Credential Attacks

Attackers Don’t Hack In… They Log In.
Credential attacks are a critical enabler for ransomware, costing businesses over $10 billion in the past five years
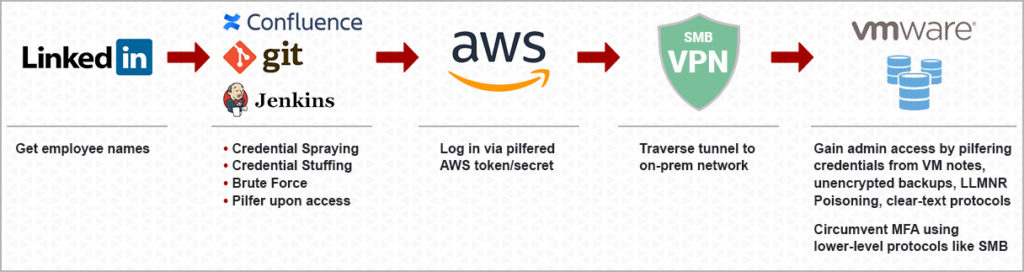
The Password Pandemic
Defense Alone Isn’t Enough. Fix What Matters.
Credential attacks are growing more sophisticated and more costly. Are you ready to see your vulnerabilities from the attacker’s perspective?
Get a Demo of NodeZero®
Find out how Horizon3.ai can uncover your weaknesses—and empower you to fix them before attackers exploit them.
