Over the last week, the widely reported critical security flaw in the Progress MOVEit Transfer application (CVE-2023-34362) reminded us yet again to remain vigilant in securing our IT infrastructure from potential cyber threat actors. Also, part of the #StopRansomeware campaign, Cybersecurity & Infrastructure Security Agency (CISA) published a joint Cybersecurity Advisory (CSA) detailing the importance of organizations protecting against ransomware while maintaining a pulse on the current threat landscape. According to Progress, MOVEit Transfer is used worldwide by thousands of customers, including major companies like Disney, Chase, and BlueCross Blue Shield, for managing organizations’ file transfer operations. The CL0P ransomware gang, otherwise known as Lace Tempest, is credited with initially exploiting the zero-day vulnerability and publishing an extortion note on its dark web leak site claiming to have information on hundreds of businesses.
CVE-2023-34362 poses a significant risk to businesses relying on MOVEit for file transfer operations. The active exploitation of this vulnerability by threat actors emphasizes the need for swift action. This post is intended to help you increase your understanding of the potential impacts and add recommendations about security measures you can take to fortify their defenses and mitigate the risk posed by CVE-2023-34362.
An attack targeting MOVEit’s web application could prove detrimental to any organization, because the application is responsible for interfacing with MySQL, Microsoft SQL Server, and Azure SQL database engines. This critical flaw is an SQL injection vulnerability that lets unauthenticated attackers gain access to unpatched MOVEit servers and execute arbitrary code remotely, giving them access to sensitive data, the ability to disrupt systems, or complete compromise of the file transfer infrastructure. With reports of active exploitation in the wild, it is crucial to comprehend the implications of CVE-2023-34362 on businesses relying on MOVEit.
Open-source reporting indicates that cyber threat actors are actively exploiting or seeking to exploit CVE-2023-34362 in real-world scenarios, highlighting the urgency of addressing this vulnerability. CL0P, the initial group to exploit this vulnerability, is notorious for being a “big game hunter” that targets organizations with large budgets by issuing proportionally large ransom demands – some demands have gone as high as $20 million. However, CL0P also hones and sharpens their skills by targeting smaller organizations. Additionally, they have been known to target the Public Health and Healthcare industry in the past. Some examples include:
- April 2020: ExecuPharm, Inc., a U.S.-based pharmaceutical research company
- May 2020: Carestream Dental LLC, a U.S.-based provider of dental equipment
- November 2020: Nova Biomedical, a U.S.-based medical device manufacturer
While we do not have insight into how much money CL0P is demanding, they have provided the public with step-by-step instructions for would-be victims (see Graphic #1 below). As of 14 June, CL0P appears to have followed through with at least a portion of the instructions when they published the names of a handful of companies that presumably refused to contact them.
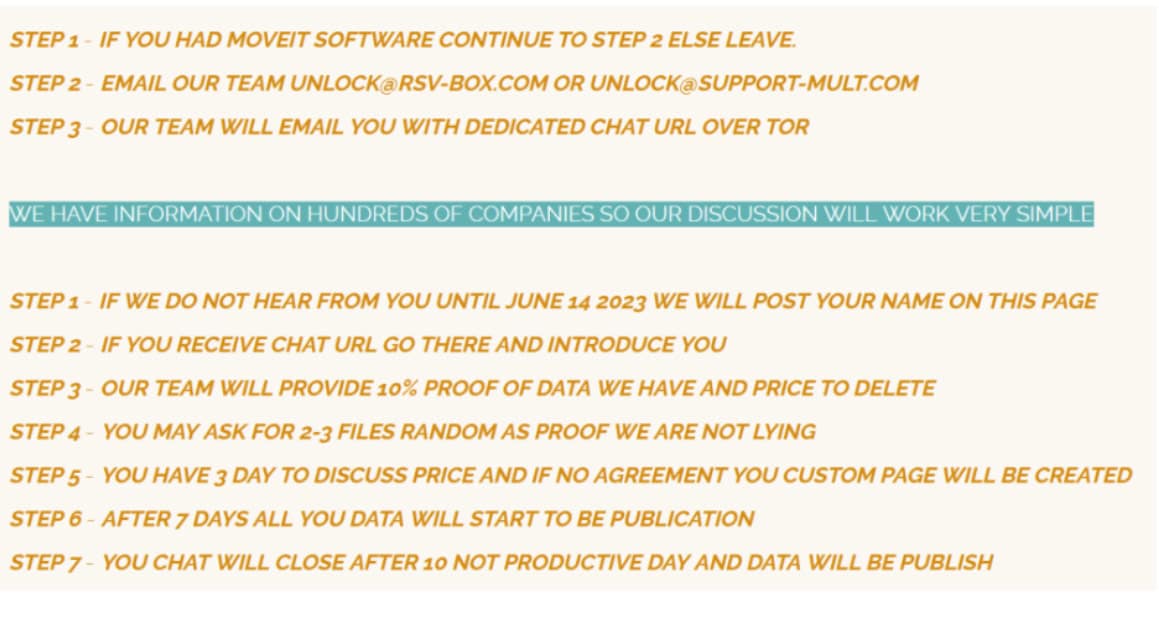
Graphic #1: CL0P Ransomware Gang leaves an extortion note for MOVEit Transfer application users.
Background
CL0P has been in the ransomware game since 2019-2020 and is known for targeting managed file transfer (MFT) applications touting ransomware as a service (RaaS) to infiltrate their targets IT infrastructure. Mostly targeting MFT applications, they continue to use these holes in vulnerable software for monetary gain. In the recent past, CL0P has also been attributed to several other recent zero-day ransomware campaigns such as PaperCut, GoAnywhere MFT, SolarWinds Serv-U, and Accellion FTA. For example, in mid-March CL0P exploited the GoAnywhere MFT vulnerability (CVE-2023-0669) to gain access and steal data; and has reportedly targeted over 130 organizations worldwide. Using similar tactics, techniques, and procedures (TTPs), their main goals are disrupting daily organizational cyber activity, stealing sensitive data, and finding other opportunistic ways to disrupt or deploy further attacks.
What Now?
Horizon3.ai proactively warns customers about potential zero-day and N-day ransomware attacks and impacts so that they take immediate action to fix potential vulnerabilities and mitigate possible threats. Exploitation by any cyber threat actor poses a significant risk to businesses relying on the MOVEit web application for file transfer operations. Key Impacts on Businesses include:
- Data Breaches and Intellectual Property Theft (including current and former employee data)
- Operational Disruption and Downtime
- Manipulation of File Transfers
- Reputational Damage and Legal Consequences
Mitigation and Recommendations:
- Implement Regular Pentest Cadence (NodeZero)
- Apply Security Patches and Updates (Progress Security Advisory)
- Implement Intrusion Detection and Prevention Systems
- Conduct Regular Security Audits
- User Awareness and Training
In conclusion, the CVE-2023-34362 vulnerability in MOVEit’s web application poses significant risks to businesses relying on the software for file transfer operations. Exploitation of this vulnerability can result in data breaches, intellectual property theft, operational disruptions, manipulated file transfers, reputational damage, and legal consequences. To mitigate these risks, organizations should promptly apply security patches, implement regular pentest cadence, implement intrusion detection and prevention systems, conduct regular security audits, and provide user awareness and training. By taking these proactive measures, businesses can enhance their security posture and minimize the potential impacts of CVE-2023-34362 and thwart possible attacks by groups such as CL0P. It is crucial for organizations to prioritize cybersecurity and remain vigilant in addressing vulnerabilities to protect their sensitive data and maintain the trust of stakeholders.
Please see our Horizon3 Attack Team’s blog MOVEit Transfer CVE-2023-34362 Deep Dive and Indicators of Compromise for extensive technical information!
Sources:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-158a
https://www.darkreading.com/application-security/mass-exploitation-0-day-bug-imoveit-file-transfer-underway
https://www.darkreading.com/attacks-breaches/cl0p-gang-exploit-moveit-flaw-2-years
https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
https://www.horizon3.ai/nodezero/
https://www.horizon3.ai/moveit-transfer-cve-2023-34362-deep-dive-and-indicators-of-compromise/
https://securityaffairs.com/147195/cyber-crime/clop-ransomware-moveit-transfer-attacks.html


