As your attack surface continues to sprawl, penetration testing is still the gold-standard for understanding your exploitable risk – but only if:
- done at scale, continuously,
- supported by actionable fix guidance and verification, and
- with a unified view of all test data over time
If you’re evaluating pentesting solutions – SaaS based platforms to replace or augment manual penetration testing – here are the nine critical questions to ask to make sure your choice is as advanced as the threats you face:
1. Scale: Can the solution test your entire IP range seamlessly while maintaining operational stability?
Why it matters: Attackers see your enterprise as one interconnected system—not siloed boundaries.
Buyer beware of: automated penetration testing solutions that can’t scale to test your entire attack surface. They often hide this limitation behind suggestions to test in smaller segments, but this limits the fidelity of your tests.
Expect more: In contrast, NodeZero customers routinely pentest tens of thousands of IPs in a single test – even as much as 100K plus. This means comprehensive coverage that mirrors the attacker’s perspective.
Ask the vendor: Can you test 10,000+ IPs in production without impacting performance or test results?
2. Scope: Can the solution handle hybrid cloud environments, pivoting seamlessly between on-prem and cloud?
Why it matters: Just as they’ll look at your entire IP range, attackers will also take a holistic view of your infrastructure.
Buyer beware of: solutions that claim “cloud” but only run on a single VM within a VPC, leaving them unable to pivot across multi-cloud and hybrid cloud environments.
Expect more: An autonomous pentesting solution should freely navigate your hybrid environment. In a recent example, NodeZero started on-premises, discovered AWS keystore files in a shared drive, and gained access to the production cloud. This holistic approach ensures no blind spots.
Ask the vendor: How does your solution navigate across cloud and on-prem infrastructure?
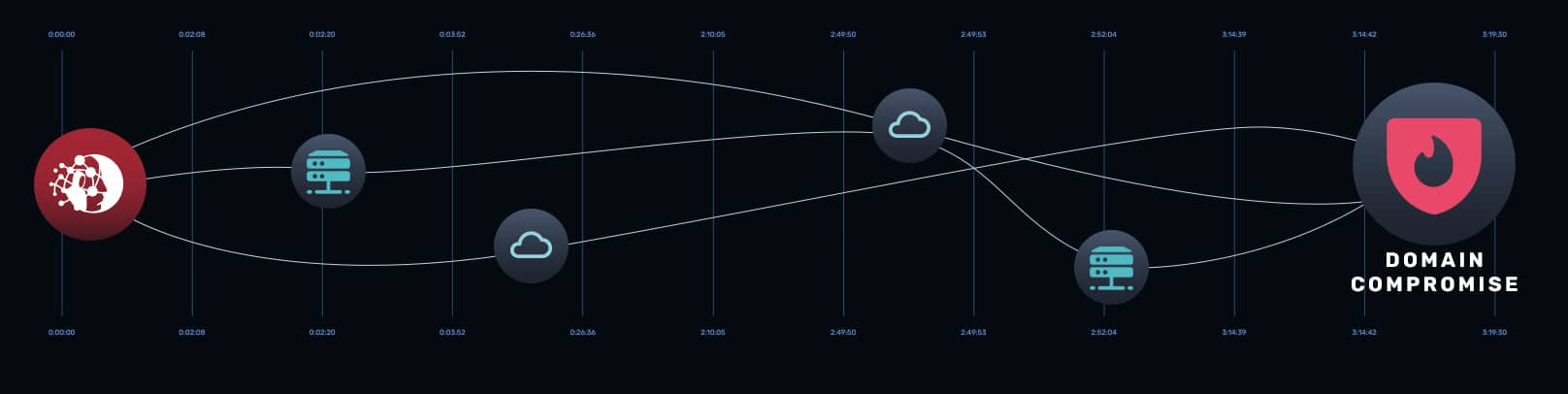
Image 1: NodeZero moving from on-premises to cloud.
3. Autonomous: does the solution dynamically adapt to what it discovers during tests?
Why it matters: To anticipate how an attacker might act, you (or rather, your SaaS pentesting solution) need to think like an attacker.
Buyer beware of: automated solutions that require predefined scripts and workflows: they’re static, lack context, and can’t discover novel or complex attack paths.
Expect more: NodeZero is autonomous (not just automated) which means it can make real-time decisions in response to what it discovers in your environment – just as an attacker would. It will move laterally and chain together multiple weaknesses to obtain critical downstream impacts.
Ask the vendor: What intelligent decision making is the solution capable of?
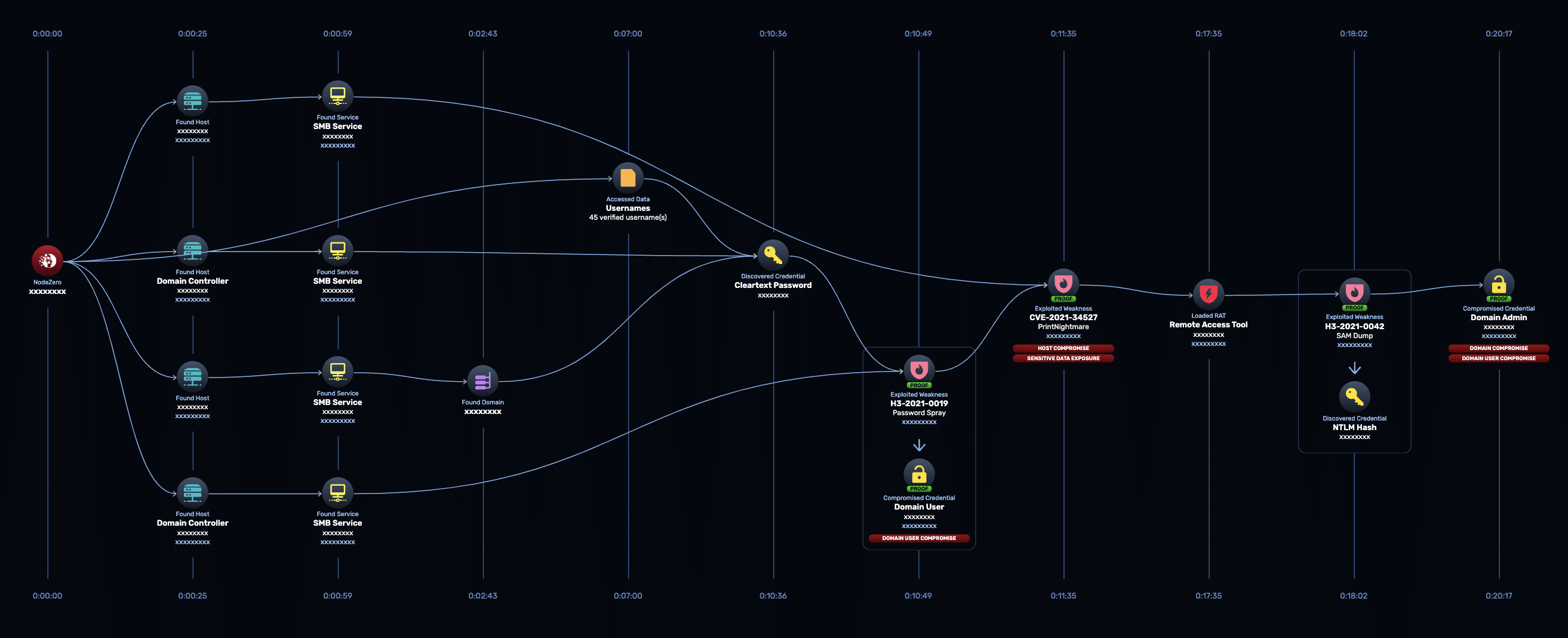
Image 2: NodeZero dynamically adapting to the environment, without following any pre-defined scripts.
4. Proof: Does the solution provide clear evidence of successful exploitation?
Why it matters: Thanks to the noise of vulnerability scanners, people just don’t trust the scan results of black box systems. To bring the right level of urgency to any risk mitigation, you need concrete proof of exploitation and downstream impacts – especially when you’re asking other teams to take action.
Buyer beware of: solutions that fail to provide actionable evidence, leaving you and/or the teams you partner with questioning the validity of findings.
Expect more: NodeZero delivers comprehensive proof for every successful exploit, including auditable logs of all commands run. This transparency makes you more credible to other teams and equips you to validate whether your security tools logged, detected, and responded to the activity – or missed it entirely.
Ask the vendor: What evidence do you give me for each successful exploitation?
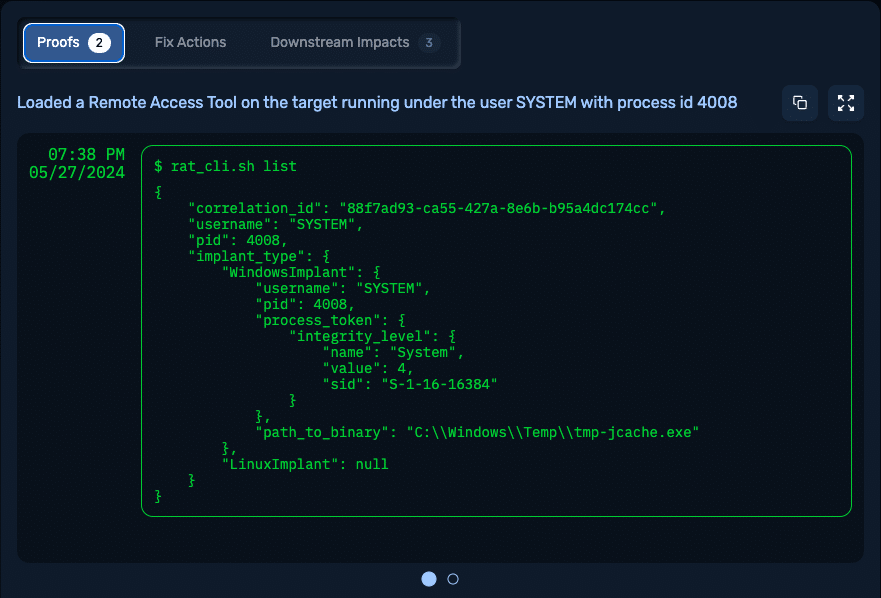
Image 3: NodeZero provides proofs for every successful exploitation.
5. Fix actions: Does the solution give you actionable remediation guidance?
Why it matters: Getting a diagnosis without a treatment plan isn’t very helpful. Same goes for knowing where you’re exploitable without knowing how to remediate.
Buyer beware of: solutions that don’t deliver in-depth, actionable guidance to fix the issues at hand.
Expect more: NodeZero provides precise, instructive fix actions for every exploited weakness. They’re developed by our world-class experts, but written to serve the folks on the hook for the fix: usually IT admins and network engineers, not highly credentialed security experts.
Ask the vendor: Do you provide remediation guidance and easy-to-follow fix actions? Will you please provide sample fix actions and remediation reports?
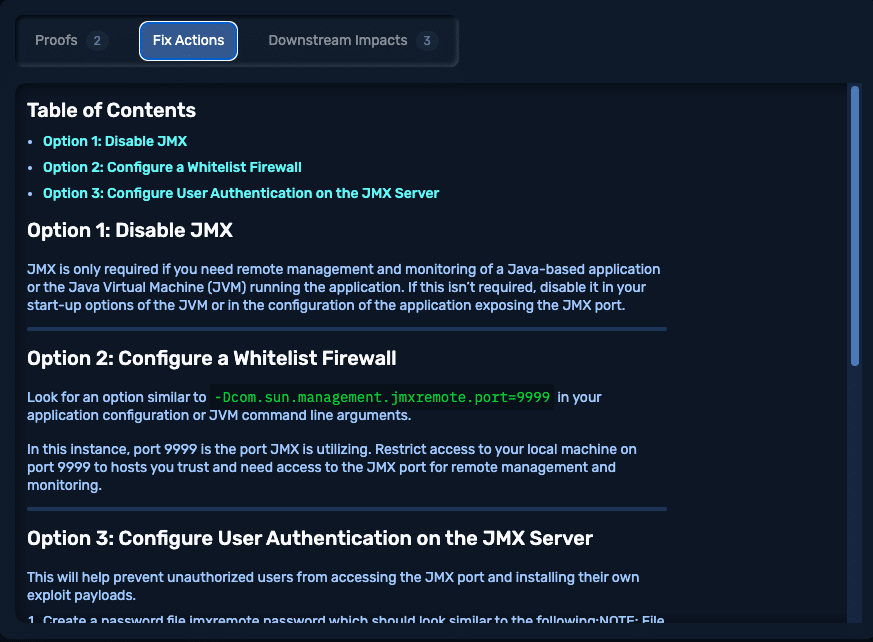
Image 4: NodeZero provides Fix Actions for every issue discovered.
6. Retesting: Can you quickly verify that issues have been mitigated or remediated?
Why it matters: Finding a weakness, making a fix, and crossing your fingers it was successful leaves you exposed – you need to verify.
Buyer beware of: automated pentesting solutions that equip you to test with more frequency, but don’t let you surgically test for the fix you just made – these leave inefficiency in your remediation processes.
Expect more: With NodeZero, users verify their fixes in minutes by running targeted retests right after remediation. They close tickets faster, improve mean-time-to-remediation, and free up valuable capacity.
Ask the vendor: How do I verify when a weakness is remediated? How long does this tend to take?
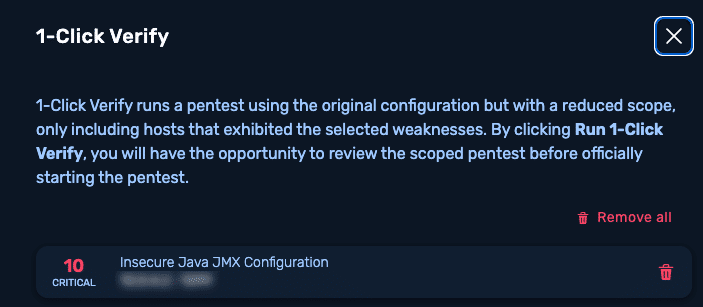
Image 5: NodeZero provides 1-Click Verify for quick retesting.
7. Detection: Can the solution deploy deception tools to detect ongoing threats?
Why it matters: The liability clock starts as soon as you’re aware of an exploitable weakness, and keeps ticking until you’ve made a successful fix.
Buyer beware of: solutions that don’t address the window of exposure, leaving you less prepared for persistent threats.
Expect more: With NodeZero Tripwires, simply check a box and we’ll strategically deploy HoneyTokens (e.g., fake AWS credentials, SQL dump files) onto the at-risk hosts or shares NodeZero has discovered.
This adds a layer of protection where you’re most vulnerable during the time you’re most vulnerable: before mitigation or remediation is complete. If triggered, alerts are sent directly to your SOC, along with historical pentest results, to accelerate incident response.
Ask the vendor: What does the solution offer to help cover the window of time between discovery and remediation?
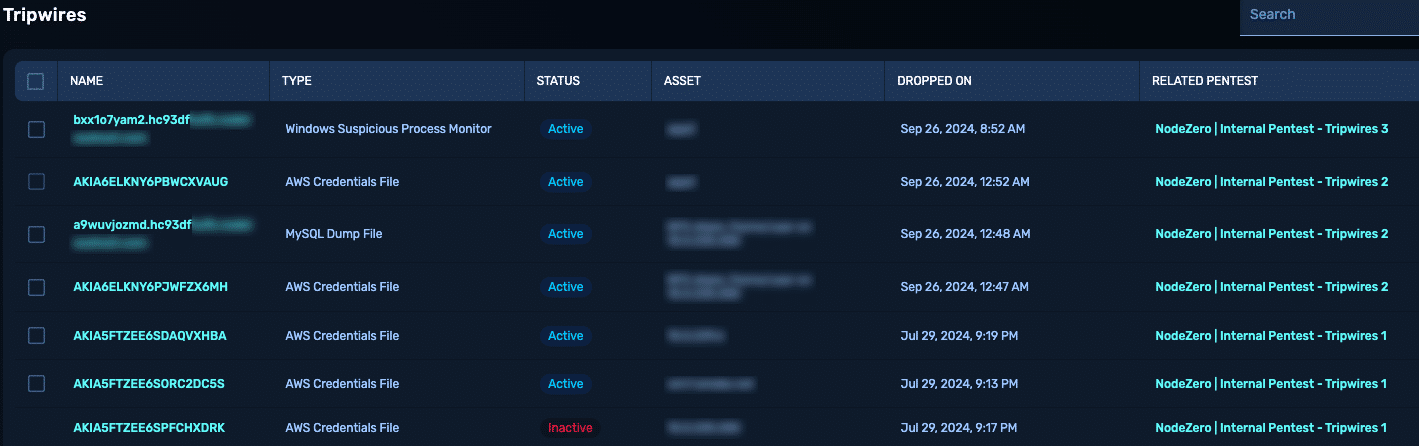
Image 6: NodeZero Tripwires deployed during pentests.
8. Early response: When new CISA KEVs (Known Exploited Vulnerabilities) emerge, how quickly can the solution adapt?
Why it matters: New CISA KEVs are prime targets for attackers who know you’re unlikely to have secured these nascent vulnerabilities—they’ll strike while the iron’s hot.
Buyer beware of: solutions without dedicated resources to quickly adapt their offerings to provide coverage against zero- and n-day threats.
Expect more: The team of world-class offensive security experts behind NodeZero Rapid Response integrates new exploits for CISA KEVs into the platform within hours. We’re often the first to weaponize and test for these emerging risks, giving our customers a critical edge.
Because NodeZero is a SaaS platform, customers can simply run a new test to know if they’re exposed, take action, and stay out of the news—to updates required.
Ask the vendor: In the past year, how quickly have you adapted to nascent threats like new CISA KEVs? What updates do customers have to make to access new exploits?
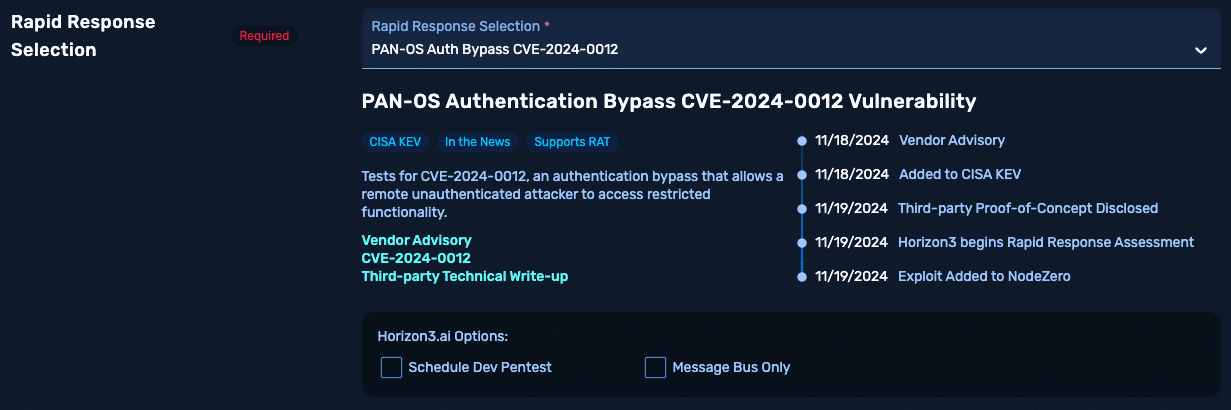
Image 7: NodeZero Rapid Response tests for CISA KEVs.
9. Unified analysis: How does the solution help me understand organization-wide testing data?
Why it matters: To make the best strategy decisions, you need to raise your vantage from individual tests to the big picture trends.
Buyer beware of: solutions that require you to manually aggregate data across tests and teams.
Expect more: NodeZero Insights gives security leaders a comprehensive view of their pentesting data so they can measure progress, better inform prioritization, and keep executive stakeholders informed with pre-built reporting.
Ask the vendor: What aggregate and trend data do you provide across all pentests we run?
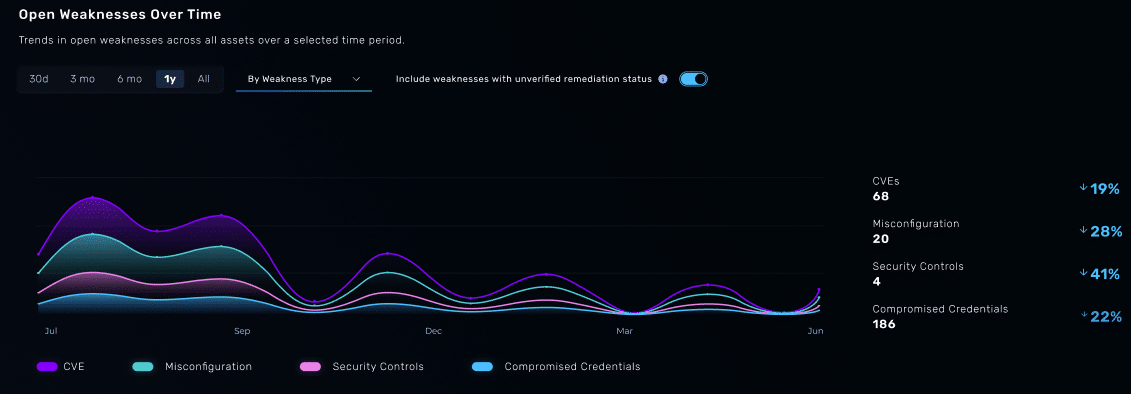

Image 8: NodeZero Insights open weaknesses over time.
Ask the tough questions, get the best pentesting solution for your stack.
As you evaluate your options, cut to the chase with these 9 questions, and you’ll come away with a solution that brings you more value. So go ahead, send these ahead of your vendor demo calls:
- Can you test 10,000+ IPs in production without compromise?
- How does your solution navigate across cloud and on-prem infrastructure?
- What evidence do you give me for each successful exploitation?
- What intelligent decision making is the solution capable of?
- Will you please provide sample fix actions and remediation reports?
- How do I verify when a weakness is remediated? How long does this tend to take?
- What does the solution offer to help cover the window of time between discovery and remediation?
- In the past year, how quickly have you adapted to nascent threats like new CISA KEVs?
- What aggregate and trend data do you provide across all pentests we run?
To dive deeper into how NodeZero addresses these—plus any other questions you have—schedule a demo with our team today.

