In a typical enterprise network with thousands of systems and users, sophisticated attackers don’t waste time testing everything. They hunt strategically for the assets that deliver maximum impact: domain controllers, privileged service accounts, and critical database servers. Compromising these systems unlocks broad access and enables widespread impact. Depending on their objectives, adversaries can conduct espionage and steal intellectual property, deploy ransomware for financial extortion, execute business email compromise and wire fraud, sabotage critical operations, or establish persistent access for long-term strategic advantage. Whether the threat comes from nation-state actors, organized criminal groups, or insider threats, high-value targets remain the same.
What is High-Value Targeting?
High-Value Targeting (HVT) analyzes and prioritizes systems and accounts based on business impact, replicating how sophisticated attackers identify and prioritize targets after establishing initial access. It identifies domain controllers, privileged accounts, and critical infrastructure, directing NodeZero to test the most critical attack paths first. As NodeZero discovers new systems, credentials, and network relationships, HVT continuously refines its assessment and adapts priorities. This means faster discovery of critical paths and pentesting that reflects how real adversaries operate.
The Challenge: Too Many Targets, Not Enough Signal
Consider a mid-sized enterprise: 5,000 endpoints, 3,000 user accounts, and dozens of servers running critical services. Without intelligent prioritization, penetration testing becomes a numbers game where teams scan everything equally and leave prioritization to already‑overwhelmed security staff. With 48,185 new vulnerabilities disclosed in 2025, a 20% increase over roughly 40,000 in 2024, and many SOC teams reporting they cannot keep pace with alerts, defenders struggle to separate signal from noise.
Sophisticated attackers don’t have this problem. Human-operated ransomware groups and advanced persistent threat (APT) actors spend time on reconnaissance to avoid inefficiency. According to Mandiant’s M-Trends 2024 report, attackers maintain presence in networks for a median of 10 days before detection, time they use to map targets and build attack paths. They enumerate domain users looking for administrator patterns, scan for hostnames suggesting critical infrastructure like DC, SQL or BACKUP, and correlate Active Directory metadata with network service data to build targeted attack paths.
Industry data underscores that focus. Microsoft’s reporting shows that 78% of human-operated ransomware attacks involve domain controller breaches, and in 35% of cases the domain controller becomes the primary device used to spread ransomware at scale. Attackers target authentication systems, backup infrastructure, and privileged accounts because compromising these assets enables widespread impact. High-Value Targeting gives defenders that same contextual intelligence by providing NodeZero with attack prioritization context and surfacing business impacts directly in the UI, helping teams understand the true risk each asset represents.
How High-Value Targeting Works
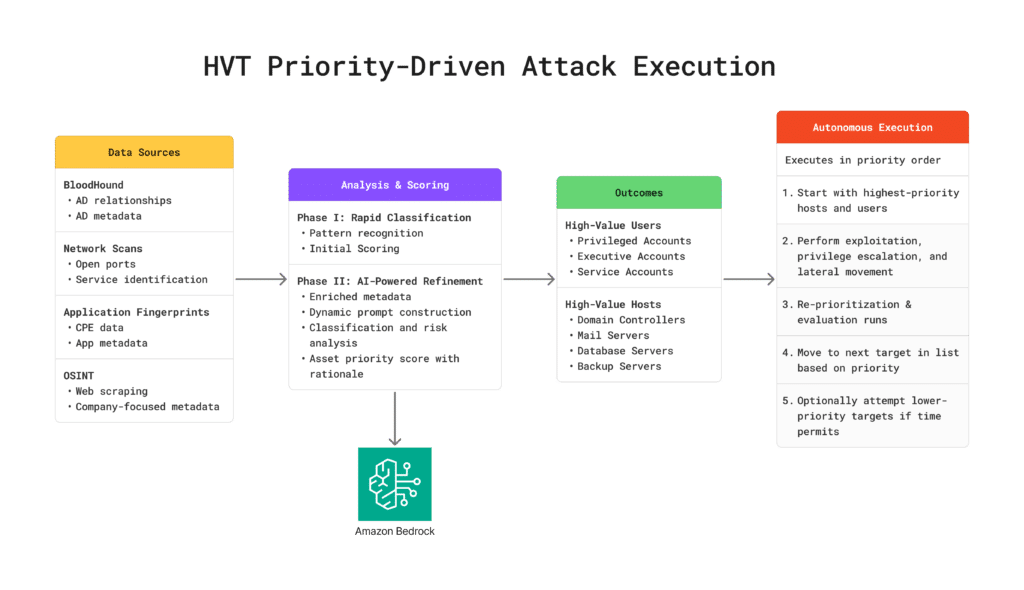
High-Value Targeting uses a two-phase approach to identify and score targets based on their potential impact on your organization.
Rapid Classification – Performs initial analysis using pattern recognition to quickly categorize assets based on naming conventions, network characteristics, and structural indicators. This baseline identifies likely roles such as domain controllers, database servers, and administrative accounts with high efficiency.
AI-Powered Refinement – Large language models process the baseline classification alongside detailed data to produce nuanced, accurate prioritization. The analysis synthesizes hostname patterns, network scan data (port scans, IANA service names, application fingerprints, CPE data), identity metadata (group memberships, SPNs, object location), privilege indicators, and business context. This includes environment tags, geographic hints, department associations, asset criticality, and OSINT about the organization and its operations.
This two-phase architecture reduces cost by filtering targets with fast pattern matching before invoking AWS Bedrock LLMs for deeper analysis. HVT runs directly within the NodeZero platform with full explainability, allowing teams to see why each asset or identity was tagged as high value and how that classification ties to business risk.
The diagram below illustrates this workflow: reconnaissance data feeds into LLM-powered analysis and scoring, producing priority rankings and attack rationales that drive NodeZero’s autonomous execution strategy.
Host Analysis in Practice
HVT examines each host using multiple signals:
- Naming patterns that indicate purpose and role, such as
prod-db-mysql01,backup-veeam-west,dc01-chicago,sqlserver-finance,exchange-mail01,jump-box-dmz, or identifiers likedc,ad,sql,mssql,exch,mail,backup,admin,mgmt,jump,bastion,web,api,file, ornas - Network services detected during scanning, including Kerberos (88), LDAP (389/636), SMB (445), RDP (3389), SQL Server (1433), Exchange-related ports, backup agents, and application-specific service banners
- Directory metadata from Active Directory or cloud identity providers, such as computer object location in OUs, service principal names, security group memberships, and object attributes
- Business context including environment tags (production vs. development), geographic location, and department assignments, enriched with company industry data from OSINT to understand asset criticality
While domain controllers represent critical infrastructure in any environment, our prioritization analyzer goes beyond identifying standard Active Directory components. The intelligence extends across diverse industries and environments: industrial control systems, educational institutions, maritime operations, financial services, and medical facilities.
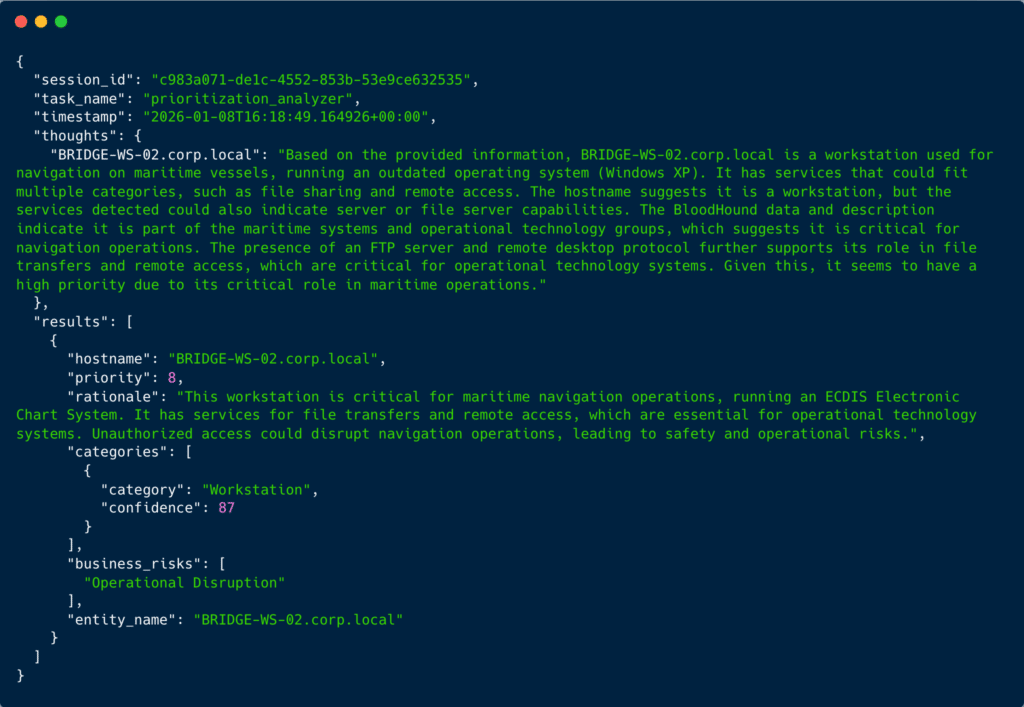
Here’s how the analyzer triangulates evidence from multiple sources to build confidence. In this example above, four independent indicators all point to the same conclusion:
- Hostname semantics:
BRIDGE-WS-02.corp.localindicates a workstation on the ship’s bridge - BloodHound enrichment: Group memberships in
Maritime SystemsandOperational Technologyconfirm its operational role - Application detection: Identifies ECDIS (Electronic Chart Display and Information System), the navigation software used on maritime vessels
- OSINT enrichment: The business website indicates this is a maritime transportation shipping company to help with context
Despite being technically classified as a workstation (87% confidence), the analyzer assigns priority 8, higher than many servers, because it understands the business context: this system is critical for maritime navigation operations. The presence of an outdated operating system (Windows XP), combined with FTP and remote desktop services on an OT network, creates significant exposure.
This multi-faceted approach reduces false positives and provides security teams with trusted, actionable intelligence. A traditional vulnerability scanner might flag this as “just another Windows XP workstation,” but HVT recognizes it as a safety-critical system where compromise could disrupt navigation operations and create maritime safety risks.
Here’s another interesting example that demonstrates HVT’s breadth across different security domains:
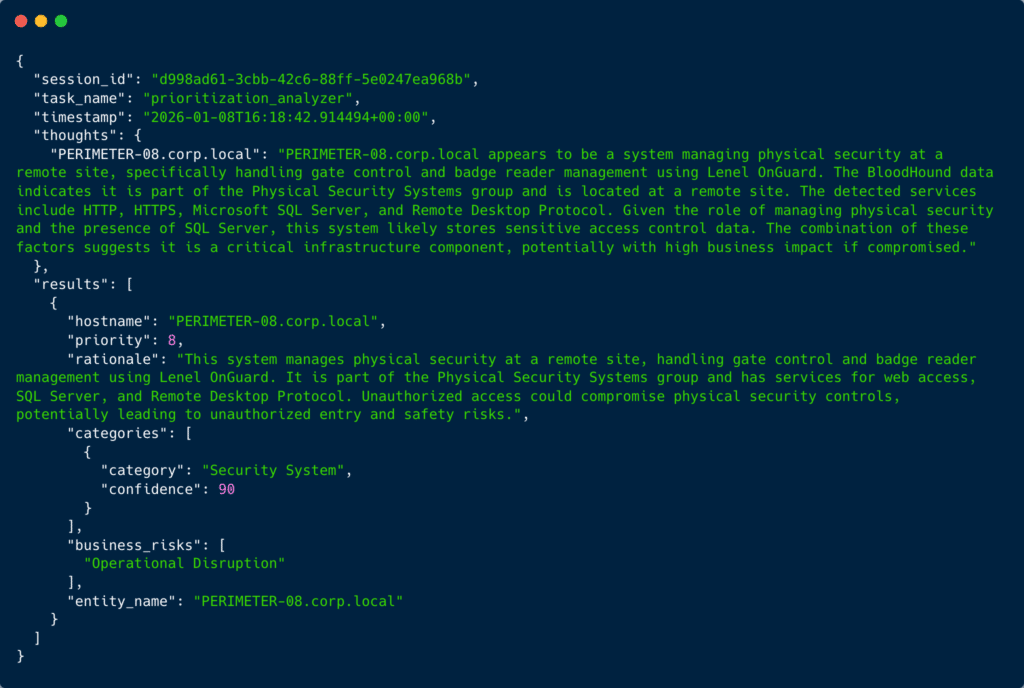
The analyzer identifies PERIMETER-08.corp.local as a physical security system running Lenel OnGuard, software used for gate control and badge reader management. Here’s how multiple data sources confirm this classification:
- Hostname semantics:
PERIMETER-08.corp.localsuggests perimeter security infrastructure - BloodHound enrichment: Group membership in
Physical Security Systemsand location tagged as a remote site - Application detection: Identifies Lenel OnGuard access control software
- Network services: Microsoft SQL Server detected, which stores sensitive access control data and badge reader logs
The analyzer assigns priority 8, recognizing that physical security systems represent a critical convergence point between cyber and physical domains. While technically just a server running a database and web interface, compromise of this system could allow attackers to manipulate gate controls, disable badge readers, or gain insights into facility access patterns at a remote site.
User Analysis in Practice
HVT evaluates each user account based on:
- Account naming that suggests role or privilege level, such as admin prefixes (
adm-,admin-), service account patterns (svc-,sa-), or executive indicators - Privilege indicators including domain group memberships (Domain Admins, Enterprise Admins, Schema Admins), admin count attributes, delegated permissions, and elevated role assignments
- Business function inferred from job titles, department affiliations, and organizational context
- Account status including whether accounts are active, disabled, stale, or have special restrictions
- OSINT intelligence from public sources: company industry and business model, employee roles and departments, organizational structure, and key business functions
This contextual understanding allows HVT to distinguish between a domain administrator with Enterprise Admin rights (existential risk), a DBA service account with database access (high-value data exposure), and a standard user in sales (limited blast radius). The system understands that compromising the CFO’s account at a financial services firm carries different implications than a marketing coordinator at a manufacturing company.
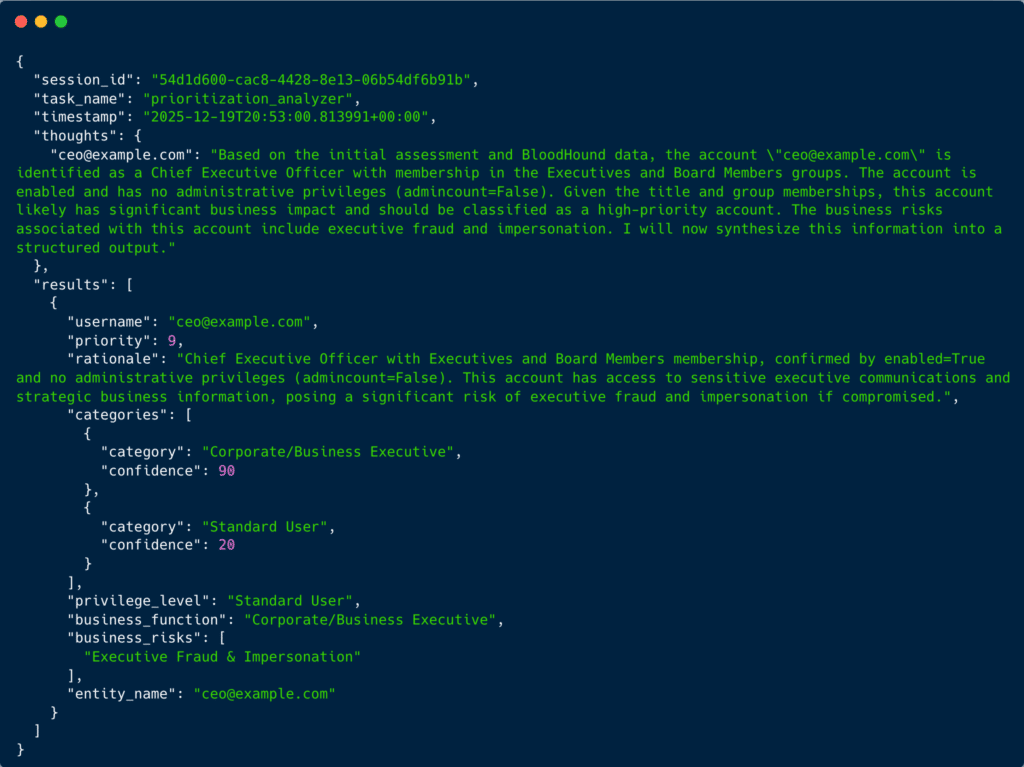
Take this CEO account in the image above: despite having admincount=False and zero administrative privileges, it receives a priority score of 9, nearly as critical as the domain admin. The analyzer synthesizes multiple contextual signals:
- Identity inference: UPN format and title field confirm C-suite position
- Group memberships:
ExecutivesandBoard Membersgroups indicate organizational importance - Account status:
enabled=Trueconfirms it’s an active, accessible target - Attack vectors: Flags specific business risks like
Executive Fraud & Impersonation
From an attacker’s perspective, a CEO’s inbox can be more valuable than a sysadmin’s terminal. Business Email Compromise (BEC), wire fraud, and strategic intelligence gathering don’t require elevated privileges. They require access to the right person.
The dual-category classification shows this nuance: 90% confidence as Corporate/Business Executive (the primary risk driver) with 20% confidence as Standard User (the technical reality). This helps security teams understand that protecting this account requires different controls than protecting privileged accounts: anti-phishing measures, email authentication (DMARC/DKIM/SPF), and executive security awareness rather than PAM solutions.
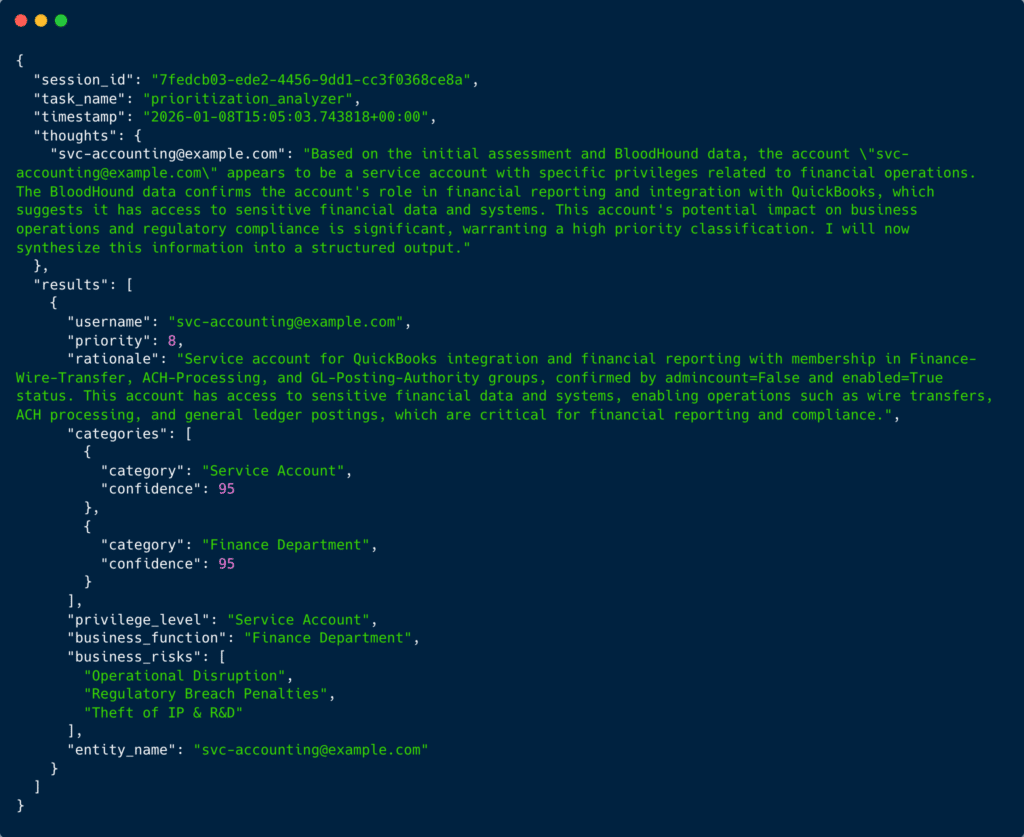
Service accounts often reveal the most about an organization’s critical business operations. Consider svc-accounting@example.com, a service account that HVT identifies as high-priority despite having zero administrative privileges:
- Account naming: The
svc-prefix andaccountingdesignation immediately suggest a service account tied to financial operations - BloodHound enrichment: Group memberships in
Finance-Wire-Transfer,ACH-Processing, andGL-Posting-Authorityconfirm access to critical financial systems - Application context: Integration with QuickBooks for financial reporting and data synchronization
- Account status: Enabled and active (
admincount=Falsebutenabled=True)
The analyzer assigns priority 8 and flags three distinct business risks: Operational Disruption, Regulatory Breach Penalties, and Theft of IP & R&D. This service account can execute wire transfers, process ACH payments, and post to the general ledger. From an attacker’s perspective, this account represents direct access to move money and manipulate financial records, making it far more valuable than many privileged IT accounts.
Business Risk Mapping
HVT automatically maps targets to 13 tangible business risk categories, including:
- Operational Disruption: Systems whose compromise would halt business operations
- Critical System Shutdown: Infrastructure whose failure affects organization-wide services
- Regulatory Breach Penalties: Systems containing regulated data (PCI, HIPAA, GDPR)
- Leak of Sensitive Communications: Executive accounts or strategic planning systems
- Theft of IP & R&D: Engineering systems, source code repositories, research data
This mapping helps security teams articulate risk to business stakeholders in business terms rather than just CVSS scores.
The Attack Path
NodeZero uses High-Value Targeting methods to prioritize attack operations dynamically. When NodeZero gains initial access, it continuously re-prioritizes based on newly discovered systems, credentials, and relationships. It probes high-priority user accounts for weak credentials or authentication vulnerabilities, tests administrative workstations for exploitation vectors or credential exposure, and leverages compromised credentials against domain controllers and database servers. As new data emerges, HVT reassesses priorities to focus on the most critical paths.
NodeZero offers two operational modes: HVT-Only, which exclusively targets assets tagged as high value, and Comprehensive, which attacks all compromised entities but prioritizes high-value paths first. In both modes, HVT paths are exhausted before moving to lower-priority targets, creating efficient attack chains that mirror how advanced persistent threats operate.
The attack graph below demonstrates this in action, showing how NodeZero discovered HVT-prioritized hosts that led to compromising HVT-identified accounts with privileged access.
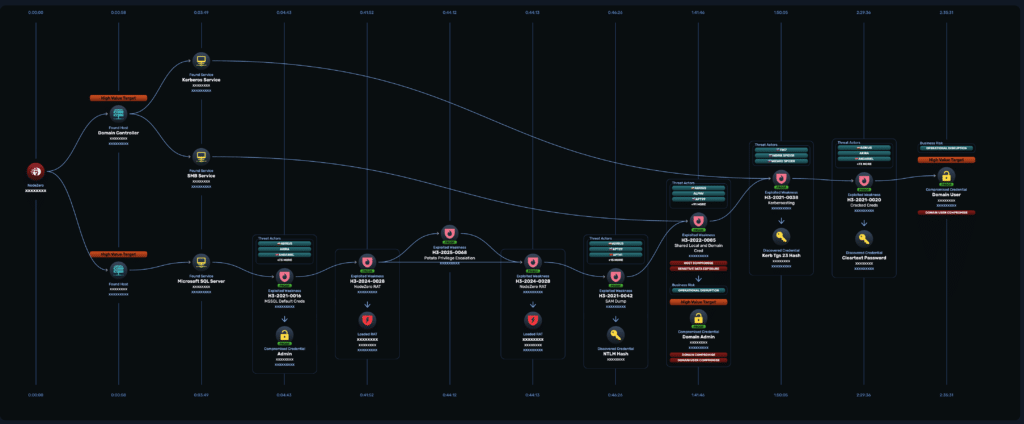
Within the first three minutes, NodeZero identifies the Domain Controller and Microsoft SQL Server after the initial scan. The critical infrastructure targets are marked with orange HIGH VALUE TARGET bars and two parallel attack chains then unfold:
Path 1: Kerberoasting attack
- Leverages Domain Controller to identify Kerberoastable service accounts
- Executes Kerberoasting attacks to extract SPN tickets
- Cracks tickets offline to obtain plaintext credentials
- Compromises High-Value domain user
svc_Solarwinds
Path 2: SQL Server exploitation chain
- Identifies MSSQL server with default credentials
- Deploys NodeZero RAT with limited permissions
- Chains multiple exploits and performs privilege escalation
- Dumps credentials from MSSQL server memory
- Discovers Domain Admin credentials
Under the Hood: AWS Bedrock
High-Value Targeting analyzes sensitive reconnaissance data from customer networks, which means security and data isolation are non-negotiable. AWS Bedrock provides:
- Data isolation guarantees: Customer prompts and outputs are never stored by Bedrock, never shared with third-party model providers (Anthropic, Meta, Cohere), and are never used by these providers for model training. Bedrock uses dedicated model deployment accounts isolated from providers, ensuring model providers have no access to customer data or logs.
- Scoped IAM permissions: Granular access controls using AWS IAM allow us to restrict HVT to specific Bedrock actions (like
bedrock:InvokeModel) with least-privilege permissions. We use IAM roles with tightly scoped policies, ensuring HVT can only invoke the specific models and operations required for analysis. - Model flexibility: Access to multiple foundation models from different providers through a single API. When newer, more capable models emerge (like Claude Opus 4 or future releases), we can evaluate and adopt them without rebuilding infrastructure, keeping HVT’s intelligence current.
- Cost optimization: Prompt caching reduces costs by up to 90% and latency by up to 85% for our repeated analysis prompts. Combined with our two-phase architecture (fast pattern matching before LLM invocation), we minimize expensive API calls while maintaining analysis quality.
- Production scalability: Bedrock handles automatic scaling, availability, and model management.
Bedrock delivers production-grade reliability backed by AWS infrastructure while avoiding single-provider lock-in. Multi-model access through a unified API means we can evaluate and adopt newer models as they emerge, keeping HVT’s intelligence current regardless of which providers succeed long-term.
Conclusion
High-Value Targeting demonstrates what’s possible when you combine LLM intelligence with autonomous pentesting. HVT doesn’t just find vulnerabilities; it understands which ones matter and why, adapting in real-time as NodeZero discovers your environment.
This is just the beginning. We’re continuously evolving our prioritization analyzer to understand more attack scenarios and business contexts. We’re also developing additional LLM-powered capabilities that will push autonomous pentesting even further. Stay tuned.
Want to see your network through an attacker’s eyes? The game has changed.
Sources & References
- Mandiant M-Trends 2024 Report – Global median dwell time (10 days overall, 5 days for ransomware)
Source: https://services.google.com/fh/files/misc/m-trends-2024.pdf - Microsoft Security Blog (April 2025) – Human-operated ransomware targeting domain controllers (78% breach rate, 35% as primary spreader)
Source: https://www.microsoft.com/en-us/security/blog/2025/04/09/how-cyberattackers-exploit-domain-controllers-using-ransomware/ - Vectra AI State of Threat Detection Report – SOC team challenges with alert volumes
Source: https://www.helpnetsecurity.com/2024/10/07/soc-teams-security-tools-problems/ - Enterprise Strategy Group (ESG) / ISSA Study – Cybersecurity professional work-life balance challenges (38%)
Source: https://brightsec.com/blog/the-growing-concern-of-burnout-in-application-security/ - Cisco Talos Year in Review 2024 – Identity-based attack patterns and Active Directory compromise
Source: https://cyberscoop.com/cybercriminals-target-identity-weaknesses-cisco-talos/ - Semperis 2024 Ransomware Risk Report – Active Directory as primary ransomware target
Source: https://www.semperis.com/blog/new-ransomware-statistics-reveal-need-for-ad-security/ - SpectreOps – BloodHound is developed and maintained by SpecterOps. Learn more at https://specterops.io/bloodhound
- Jerry Gamblin – 2025 CVE Data Review (48,185 CVEs disclosed in 2025; 20.6% increase over 2024) Source: https://jerrygamblin.com/2026/01/01/2025-cve-data-review/
