CVE-2025-11250
ManageEngine ADSelfService Plus Authentication Bypass
Reversed by Horizon3.ai
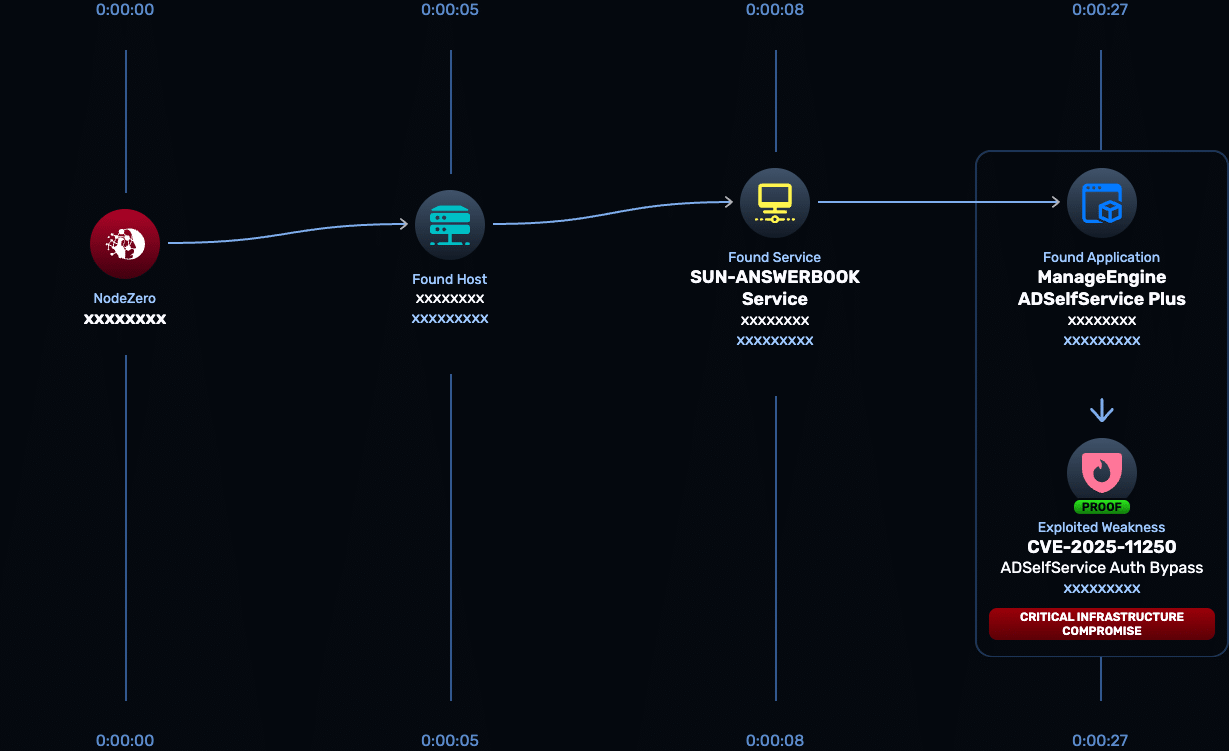
CVE-2025-11250 is a critical vulnerability in ManageEngine ADSelfService Plus that allows unauthenticated attackers to gain unauthorized access to the application. ManageEngine confirmed the issue and released a fix in ADSelfService Plus Build 6519 on October 1, 2025.
ADSelfService Plus is commonly deployed as an identity front end for Active Directory password resets, account unlocks, SSO, and MFA enrollment. Compromise of this system exposes identity workflows attackers can directly abuse for credential access and lateral movement.
Technical Details
- Vulnerability type: Authentication bypass. ManageEngine does not disclose technical exploitation details in the advisory.
- Attack preconditions: No authentication required. Exploitation enables unauthorized access to ADSelfService Plus functionality.
Horizon3 analysis: Internal research determined the issue stems from improper filter handling that allows spoofed requests to bypass authentication controls.
NodeZero® Offensive Security Platform – Rapid Response
A Rapid Response test for CVE-2025-11250 was launched in January 2026 to help organizations quickly determine whether ADSelfService Plus instances are exploitable and to validate remediation after patching.
- Run the Rapid Response test: Identify exploitable internal and internet-facing ADSelfService Plus instances.
- Patch immediately: Upgrade to ManageEngine ADSelfService Plus Build 6519 or later, as directed by the vendor.
- Re-run the Rapid Response test: Confirm that authentication bypass is no longer possible after upgrading
If exploitability is confirmed, treat this as a compromise of identity infrastructure. Review identity-related logs, enrollment changes, and downstream authentication events for signs of abuse.
Indicators of Compromise (for hunting)
| Indicator | Type | Description |
| Unauthenticated access to protected ADSelfService Plus endpoints | Network / Web | Look for successful requests reaching authenticated application paths without valid sessions. |
| Unexpected password resets, unlocks, or MFA enrollments | Identity | Review identity logs for actions without corresponding legitimate user authentication. |
| Account creation or unlock events without user interaction | Identity | Prioritize events enabling attacker-controlled access. |
| Anomalous downstream AD authentication activity | Identity / AD | Hunt for lateral movement using credentials originating from ADSelfService Plus workflows. |
Affected Versions & Patch
- Affected: ManageEngine ADSelfService Plus Build 6518 and earlier.
- Fix: Upgrade to Build 6519 (released October 1, 2025) or later.
Recommended actions:
- Inventory all ADSelfService Plus deployments and confirm build versions.
- Upgrade any instance running Build 6518 or earlier.
- Restrict access to ADSelfService Plus to trusted networks where possible.
- Run the Rapid Response test before and after patching to confirm exploitability is eliminated.
- Review identity and authentication logs for signs of abuse.
CISA KEV status
At the time of publication, CVE-2025-11250 is not yet listed in the CISA Known Exploited Vulnerabilities (KEV) catalog.
However, ADSelfService Plus has been previously targeted by threat actors, including advanced actors exploiting earlier vulnerabilities to gain access to government and enterprise environments. Given the product’s role in identity and authentication workflows, authentication bypass vulnerabilities in ADSelfService Plus historically see rapid attacker interest once public.
Organizations should treat this vulnerability as high risk and prioritize patching and verification accordingly, rather than waiting for KEV inclusion.