero delivers detailed remediation guidance, including business impact, and exploit context directly into tools like ServiceNow and Jira.
3. VERIFY
NodeZero re-runs the attack path. If the issue is still exploitable, it stays open. If not, the fix is confirmed, with full visibility and timestamped proof.
What a NodeZero Assessment Looks Like in Practice
This is how the six capabilities work together during a real-world NodeZero assessment:
- NodeZero performs an attack and gains access to a shared fileshare.
- Advanced Data Pilfering surfaces exposed credentials and financial documents.
- High-Value Targeting links the compromised identity to the Accounts Receivable group.
- Endpoint Security Effectiveness surfaces that EDR software is installed — but confirms it was bypassed during lateral movement to the domain controller.
- Threat Actor Intelligence shows that the attack sequence aligns with Cozy Bear tradecraft.
- NodeZero Tripwires™ are dropped on the compromised system to monitor for re-entry.
- Vulnerability Management Hub consolidates the full attack chain and opens a ServiceNow ticket.
- MCP Server triggers a 1-click retest after remediation is completed.
- NodeZero re-runs the attack to confirm the issue is resolved — Tripwires remain active.
*Note: Introduced in 2024, NodeZero Tripwires™ convert real pentest findings into targeted deception — deploying lures where intrusions are most likely. When touched, they deliver high-fidelity alerts with full context, turning offense into defensive detection.
Example RBVM Workflows in Production
Here are a few Find–Fix–Verify loop examples that are in production today:
- Credential Abuse
NodeZero exploits credential reuse → IAM rotates keys → MCP triggers retest - IaC-Driven Fix Loop
Cloud misconfig is exploited → Terraform PR is generated and redeployed → NodeZero confirms resolution - CISA KEV Validation
Exploited KEV is validated → Patch deployed → Retest confirms it is no longer vulnerable
What Security Teams Can Prove Now
Key benefits of the six new capabilities for stakeholders:
Security Leaders Uncover
- Which fixes reduced real-world risk
- Which tools failed under pressure
- Which findings matter to the business
SOC & Detection Engineers Learn
- Where detection gaps exist
- Which TTPs went undetected by EDR/SIEM
- Where Tripwires are deployed — and why
GRC & Audit Teams Discover
- What was exploitable with confirmed impact
- Which threats were aligned to attacker behavior
- Which controls were validated with proof
Horizon3.ai RBVM Starts Here
NodeZero isn’t just a pentesting tool. It’s an offensive security platform that helps you identify, reduce, and verify real-world risk across your exploitable attack surface, adversary behavior, and critical business assets.
If your RBVM program still relies on scanner exports and unverified fixes, it’s time to evolve.