Threat Actor Mapping
Reveal which adversaries match your exposures
Knowing you have a vulnerability isn’t enough. Security teams need to know who would exploit it — and what that risk means in the real world. Threat Actor Mapping connects NodeZero® pentest results to known adversary tactics, techniques, and procedures (TTPs), helping you prioritize remediation based on threat relevance, not just CVE counts.
Adversary-aligned context, not just vulnerabilities
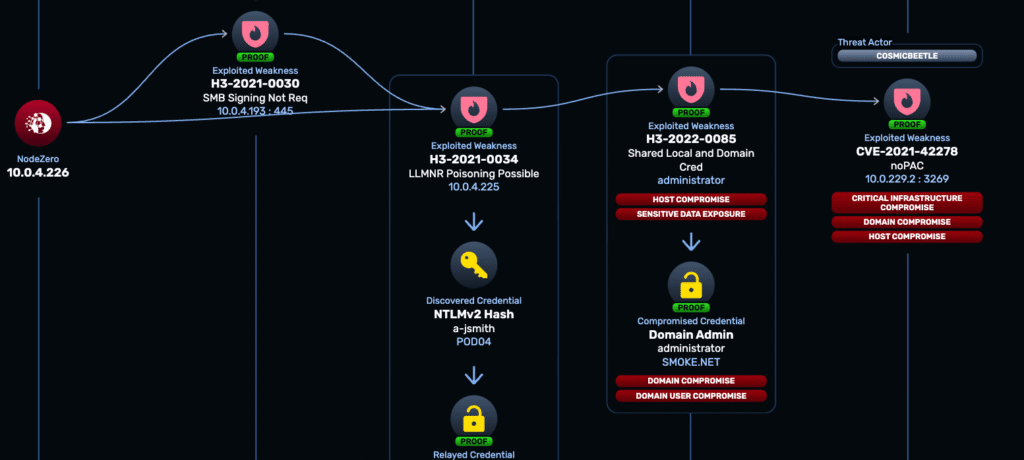
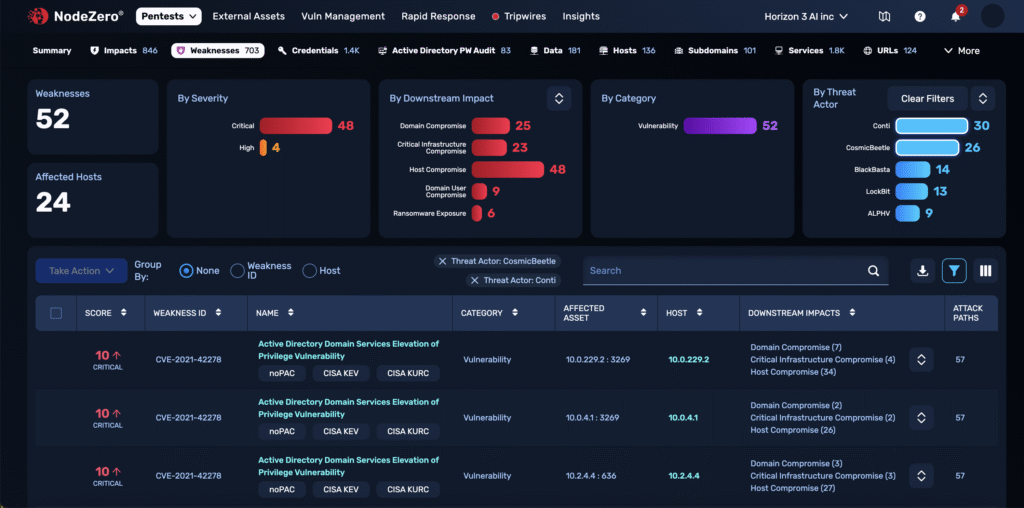
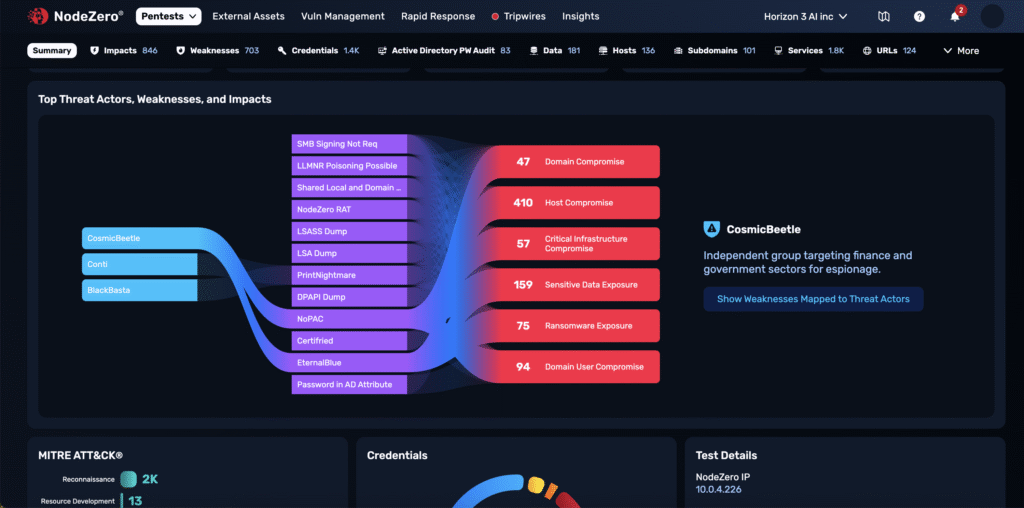
Threat Actor Mapping analyzes NodeZero’s findings and ties each attack technique to known threat groups based on MITRE ATT&CK. Instead of relying on passive threat feeds, it surfaces which adversaries share behavior with the techniques NodeZero actually used in your environment — providing operational context to help teams fix what matters most.
Note: This is not attribution. NodeZero maps observed TTPs to groups that commonly use them — giving defenders insight into adversary alignment, not point-in-time attribution.
How adversary mapping comes to life
Real techniques mapped to real threat groups
NodeZero runs real attacks, not simulations. As it moves through your environment, it logs every step — from lateral movement to privilege escalation to data access. Each technique is mapped to MITRE ATT&CK, then correlated with known threat actor profiles.
Business-ready context for decision makers
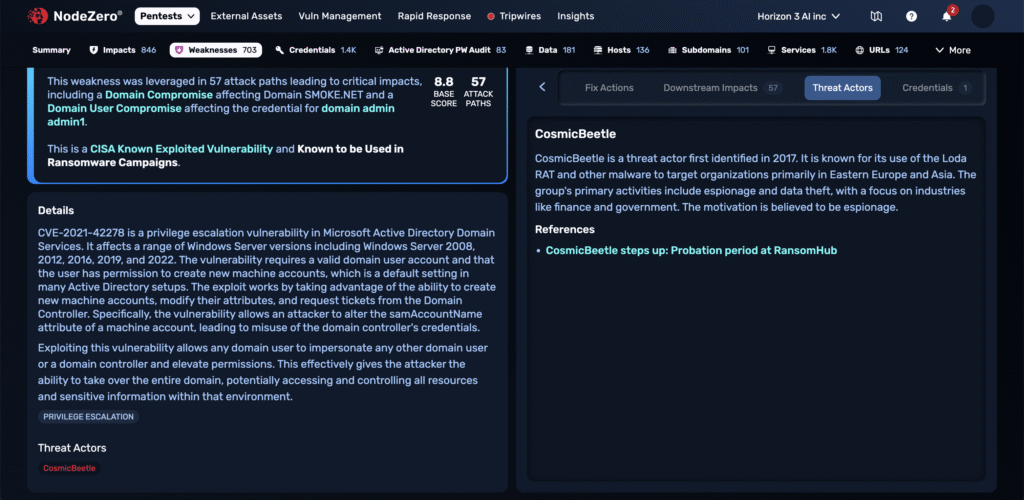
Each mapped actor includes a short and long description: who they target, what industries they operate in, and the urgency of mitigation. These narratives show up in exportable reports, making board-level reporting and regulator conversations easier and more credible.
Why threat-informed intelligence changes everything
Fix what your adversaries would exploit
Don’t guess which issues matter — prioritize based on real-world threat alignment.
Turn pentests into threat intelligence
Bridge the gap between vulnerability scanning and active threat monitoring.
Improve board and audit reporting
Explain risk in business terms, with known threat actors and mapped impact paths.
See the tactics behind the attacks
Every NodeZero operation now reveals which techniques match known adversaries — from APT29 to FIN7.