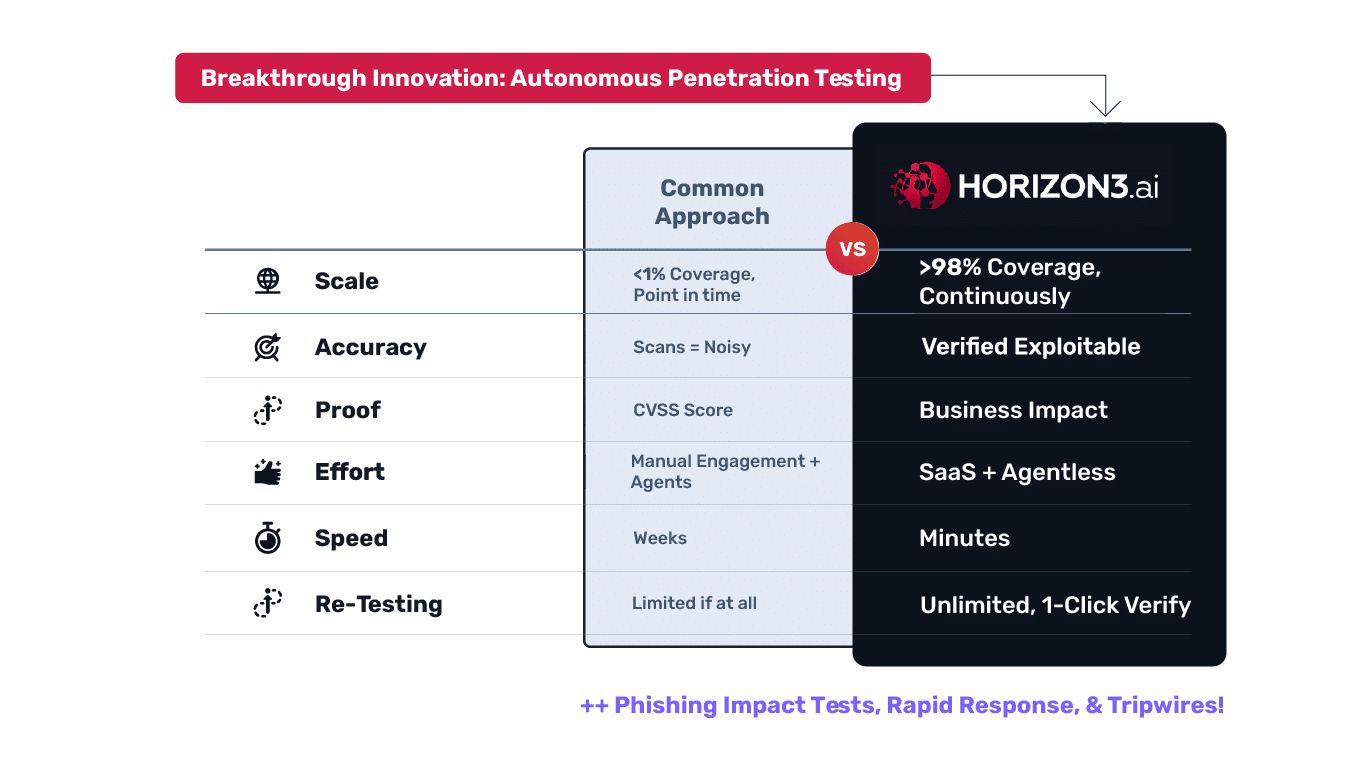
Fix what matters. Prove you’re secure.
Two Missions. One Platform.
Pentesters and red teams share a common goal: improving an organization’s security posture. But their objectives, scope, and methods differ. Pentesters focus on identifying as many vulnerabilities as possible within a defined environment, while red teams simulate real-world adversaries to test detection and response.
NodeZero® Offensive Security Platform helps both teams succeed by showing what’s truly exploitable. It’s the only autonomous pentesting platform that identifies real attack paths—so you can focus on what matters, cut through the noise, and continuously validate your security posture.
Penetration Testing
Goal: Identify as many vulnerabilities as possible within a targeted system or application.
Characteristics:
- Focused scope: Typically limited to a specific asset or environment (e.g., a web app or internal network)
- Short duration: Conducted over a few days or weeks
- Known engagement: The blue team is usually aware
- Compliance-oriented: Often tied to requirements like PCI-DSS or HIPAA
- Methodical process: Recon → Exploitation → Reporting
- Deliverable: A detailed report of vulnerabilities and recommendations
How NodeZero Adds Value:
- Acts as a force multiplier: test tens of thousands of assets in a single engagement, uncovering attack paths that chain weaknesses across on-prem and cloud environments.
- Accelerates host coverage: NodeZero applies a full library of attack content to every host, surfacing hard-to-find configuration drift or overlooked systems.
- Accelerates host coverage: NodeZero applies a full library of attack content to every host, surfacing hard-to-find configuration drift or overlooked systems.
- Delivers context and proof: Each finding includes full attack path visibility, the exact commands executed, and system responses.
- Validates actual exploitability: Move beyond CVE listings—see what an attacker could do right now.
- Enables frequent testing: Run tests daily, monthly, or after major changes. Slash cost-per-test.
- Speeds up reporting: Reports are generated automatically and accepted for compliance.
- Maps every action to MITRE ATT&CK: Show which techniques were used and where.
- Expands use cases: Measure EDR and SIEM visibility, validate SOC SLAs, and demonstrate risk reduction with before/after tests.
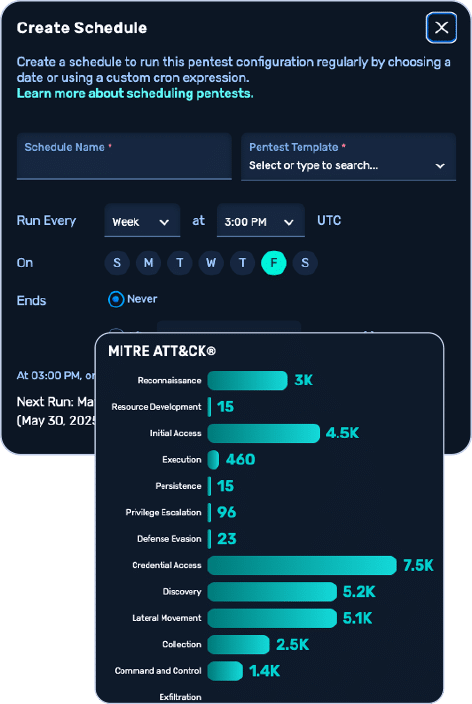
Red Teaming
Goal: Evaluate detection and response capabilities by emulating real-world adversaries.
Characteristics:
- Broad scope: Objective-driven (e.g., data exfiltration, domain admin)
- Extended duration: Often weeks to months
- Covert operations: The blue team is usually not informed
- Adversary simulation: Emulates real tactics, techniques, and procedures (TTPs)
- Outcome-driven: Measures resilience across the attack lifecycle
Horizon3.ai Value
- Execute autonomous red team operations on demand. Eliminate lag time—NodeZero runs in hours, not weeks. Identify and fix critical risks before attackers do.
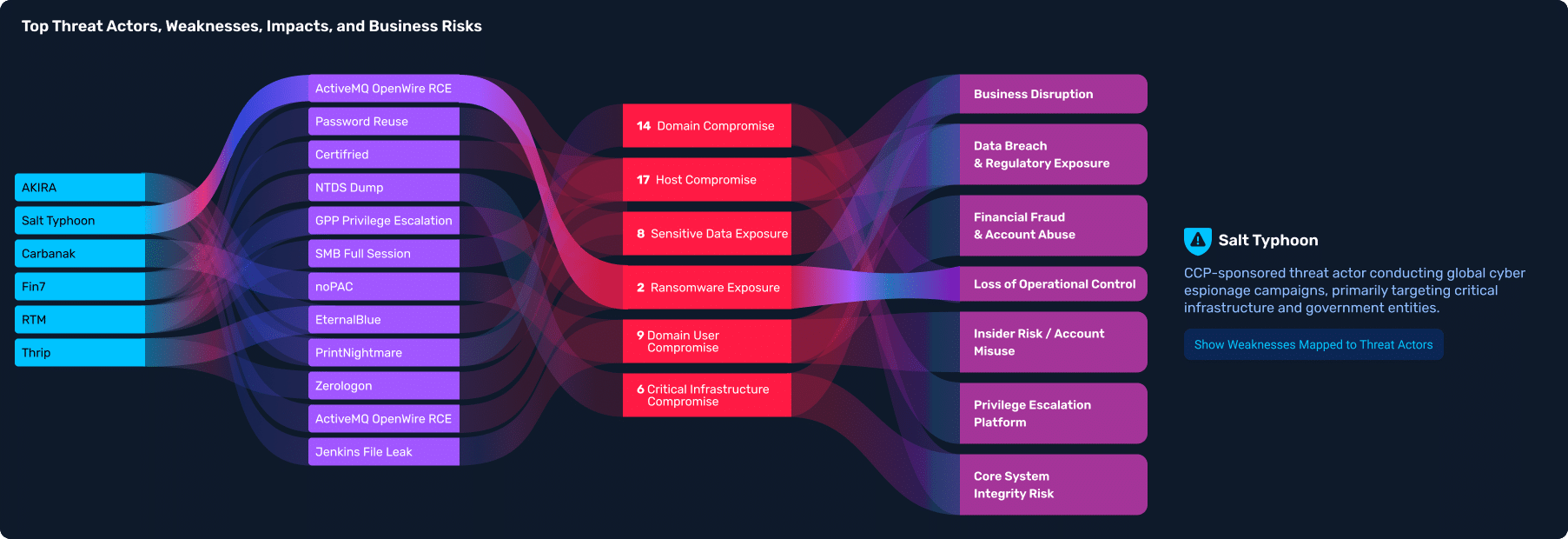
- Identify actual paths to crown jewels using real-world exploits. Discover lateral movement paths, privilege escalation opportunities, and domain compromise scenarios. Then, surface the root causes—misconfigurations, poor credential hygiene, and security tool gaps.
- See exactly what was found during the operation, prioritized by impact. Validate which vulnerabilities are actually exploitable, and replace CVSS-based guesswork with real, impact-driven prioritization.
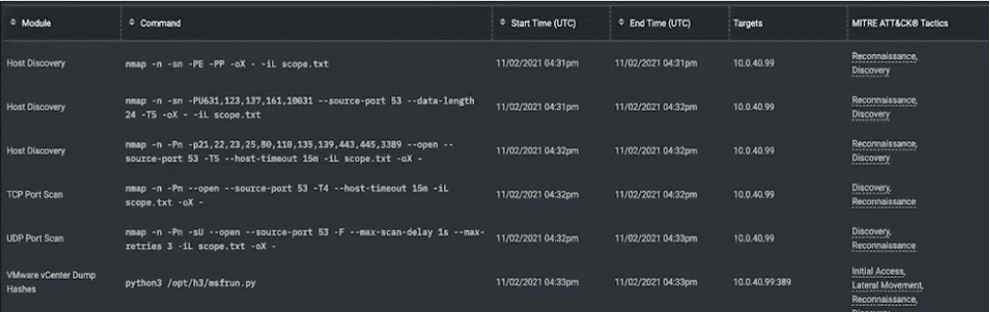
- Help tune detection logic based on real attack behavior. Reveal where your security tooling failed to detect or block malicious activity, and validate your incident response workflows and containment procedures. Test SOC alerting capabilities, perform log correlation for missed detections, adjust your tooling, and re-test.
- Phishing integrations show blast radius when credentials are phished
- Identity-based tests uncover different attack vectors
- Deliver audit-ready narratives that demonstrate security posture over time
- Deliver before/after testing to measure and prove risk reduction
- Reduce patching workload by 60–80% by focusing only on exploitable vulnerabilities
- Validate compensating controls ahead of audits
- Integrate with existing vulnerability management workflows to speed up remediation cycles
- Improve mean time to respond (MTTR) and detection fidelity using real attacker telemetry
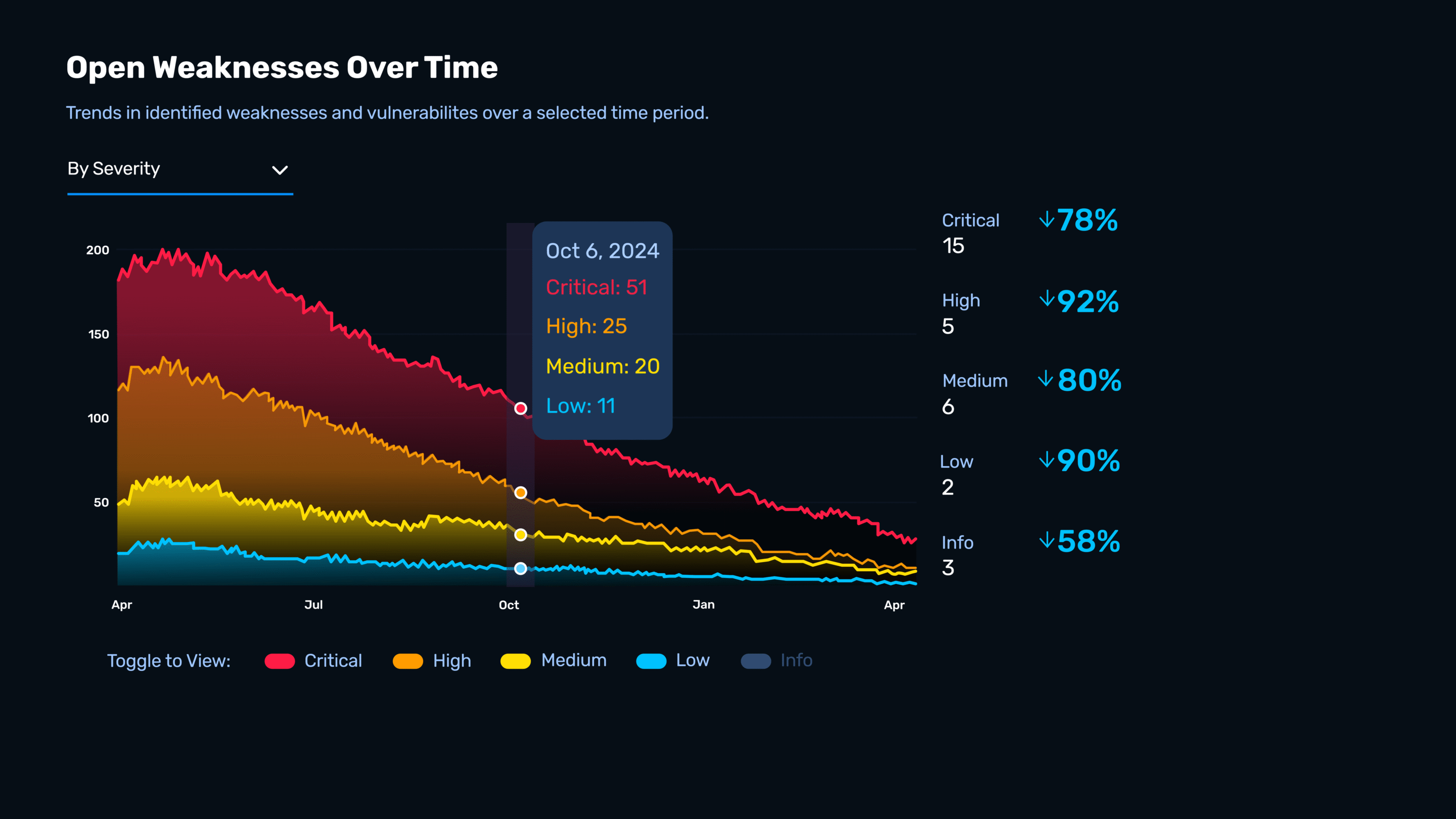
What Customers Ask—and What NodeZero Delivers
“We’re too busy to evaluate another tool.”
→ NodeZero is autonomous—no agents, no manual lift. Most teams get meaningful results within hours of first deployment.
“How is this different from BAS or attack simulations?”
→ BAS tells you what might happen. NodeZero shows you what can actually happen—today, in your environment, using real exploits.
“We don’t have the headcount to manage this.”
→ NodeZero doesn’t flood your queue. It tells you what matters most, why it matters, and how to fix it. Most tests consolidate thousands of vulnerabilities into 2–5 critical attack paths.
“Is it safe to run in production?”
→ Yes. NodeZero was built to run in live environments. You control the scope and set guardrails. It’s been run over 100,000 times in healthcare, finance, and manufacturing—with zero downtime.
“We already run annual pentests.”
→ Annual tests are like doing a fire drill once a year. The threat landscape shifts every week. NodeZero keeps pace by letting you test continuously.