Endpoint Security Effectiveness
Get the Most Out of Your EDR Investment
EDRs are critical to stopping modern attacks — but most teams don’t know if theirs is working as intended. NodeZero® helps organizations get the most out of their EDR investments by safely executing real-world attack techniques in production. It reveals whether endpoint defenses detect, alert, or block behavior that matters — helping teams tune, validate, and improve coverage with evidence, not assumptions.
From coverage to consequence — mapped
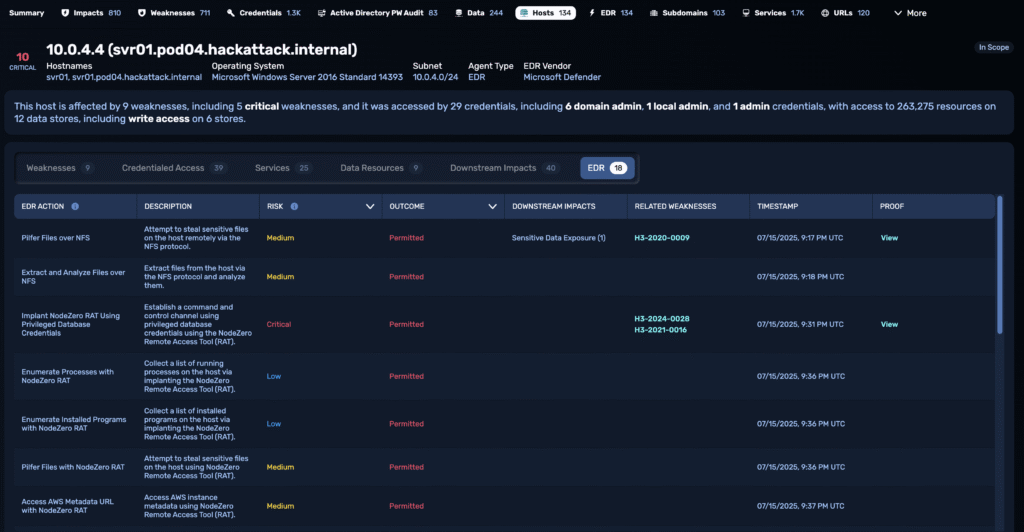
Endpoint Security Effectiveness shows exactly how your endpoint protections respond to real attack behavior. NodeZero checks for EDR presence on each host, then executes techniques ranging from credential theft to privilege escalation and lateral movement — all without breaking production. The results reveal blind spots, missed detections, and what happens when attackers slip through.
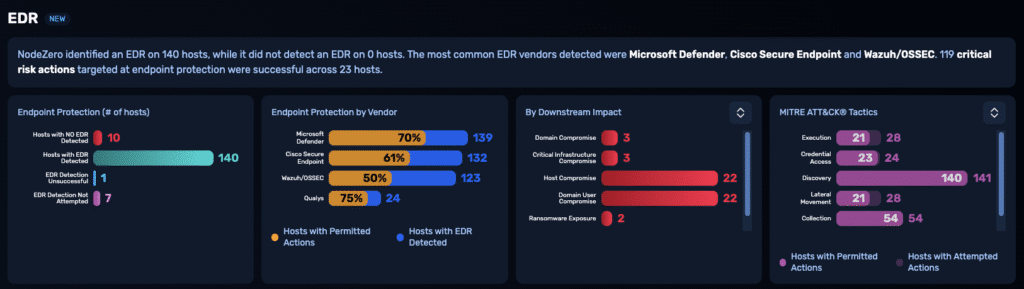
What the results actually tell you
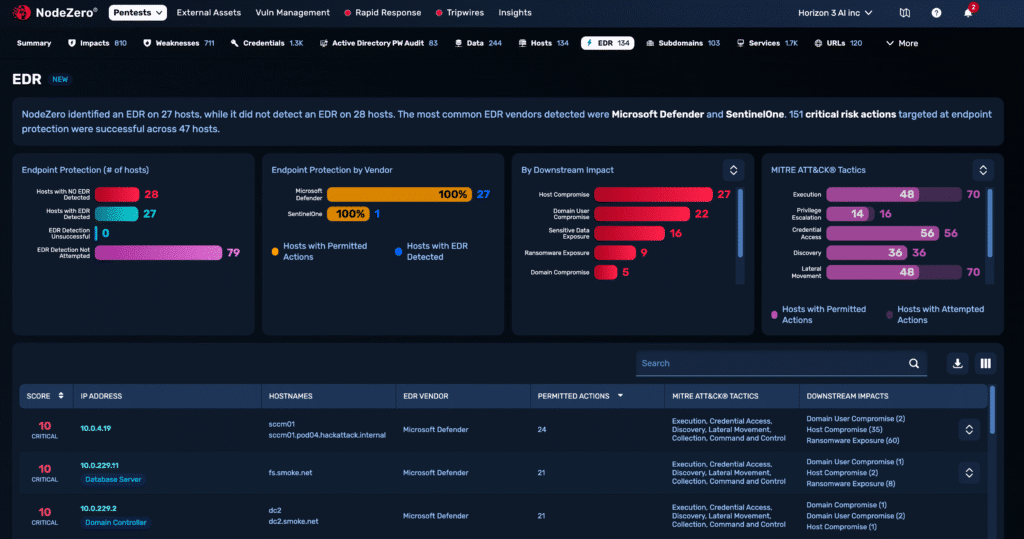
EDR deployment coverage
NodeZero identifies which hosts are missing endpoint protection entirely — or where deployments are misconfigured or stale.
Detection and prevention performance
On protected hosts, NodeZero executes techniques designed to trigger detection or blocking. It records whether each technique was logged, alerted, or stopped.
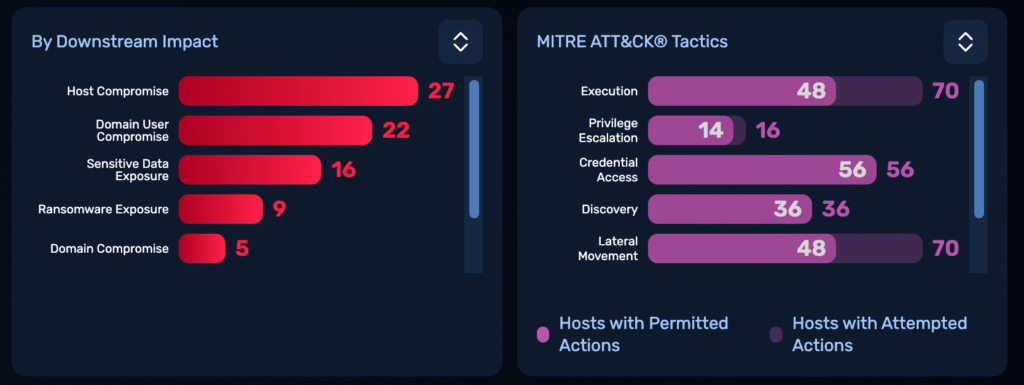
TTP-level granularity
Every NodeZero action is mapped to a MITRE ATT&CK TTP and labeled with outcomes – blocked or permitted – across real attack chains
EDR Visibility by Vendor
NodeZero correlates performance by EDR vendor and version. You can see where a given tool failed to detect credential dumping or lateral movement on a specific host.
EDR-specific performance insights
You can’t fix what you don’t test
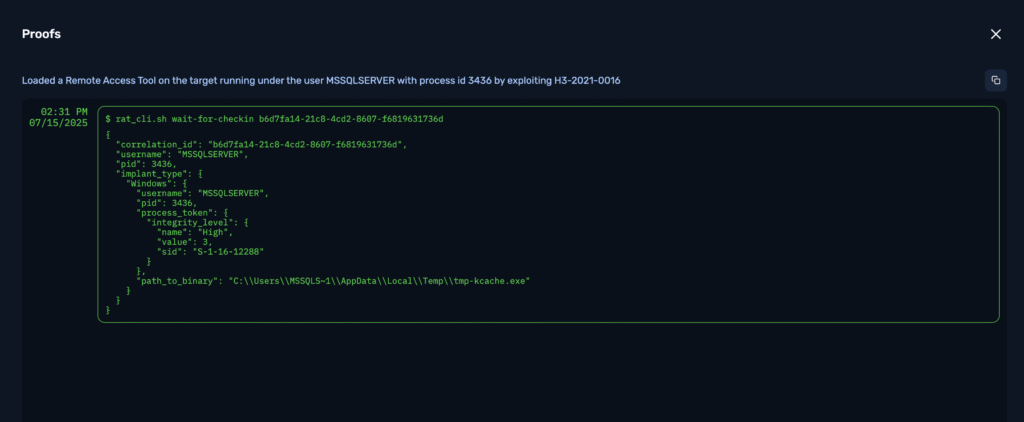
NodeZero validates endpoint defenses across real kill chains — not test payloads.
EDR effectiveness becomes measurable
Teams gain proof of what tools miss, down to the host and technique.
Tuning and escalation become easier
Provide your EDR vendor with test-backed data to support critical fixes and rule tuning.
Security investments become accountable
CISOs get hard evidence to back budget decisions, performance metrics, and control audits.