CVE-2025-20362
CVE-2025-20333
CVE-2025-20363
Cisco ASA / FTD WebVPN Vulnerabilities
According to the Recent Cisco Advisory:
“On November 5, 2025, Cisco became aware of a new attack variant against devices running Cisco Secure ASA Software or Cisco Secure FTD Software releases that are affected by CVE-2025-20333 and CVE-2025-20362. This attack can cause unpatched devices to unexpectedly reload, leading to denial of service (DoS) conditions. Cisco strongly recommends that all customers upgrade to the fixed software releases that are listed in the Fixed Software section of this advisory.” Patch and verify your remediation with Rapid Response test ASAP.
Latest News: Cisco Warns of New Firewall Attack Exploiting CVE-2025-20333 and CVE-2025-20362
Multiple critical vulnerabilities in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) WebVPN components are being actively exploited. CVE-2025-20362 is an unauthenticated authorization bypass that can be chained with CVE-2025-20333 to achieve remote code execution as root. CVE-2025-20363 is a related unauthenticated RCE impacting ASA/FTD (and some IOS components).
Cisco and CISA report active exploitation and widespread scanning; CISA issued Emergency Directive 25-03 on September 25, 2025. A Rapid Response test for these issues launched October 9, 2025.
Technical Details
- CVE-2025-20362 – WebVPN Auth Bypass: Crafted HTTP(S) requests can reach restricted endpoints without authentication. This vulnerability alone doesn’t execute code but enables access to sensitive paths for chaining.
- CVE-2025-20333 – WebVPN Remote Code Execution: Attackers with credentials—or who exploit CVE-2025-20362—can send malicious HTTPS requests that execute arbitrary code as root.
- CVE-2025-20363 – Web Services RCE: Separate flaw that allows arbitrary code execution without authentication in ASA/FTD and with an authenticated user in some Cisco IOS components.
- Affected Versions: Cisco ASA 9.16–9.23; Cisco FTD 7.0–7.7. Validate specific software images against Cisco advisories.
- Threat Context: Cisco and CISA attribute ongoing exploitation to the same actor behind ArcaneDoor (UAT4356), a state-sponsored espionage campaign first observed in 2024.
Mitigations
Immediate Actions
- Patch or upgrade to Cisco’s fixed releases immediately.
- Restrict or disable devices if upgrades aren’t available or not immediately possible.
- Isolate and investigate any potentially compromised devices.
Follow Cisco’s guidance to detect attacks or use CISA’s Malware Next Generation to hunt for threat actor presence. If your ASA or FTD devices are exploitable by CVE-2025-20362, they’re exploitable by the others. Treat this as a drop-everything-and-patch-now scenario.
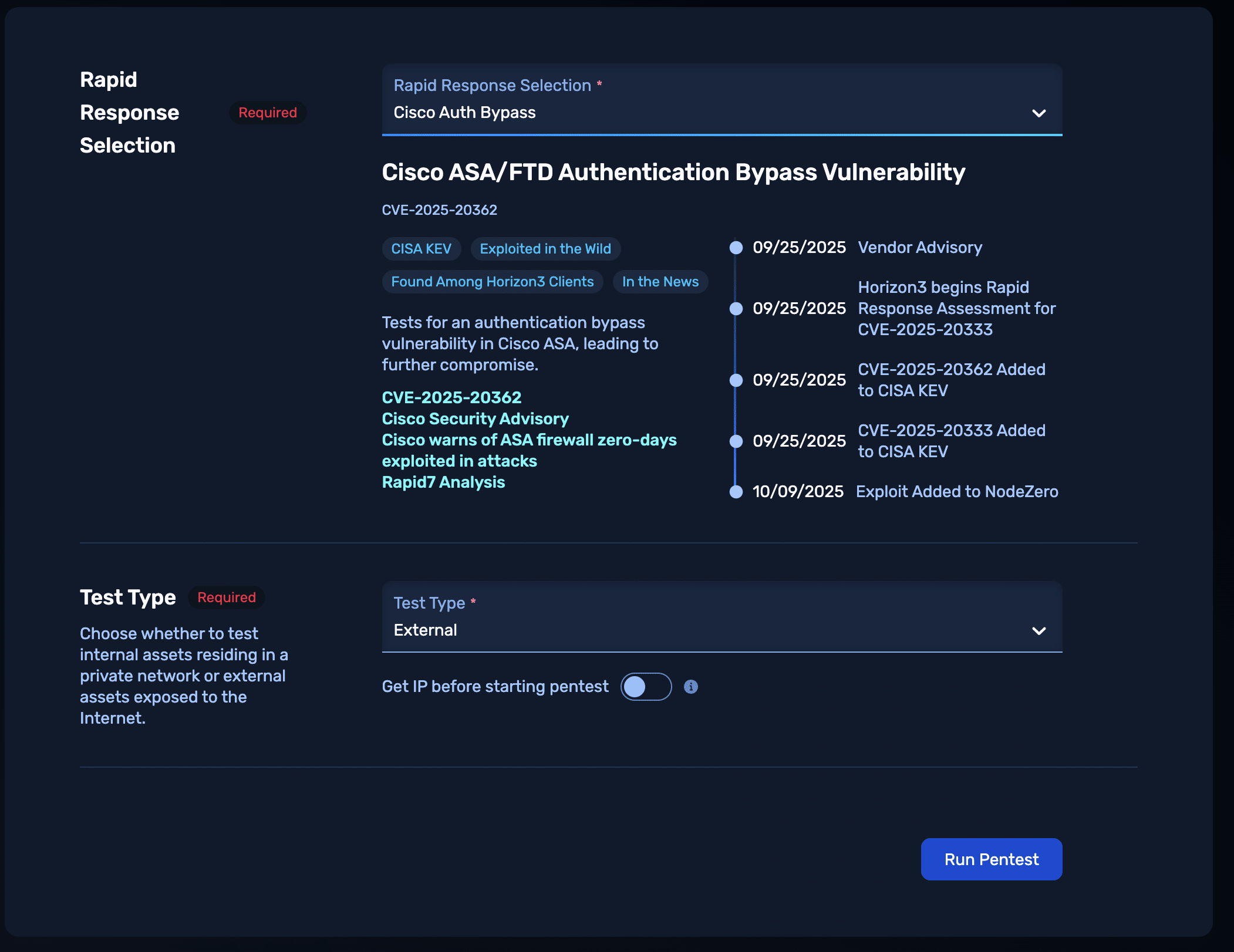
NodeZero® Offensive Security Platform — Rapid Response
The Cisco ASA / FTD Rapid Response test enables customers to safely verify exploitability and confirm remediation success.
Run the Rapid Response test from the customer portal to determine whether any internet-facing or internal Cisco ASA or FTD devices are exploitable.
Patch immediately — apply Cisco’s fixed releases for ASA versions 9.16–9.23 and FTD versions 7.0–7.7.
Re-run the Rapid Response test to confirm that the applied patches and/or configuration changes eliminated exploitability and close the loop on remediation.
Get exploitability results fast from Rapid Response test
References
🔗 CISA Emergency Directive 25-03
🔗 Cisco Advisory: CVE-2025-20362

