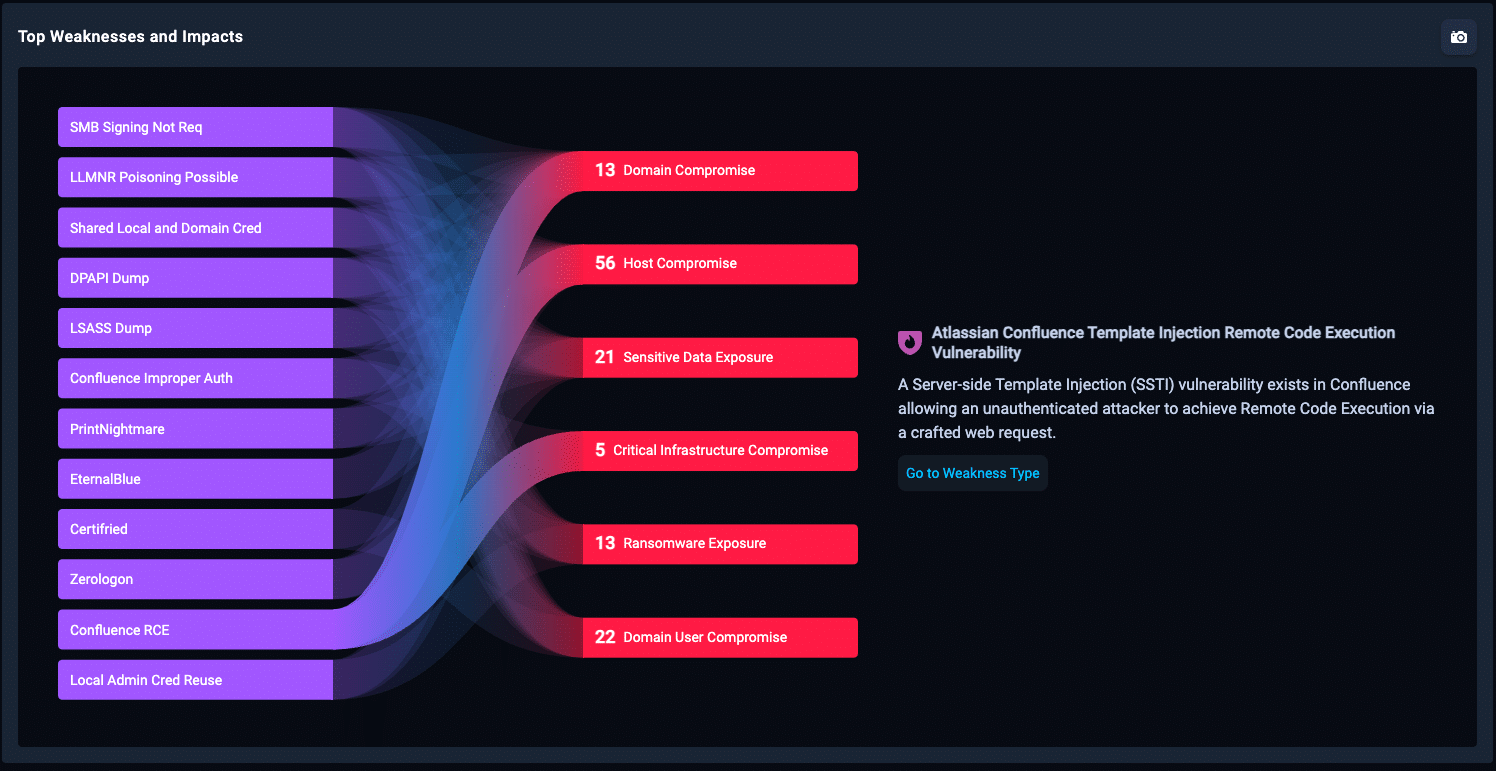
On 16 January, Atlassian released a security advisory concerning CVE-2023-22527 that affects vulnerable out-of-date versions of Confluence Data Center and Server. Both Confluence Data Center and Server are used by large enterprises and smaller to mid-size businesses respectively for team collaboration and knowledge sharing, and often house sensitive or proprietary information. This critical vulnerability (CVSS Score 10) allows an unauthenticated attacker to achieve remote code execution (RCE). This type of vulnerability is often scored as critical since RCEs can allow an attacker to control and manipulate computer systems from a distance. Although Atlassian just disclosed this vulnerability last week, security researchers are already observing exploitation attempts in the wild.
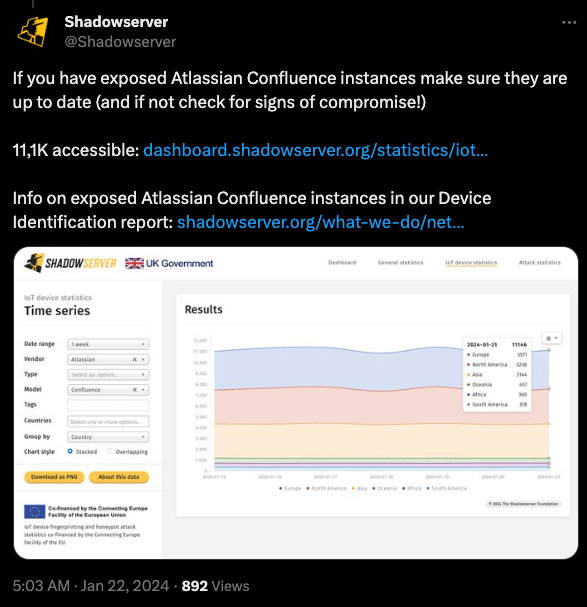
On 22 January, the non-profit cybersecurity organization The Shadowserver Foundation reportedly observed attempts at exploiting this vulnerability by cyber threat actors. Close to 40,000 exploitation attempts were observed from 600 IP addresses. The cyber threat actors used testing callback attempts and whoami execution in an attempt to look for vulnerable servers that they can compromise and abuse to gain undetected access to victims’ networks.
Who Is Affected?
Anyone who runs Confluence Data Center and Confluence Server endpoints versions 8.0.x, 8.1.x, 8.2.x, 8.3.x, 8.5.x, and 8.5.0 through 8.5.3 may be impacted by this vulnerability.
How Do I Fix It?
Atlassian recommends that you immediately patch if you are running an out-of-date version of Confluence Data Center and/or Confluence Server. At the time of this publication, there are no known workarounds to remediate this vulnerability.
How Can NodeZero™️ Help?
As of today, all users running NodeZero™ can run an autonomous pentest to determine if their Atlassian Confluence systems are vulnerable, reachable, and exploitable due to this vulnerability. We also recommend running a follow-on pentest to verify that any remediation steps, like patching in this instance, are effective.