Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
CVE-2024-23108: Fortinet FortiSIEM 2nd Order Command Injection Deep-Dive
In November of 2023, preparing for a call for papers, I attempted to investigate the FortiSIEM patch for CVE-2023-34992. I kindly inquired with the PSIRT if I could have access to the most recent versions to some of their appliances to validate the patches, to which they declined. Acquiring access a different way, I eventually…
Enhancing Cybersecurity Through Collaborative Risk Management
May 21, 2024
Use Case About NodeZero™ for Third-Party Risk Management
On-Prem Misconfigurations Lead to Entra Tenant Compromise
As enterprises continue to transition on-premises infrastructure and information systems to the cloud, hybrid cloud systems have emerged as a vital solution, balancing the benefits of both environments to optimize performance, scalability, and ease of change on users and administrators. However, there can be risks involved when connecting a misconfigured or ill-protected network to cloud…
CVE-2023-34992: Fortinet FortiSIEM Command Injection Deep-Dive
In early 2023, given some early success in auditing Fortinet appliances, I continued the effort and landed upon the Fortinet FortiSIEM. Several issues were discovered during this audit that ultimately lead to unauthenticated remote code execution in the context of the root user. The vulnerabilities were assigned CVE-2023-34992 with a CVSS3.0 score of 10.0 given…
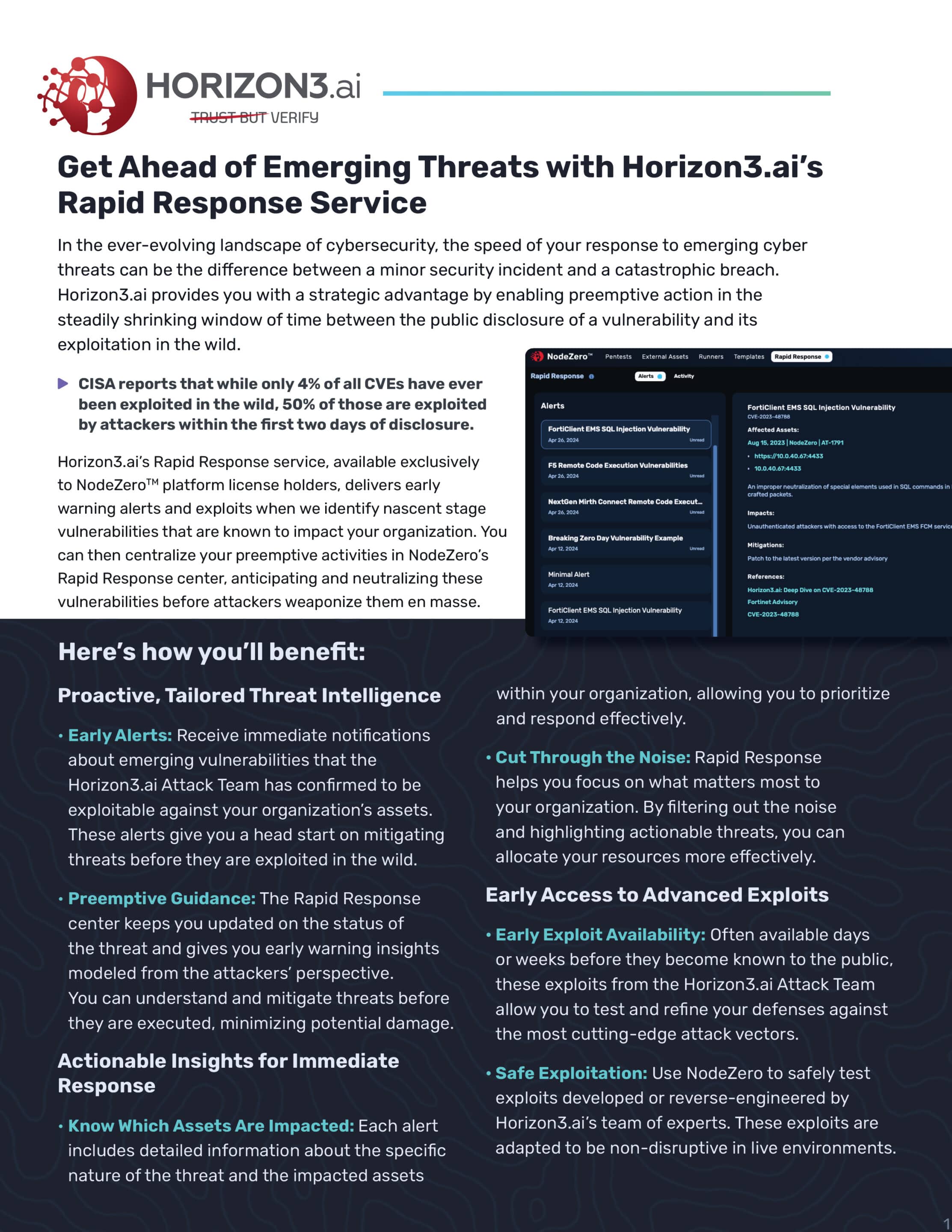
Outpace Emerging Cyber Threats with Horizon3.ai Rapid Response
In this webinar. Horizon3.ai cybersecurity expert Brad Hong covers our new Rapid Response service.
Advancing Emergency Response Security with Autonomous Pentesting
May 9, 2024
In an increasingly interconnected world, where digital technologies infiltrate every aspect of society, vulnerabilities in these systems can be exploited by malicious actors to disrupt emergency services, compromise sensitive information, or even endanger lives.
Get Ahead of Emerging Threats with Horizon3.ai’s Rapid Response Service
April 30, 2024
In the ever-evolving landscape of cybersecurity, the speed of your response to emerging cyber threats can be the difference between a minor security incident and a catastrophic breach. Horizon3.ai provides you with a strategic advantage by enabling preemptive action in the steadily shrinking window of time between the public disclosure of a vulnerability and its…
Fix What Matters: Accelerating Cyber Defense Through the Eyes of an Attacker
April 30, 2024
The emergence of new attack vectors, the steady growth of attack surfaces, and the increasing speed at which vulnerabilities are exploited underscore the critical need for proactive defense strategies.
NodeZero: Testing for Exploitability of Palo Alto Networks CVE-2024-3400
April 25, 2024
On April 12 (and then updated again on April 20), Palo Alto Networks released an advisory about a vulnerability in the PAN-OS® software that runs Palo Alto Networks® Next-Generation Firewalls (NGFWs).
Fortifying the Chain: A Proven Strategy for Supply Chain Defense
April 24, 2024
Understanding the Landscape of Cyber Threats and the Innovations in Third-Party Risk Management