A Pentest Wednesday® Story
Every security leader understands Patch Tuesday.
What most don’t realize is that attackers can chain weak credentials, misconfigurations, and defaults across an entire global environment in hours, long before patching cycles finish.
For one of the world’s largest payments providers, the challenge wasn’t applying fixes, it was proving they worked across the entire environment.
Outcomes at a Glance
Expanded testing from small samples to every IP, every quarter
Exposed default credentials and infrastructure blind spots missed by human pentesters
Replaced semi-annual point-in-time pentests with full-environment validation
Achieved auditor acceptance of autonomous pentesting for PCI and banking requirements
Consolidated tools while increasing visibility into security posture
Achieved measurable improvements in cyber hygiene, contributing to reduced insurance costs
That is the essence of Pentest Wednesday®. It moves beyond compliance-driven testing to organization-driven validation. For this payments provider, that shift changed how risk was understood, prioritized, and proven.
Impact
This organization operates one of the largest payment ecosystems in the world, processing trillions of dollars in annual transaction volume across more than a hundred countries. Its infrastructure spans hundreds of offices and environments, with security oversight shaped by strict banking and PCI requirements.
Each year, the company undergoes more than twenty PCI audits across dozens of products. Banks required at least two pentests annually, and the organization complied. On paper, the program looked mature. In practice, the limitations of that approach became increasingly clear. Attackers are not limited to the same narrow paths pentesters chose.
Groups targeting financial infrastructure prove that misconfigurations, defaults, and weak credentials, not just unpatched CVEs, were enough to cause real damage. Annual or semi-annual pentests were not built to keep up with the demands placed on the organization.
Background
Like many large enterprises, the company relied on a mix of defensive controls and human-led pentests to meet regulatory expectations. Each pentest produced a report, but every report told a different story.
- One or two findings per test
- Different attack paths each time
- No consistent coverage or scope
- No way to know what had never been tested
As one security leader from the organization quoted throughout this blog put it: “Pentesters hit the targets and walked away. They told me one or two issues, but never the full picture.”
At the core of the issue was scale, and the growing realization that traditional pentesting simply could not keep up with the size and complexity of the environment.
When NodeZero® was introduced, skepticism was high. The solution had to prove it could deliver real value, not just more data. Working sessions with Horizon3.ai’s Customer Success Team focused on walking through findings, validating fixes, and building confidence in the results.
That confidence came quickly.
“No human pentester can test 10,000 IPs. It is impossible.”
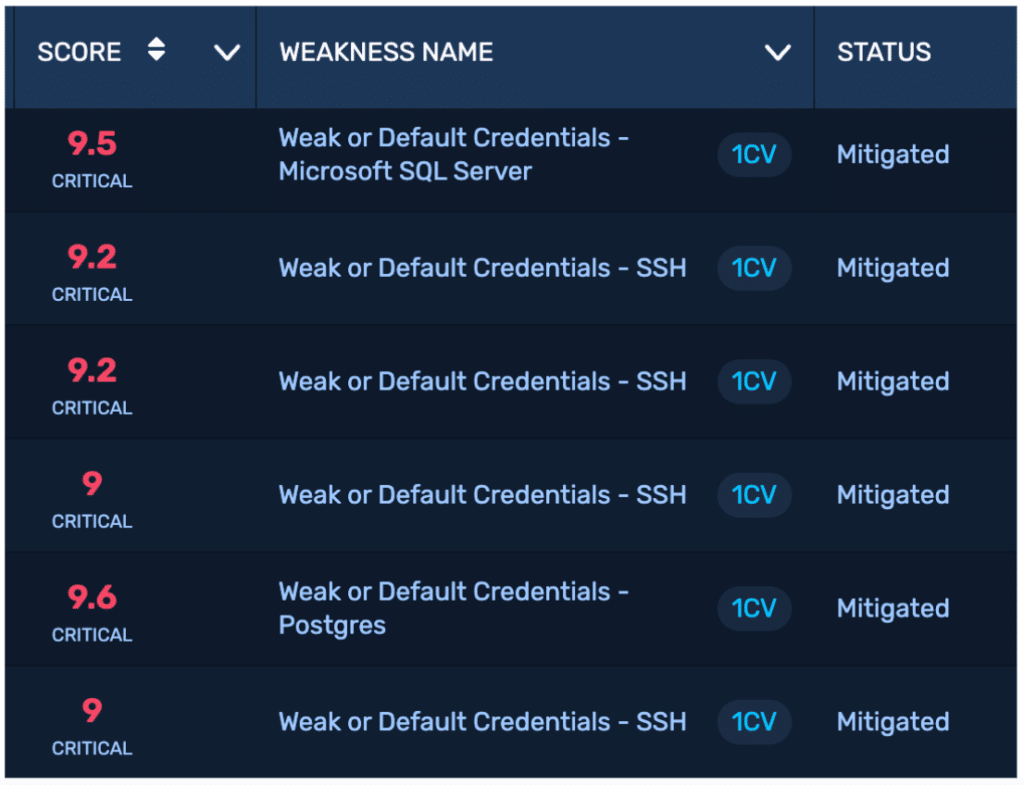
On the first NodeZero run, the team uncovered default passwords across infrastructure devices, exposed ESXi management ports, and misconfigured systems spread across offices globally. These were issues no prior pentest had previously reported.
“I was shocked. No human pentester ever found the default passwords or open ESXi ports NodeZero did on day one.”
Mitigation
The real shift happened when findings turned into proof. Using NodeZero’s exploitation evidence, the security team began demonstrating real attack paths to internal IT teams and product stakeholders. “They looked at me like I lost my mind. I said: You couldn’t fix your stuff, so I am fixing it for you.”
In one case, a single weak credential was leveraged to access nearly 300,000 files in approximately two hours, yet manual pentesters missed this entirely. That scenario would meet the objective of any ransomware operator.
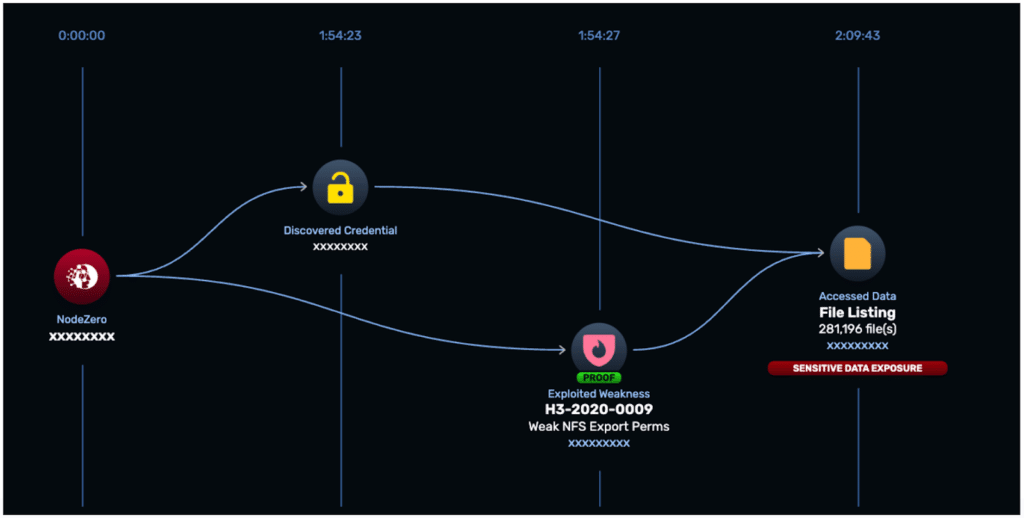
Seeing exploitation in action, instead of static vulnerability output, fundamentally changed how the team evaluated risk. Attack paths were no longer abstract, which removed ambiguity around severity and priority. Remediation timelines shortened, ownership became explicit, and fixes moved through the organization without friction.
With that level of clarity and confidence, the organization began to rethink how often and how broadly testing should occur.
Rather than relying on two point-in-time pentests each year, the organization adopted quarterly testing across its entire environment. Any initial concerns from banking partners were addressed with evidence, including consistent methodology, complete coverage, and proof that remediation efforts were effective.
Today, all four quarterly reports are shared with banking partners and auditors, and are accepted.
Remediation
With full coverage established, the team focused on turning testing into a repeatable, operational security program. As new NodeZero capabilities became available, including Vulnerability Risk Intelligence, they were adopted to strengthen different parts of the security lifecycle.
“Every quarter, we test every single IP. Humans cannot do that. NodeZero can.”
Scheduling NodeZero tests allowed the team to standardize quarterly testing across more than fifty networks, using prebuilt templates to accelerate reporting and make results easier for banks and auditors to consume.
Vulnerability and risk insights helped accelerate validation and confirmation, allowing the team to focus remediation on what attackers could actually exploit and then immediately prove fixes worked. The team made extensive use of NodeZero’s 1-Click Verify capability to confirm that critical weaknesses were fully mitigated.
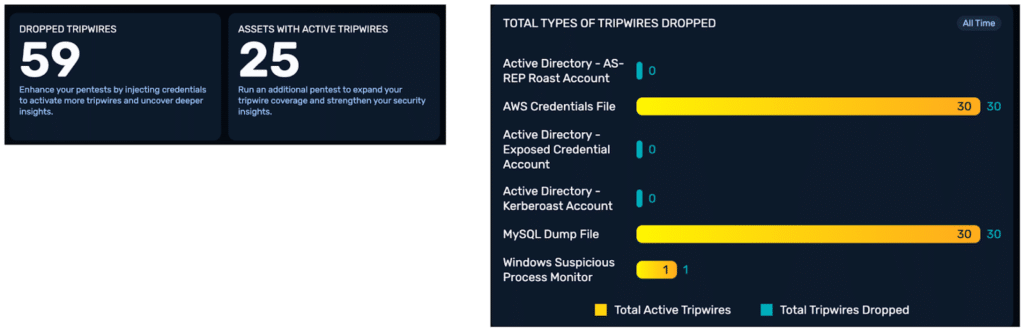
NodeZero Tripwires™ were fully adopted and replaced legacy deception tooling by embedding honeytokens directly into high-value systems. This reduced alert noise, improved detection fidelity, and eliminated the need for a separate deception platform.
“You can retire Canary now. Tripwires do this better.”
Operationally, NodeZero offset the lack of large internal red teams and specialized skill sets. It also helped demonstrate value to new security leadership with backgrounds at major financial institutions, where scale, auditability, and proof matter.
As cost scrutiny increased at the executive level, the security team was able to defend NodeZero as a core platform investment. It was positioned internally as a replacement for manual red team staffing, a consolidation of multiple tools, and a source of evidence-based validation rather than theoretical findings.
“NodeZero helped me justify cutting other tools. It does what they did, but better.”
Vendor-led manual pentesting was reduced to a single required annual engagement, supplemented by quarterly NodeZero testing across the entire environment. Previous deception and monitoring tools were also retired.
The business impact was tangible. Audit cycles accelerated, reliance on external services decreased, and insurer confidence improved as security posture became easier to demonstrate and defend. In one year alone, improved hygiene contributed to a $500K reduction in cyber insurance costs.
Looking ahead, the program continued to expand. Plans were set to extend testing into additional commercial and gateway networks, applying the same validation discipline beyond the original scope. The security leader also began influencing peers across the PCI ecosystem, including members of the PCI Security Council, to consider autonomous pentesting as a viable standard.
Conclusion
For this global payments provider, the lesson was clear. Patching remains necessary, but proof is what ultimately drives confidence, accountability, and resilience.
Point-in-time pentests were never going to scale to an environment of this size. Sampling small portions of the network left blind spots, and those gaps forced teams to rely on assumptions instead of evidence, increasing risk rather than reducing it.
By moving to continuous, full-environment validation, the organization replaced guessing with knowing, and compliance with resilience.
Patch Tuesday applies the fixes. Pentest Wednesday® proves the risk is closed.