Advanced Data Pilfering
Use NodeZero® to pilfer data-at-risk as a top attacker
Advanced Data Pilfering (ADP) autonomously discover credentials hidden in data stores and contextualizes pilfered data based on risk level during internal pentests, phishing, and insider threat scenarios. ADP autotags findings with clear risk categories and surfaces them across NodeZero findings, reports, and attack graphs.
What’s happening behind the scenes
Autonomously discover and auto-tag data-at-risk
Classify business risk with GenAI reasoning
Connect data-at-risk to attacker prioritization
Validate exfiltration safely
Surfaces risk across your workflows
Context that turns exposure into risk
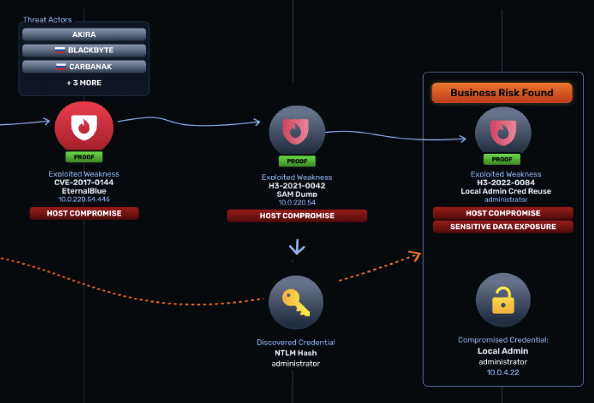
Organizations know data is exposed but lack clarity on which exposures create board-level risk. Traditional tools flood teams with regex-based noise and ignore attacker context. ADP eliminates this gap linking sensitive data exposures to exploit paths, identifying actionable prioritization and giving executives clear, business-level evidence. Organizations know data is exposed but lack clarity on which exposures create board-level risk. Traditional tools flood teams with regex-based noise and ignore attacker context. ADP eliminates this gap linking sensitive data exposures to exploit paths, identifying actionable prioritization and giving executives clear, business-level evidence.
Why it changes how you think about data risk
Focus on files that matter
Connect exposure to real business impact
Reduce manual triage
Prove resilience under real pressure
What security leaders can now prove
We have identified exploitable hidden credentials in files and data at risk, not just a laundry list of data exposures
NodeZero validates which exposures could lead to risks like IP Theft and Operational Disruption.
We have shown how identity attacks can escalate
NodeZero validates how hidden credentials can be used to escalate attacks and business risks, all with autonomous auto-tagging. No tuning required.
We have made DSPM operational
NodeZero validates which data-at-risk should be addressed first, prioritizing business impact above all else and making it easy to remediate the highest importance data security issues.
We help you tune your DLPs
NodeZero shows where credentials and data-at-risk can be exfiltrated, showing where DLPs can be fine-tuned to avoid critical business risks.
