CVE-2026-1281 & CVE-2026-1340
Ivanti Endpoint Manager Mobile | Actively Exploited Remote Code Execution
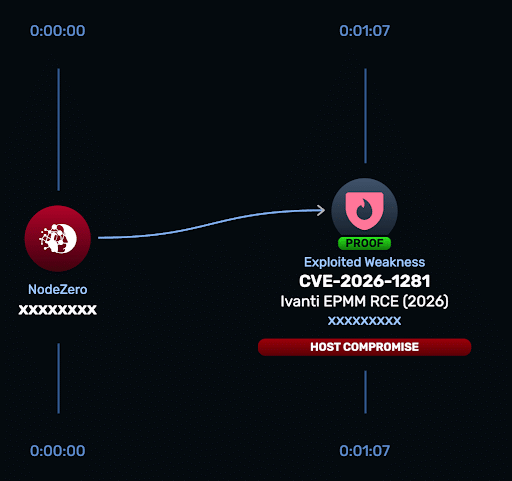
CVE-2026-1281 and CVE-2026-1340 are critical code injection vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM). The vulnerabilities allow unauthenticated remote code execution via specially crafted HTTP requests. Both carry a CVSS v3 score of 9.8.
Ivanti confirmed that these vulnerabilities have been actively exploited as zero-days in the wild. CVE-2026-1281 has been added to CISA’s Known Exploited Vulnerabilities catalog. Organizations running exposed or unpatched EPMM instances should treat this as an immediate risk.
Successful exploitation allows an attacker to execute arbitrary code on the vulnerable system, potentially leading to full compromise of the EPMM appliance, unauthorized access to managed mobile devices and enterprise data, and lateral movement into connected systems.
Technical Details
The vulnerabilities stem from improper handling and validation of HTTP requests within Ivanti Endpoint Manager Mobile. Specially crafted requests can trigger remote code execution without authentication.
Attack characteristics:
- Attack vector: Network
- Authentication required: None
- User interaction: None
- Impact: Remote code execution
- CVSS v3 score: 9.8
- Exploitation status: Actively exploited
Because EPMM often manages corporate devices, credentials, VPN access, and enterprise applications, compromise can have cascading downstream impact across identity systems and internal infrastructure.
NodeZero® Offensive Security Platform — Rapid Response
To safely verify if CVE-2026-1281 and CVE-2026-1340 affect Ivanti EPMM instances, Horizon3.ai customers can take advantage of the newly released Rapid Response test to confirm exploitability and remediation after patching.
- Run the Rapid Response test — Launch the Ivanti EPMM CVE-2026-1281 & CVE-2026-1340 Rapid Response test from the customer portal to assess internet-facing and internal EPMM instances for exploitable RCE exposure.
- Apply mitigation immediately — Follow Ivanti’s security advisory guidance and apply the appropriate RPM update based on your installed version. Customers should apply either RPM 12.x.0.x or RPM 12.x.1.x depending on their version. Only one RPM is required per version.
- Re-run the Rapid Response test — Validate that exploitation is no longer possible and confirm mitigation has effectively removed exposure.
Rapid Response helps security teams focus on vulnerabilities attackers are actively targeting, allowing prioritized action based on validated exposure.
Indicators of Compromise
Ivanti has published detection guidance, including log review and regular expression-based detection methods, in its advisory. Organizations should monitor for:
- Suspicious or malformed HTTP requests targeting EPMM services
- Unexpected process execution on EPMM hosts
- Unauthorized configuration changes within the EPMM console
- Unusual outbound network connections originating from EPMM servers
Given confirmed exploitation, exposed systems should be reviewed for compromise immediately.
Affected Versions
- Ivanti Endpoint Manager Mobile versions 12.5.0.0 and prior
- Ivanti Endpoint Manager Mobile versions 12.5.1.0 and prior
- Ivanti Endpoint Manager Mobile versions 12.6.0.0 and prior
- Ivanti Endpoint Manager Mobile versions 12.6.1.0 and prior
- Ivanti Endpoint Manager Mobile versions 12.7.0.0 and prior
Fixed Versions / Mitigation
- Mitigation: Apply the appropriate RPM update as outlined in the Ivanti Security Advisory. Customers must apply either RPM 12.x.0.x or RPM 12.x.1.x depending on their installed version. The RPMs are version-specific, not vulnerability-specific.
- Permanent fix: A full fix is expected in product release version 12.8.0.0, scheduled for release in Q1 2026.