A Pentest Wednesday® Story
Security programs rarely fail because teams ignore risk. They fail because risk is measured on a calendar, while environments change every day.
For one organization operating inside the financial and insurance industry, security had long been a priority. Infrastructure decisions were made with security in mind before a formal security program even existed. But growth changed the equation.
Headcount expanded rapidly. Operations spread across multiple locations. Business process outsourcing became core to daily work. Cloud usage increased. Legacy on-prem systems remained. Acquisitions expanded the attack surface faster than security controls could be applied.
While security efforts were active and ongoing, efficacy was still judged using a once-a-year snapshot.
As the organization’s Security Engineer put it:
“We went from a once yearly, compliance mandated, third party contracted pentest… They’d give us the findings. We’d get 30 to 60 days to remediate, and then we’d get another retest and report, and that was it.”
Everything else happened in between.
That gap eventually became hard to ignore.
Outcomes at a Glance
- Transitioned from yearly compliance snapshots to weekly validation of real-world exposure
- Reduced mean time to remediate from months to days
- Established repeatable remediation workflows in place of ad hoc fixes
- Provided clear visibility into risk across cloud, on-prem, and third-party environments
- Closed critical vulnerabilities and verified remediation with one-click retesting
“Everything we did in between then was waiting until the next year to get found out.”
Impact
In an environment with frequent change across cloud and hybrid infrastructure, understanding how risk accumulates matters as much as identifying where it exists.
Weekly validation made it possible to observe risk in motion:
After shifting to weekly validation, the security team was able to quantify risk in ways that had not been possible under an annual testing model:
- One AWS read-only credential was involved in 39 distinct attack paths
- Full AWS account compromise was safely achieved in under 10 minutes
- Access to over 100,000 sensitive files was confirmed using existing permissions
Instead of relying on static assessments, the team could see how overly permissive access translated into real downstream impact. This shifted internal discussions from compliance status to operational exposure.
Background
The organization operates in a highly regulated financial services industry providing insurance services that support lenders and servicers. In this environment, compliance is continuous, with processes, systems, and reporting designed to meet regulatory expectations on an ongoing basis. Security validation was evaluated mainly through annual third-party testing.
Security was everyone’s job in practice, but the processes to coordinate it were still informal.
Growth in cloud environments and outsourced operations made application and access ownership less clear, especially in AWS. As a result, remediation frequently relied on ad hoc coordination rather than defined workflows.
“Most of the remediations before that were me standing up and talking to the guy next to me.”
Annual testing confirmed compliance at a point in time, but it did little to reflect how access, permissions, and infrastructure evolved throughout the year.
Mitigation
The shift began with clarifying the purpose of the security program, not with the introduction of a new tool.
“Are we doing security just to check some compliance boxes or are we actually trying to accomplish something? And we determined we’re actually trying to accomplish something.”
That decision changed how the team approached scope and frequency. Instead of constraining testing to match compliance requirements, they expanded testing to reflect what was running in the environment.
Unsecured printers. Infrastructure appliances generating thousands of unauthorized access alerts. Overly permissive SMB shares containing sensitive data. Cloud environments that had never been tested.
“One of the things I did not expect… is it gave us a lot of insight into our infrastructure that we didn’t have before.”
What That Looked Like in Practice
Using a single AWS connected role with read-only access, NodeZero® validated how identity and access controls functioned in practice. It identified an AWS admin role created through automated tooling and IAM policies attached to a developer user, exposing an unknown privilege escalation path.
“We went full expand intelligent scope. Find literally everything you can.”
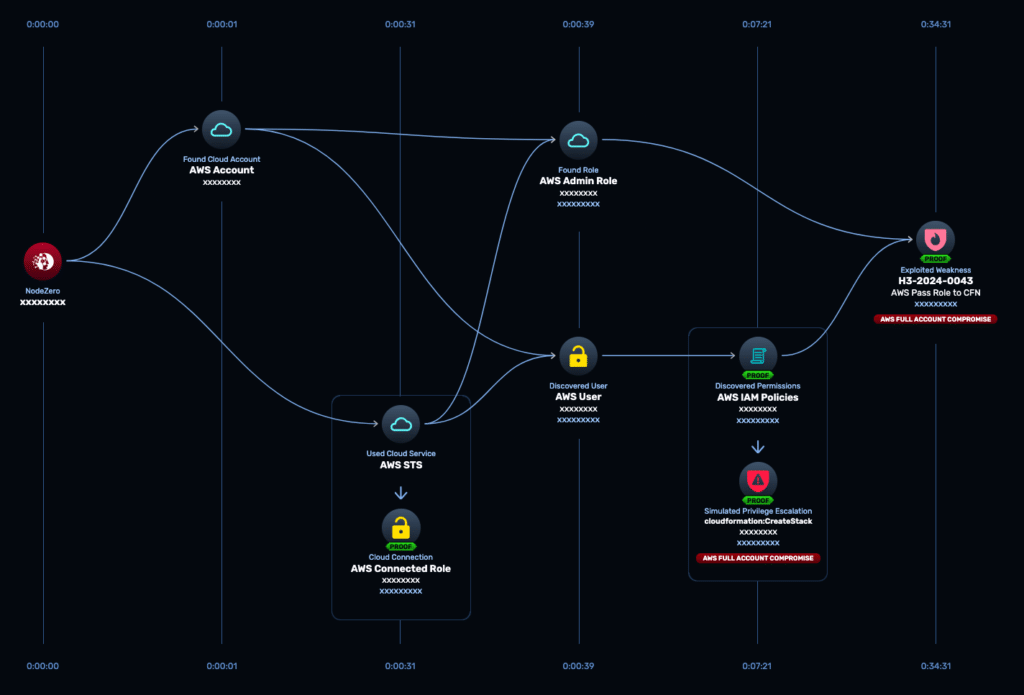
Image 1: Attack path visualization showing discovery of IAM relationships, privilege escalation, and AWS full account compromise.
That path was validated end to end, resulting in full AWS account compromise.
“When I can show an attack path with IPs, system names, and proof… it gets rid of the debate. Even if they don’t understand the technology, they understand that it’s real.”
Further testing with the same access identified an exposed S3 bucket and confirmed access to more than 100,000 files.
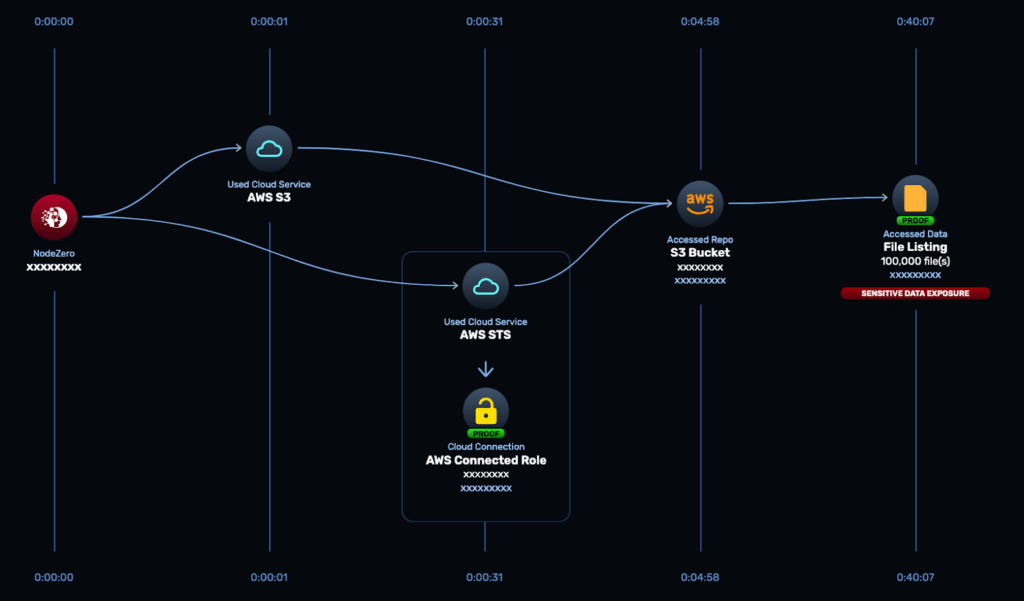
Image 2: Attack path visualization showing S3 access and confirmed sensitive data exposure.
Both outcomes reflected what was possible using permissions already in place – conditions that had existed but were not captured in annual reports.
“Not just ‘here’s an unpatched zero day with the CVE.’ It’s also… overly permissive SMB shares… with critical client data… that maybe not every single domain user should have access to.”
Increasing test frequency reduced backlog rather than expanding it.
“If you only test once a year, you have a lot of findings potentially… But it very quickly becomes obvious that if you stay on top of it, there’s a lot less to patch and a lot less critical stuff and a lot less high stuff.”
Over time, testing became routine.
“Now I think in the past eight months I’ve done maybe 40 pentests.”
That cadence shortened the exposure window, enabling a more repeatable security process.
Remediation
Regular testing introduced greater consistency into remediation efforts. Issues were identified closer to when they were introduced, and ownership became easier to assign.
Historically, remediation had created friction.
“I’ve worked with security professionals who everybody hated because it was, ‘here’s a scan, fix it, and tell me when it’s done.’”
What changed was not just frequency, but how findings were presented.
“I can say that it’s there. And I have very convenient screenshots for proof and three different possible remediation recommendations.”
Each issue came with evidence it was exploitable, context for impact, and clear guidance on how to fix it. Conversations shifted from debate to execution.
Connecting Weaknesses to Real-World Risk
Cloud misconfigurations and IAM issues were evaluated in the context of known attacker behavior using NodeZero’s Threat Actor Intelligence which connects the techniques discovered in testing and provides additional context for prioritization.
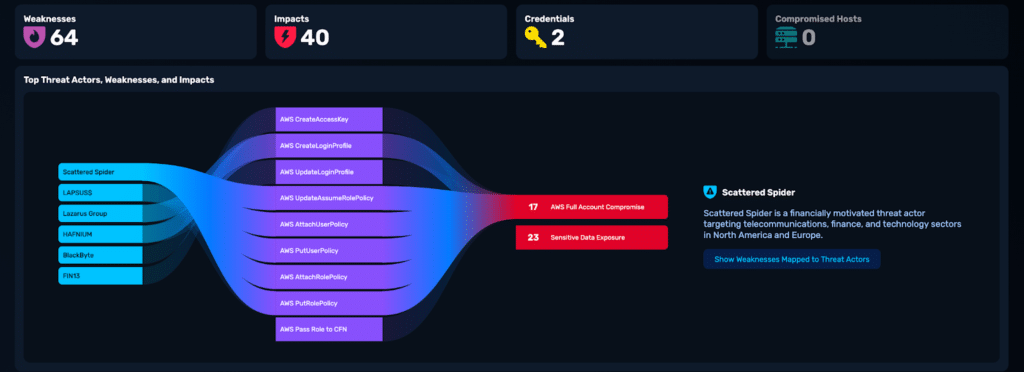
Image 3: Mapping discovered cloud IAM weaknesses to Scattered Spider TTPs and validated business impact.
That same proactive approach was applied during an internal pentest, where NodeZero identified a critical PAN-OS vulnerability (CVE-2025-0108) listed in CISA’s Known Exploited Vulnerabilities catalog. Using Rapid Response, the team validated exploitability and demonstrated a path to critical infrastructure compromise.
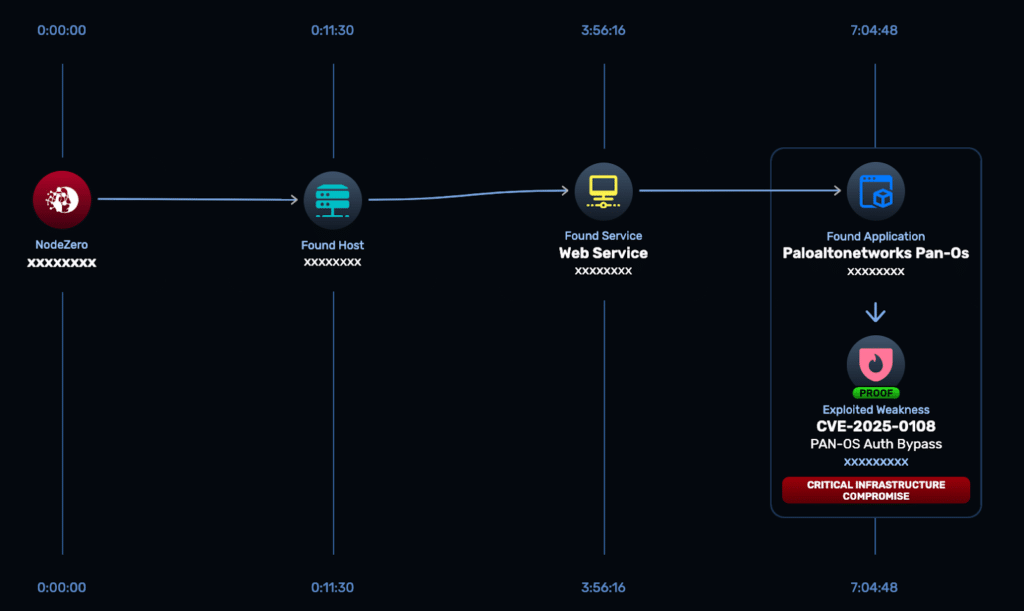
Image 4: Attack path showing exploitation of PAN-OS CVE-2025-0108 resulting in critical infrastructure compromise.
Identification, patching, and verification were completed within hours, using 1-Click Verify to confirm the attack path no longer existed.
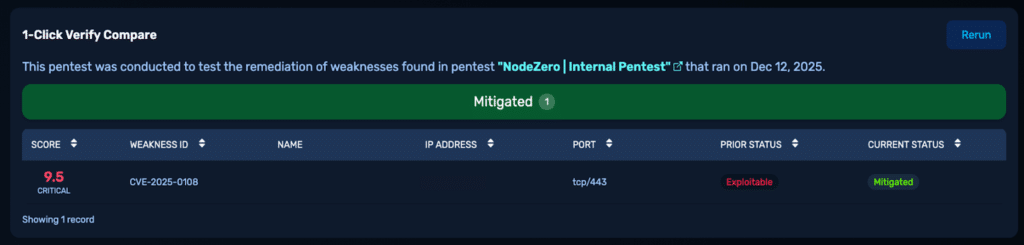
Image 5: 1-Click Verify Comparison
One-click verification confirming CVE-2025-0108 is no longer exploitable after patching.
That closed-loop model reinforced accountability and reduced the likelihood of issues resurfacing.
With remediation on firmer footing, the team extended validation to adjacent areas where assurance had been weak, including Active Directory, EDR coverage, and cloud environments across AWS, Azure, and GCP, to confirm that controls and detections were functioning as intended.
Conclusion
Annual testing confirmed compliance. Weekly testing clarified exposure.
By moving from annual snapshots to continuous validation, this organization replaced assumptions with proof. Findings became easier to prioritize. Remediation became easier to justify. Fixes could be verified instead of assumed.
One side effect was influence.
As the Security Engineer put it:
“At that point, you’re finding and remediating. It starts to feel like an AI MSP.”
Pentest Wednesday is simply the cadence required to keep pace with real change.
“It’s also a very helpful leverage tool.”

