Being a #learnitall, Lesson 1: Be Open to Be Wow’d
Most of the startup advice out there is pretty clear: get feedback early and often. Customer input is invaluable to delivering iter0, your MVP, feature releases that matter, bug fixes, utility and simplicity.
In Customer Success, a lot of the job is review and advise so a customer can hit their definition of awesome. Inevitably, if we see a customer who isn’t using the product right, we advise them how to get the most bang for their buck.
Sometimes, they advise us back.
So, our story begins…we’ve created a product that helps organizations large and small in their cybersecurity journey. Key to that product is proof. Having suffered them for the last 25 years, we’re passionate in our loathing for tools that waste time, talent, and treasure, so we provide proof of reachability and exploitability. The result is a drastic increase in accuracy and reduction in false positives, both of which resonate with leaders and practitioners who don’t value being shown “more”.
One of our customers is a global manufacturing company that has taken charge of their security posture over the last year. Sometimes however, because they’ve been using traditional tools in traditional ways, they use our product in like ways. That’s when I pounce.
In one recent case, I was schooled how a customer is using our product to do something they couldn’t do before, and that has made all the difference in the world.
“The hardest part of cyber security is deciding what not to do” …and this company put that statement into action.
While many of the tools out there associate value by showing all the issues you haven’t addressed—the more the better—this company doesn’t see it that way. As a matter of fact, they don’t even find those results that interesting or important.
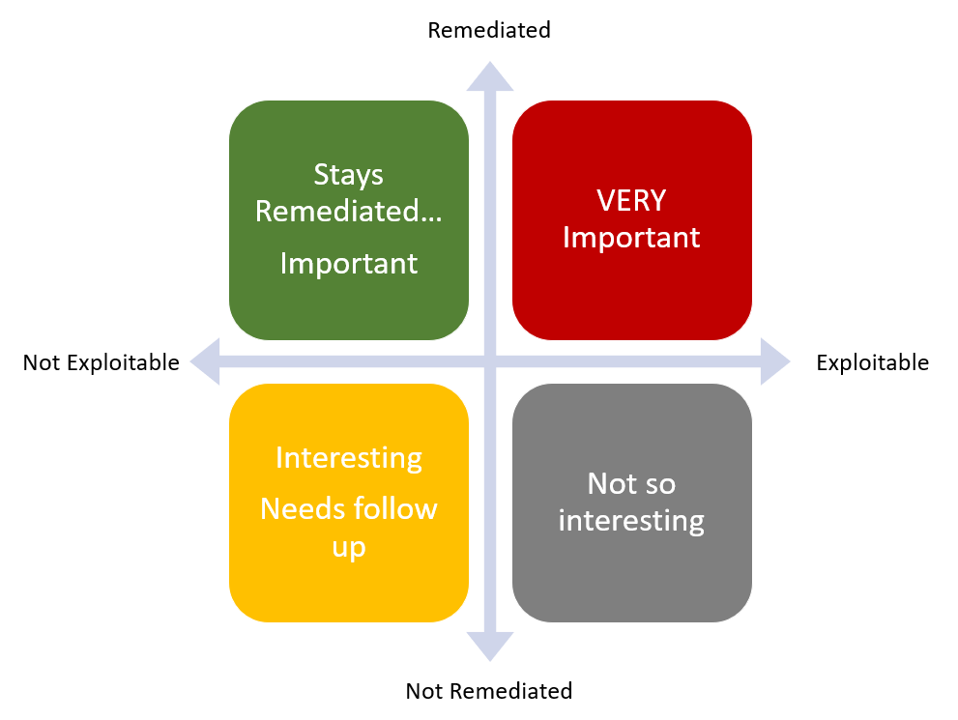
Specifically, they are running risk verification operations – where they rescan previously identified exploitable hosts, to see:
- If we didn’t remediate them, are they still exploitable (not so interesting)
- If we didn’t remediate them, but they show up as fixed (more interesting, needs follow up)
- If we DID remediate them, did they stay remediated (important)
- If we THINK we remediated them, but they show up as still exploitable (very important)
They do this targeted on the specific previously identified hosts to get accurate results quickly. The outcomes this has opened has been far and wide: verifying policy implementation, verifying remediation effectiveness, verifying contractor SLAs, verifying endpoint detection tuning, and verifying their logging and alerts. The results have been astounding.
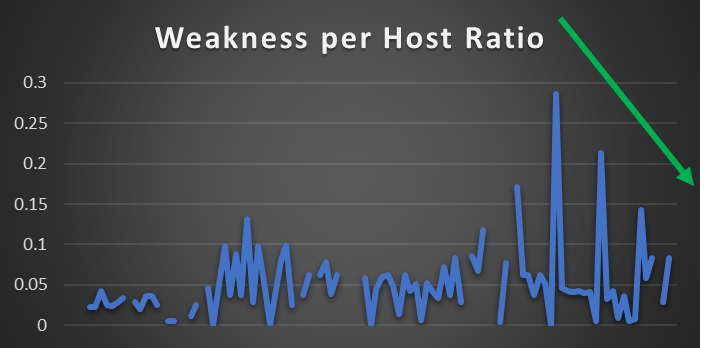
In only six months, their weakness-per-host ratio has decreased by 55% with ZERO additional manpower. Their 4-person blue team is operating as if they are a 20-person purple team.
They’ve created a culture that viscerally sees the impacts of their actions and now holds one another accountable by lifting one another up. They aren’t trying to tell their leadership they are impenetrable but are sending a clear signal: We are ready.
In conclusion, learned a great lesson here: be open to be wow’d. This customer is owning and telling their story in a powerful way, and all we had to so was listen and learn.
This is what cybersecurity can be. We might not always get it right, but we get better, together.

