Attack Blogs
SEARCH
CATEGORIES
TAGS
CVE-2024-23897: Assessing the Impact of the Jenkins Arbitrary File Leak Vulnerability
January 29, 2024
CVE-2024-23897: Assessing the Impact of the Jenkins Arbitrary File Leak Vulnerability.
CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass Deep-Dive
January 23, 2024
On January 22, 2024 Fortra posted a security advisory for their GoAnywhere MFT product. This advisory details an authentication bypass vulnerability, CVE-2024-0204, that allows an unauthenticated attacker to create an administrative user for the application. Customers were made aware of the issue by an internal security advisory post and patch made available on December 4,…
Writeup for CVE-2023-43208: NextGen Mirth Connect Pre-Auth RCE
January 12, 2024
Mirth Connect, by NextGen HealthCare, is an open source data integration platform widely used by healthcare companies. Versions prior to 4.4.1 are vulnerable to an unauthenticated remote code execution vulnerability, CVE-2023-43208. If you’re a user of Mirth Connect, you’ll want to upgrade to the latest patch release, 4.4.1, as of this writing.
Writeup for CVE-2023-39143: PaperCut WebDAV Vulnerability
January 12, 2024
Introduction Back in Aug. 2023 we released an advisory for CVE-2023-39143, a critical vulnerability that affects Windows installs of the PaperCut NG/MF print management software. Attackers can exploit this vulnerability to download and delete arbitrary files, and in certain common configurations upload files, leading to remote code execution. This vulnerability was patched in PaperCut version…
Cisco IOS XE CVE-2023-20198: Deep Dive and POC
October 30, 2023
Introduction This post is a follow up to https://horizon3.ai/attack-research/attack-blogs/cisco-ios-xe-cve-2023-20198-theory-crafting/. Previously, we explored the patch for CVE-2023-20273 and CVE-2023-20198 affecting Cisco IOS XE and identified some likely vectors an attacker might have used to exploit these vulnerabilities. Now, thanks to SECUINFRA FALCON TEAM's honeypot, we have further insight into these vulnerabilities. POC See below for an…
Cisco IOS XE CVE-2023-20198 and CVE-2023-20273: WebUI Internals, Patch Diffs, and Theory Crafting
October 25, 2023
Introduction There has been a lot of news around the recent Cisco IOS XE vulnerabilities CVE-2023-20198 and CVE-2023-2073. Information about this vulnerability was first published by Cisco on October 16th, 2023, and since then we have seen evidence of mass exploitation and implantation. In this post we share our technical insights so far into these…
NextGen Mirth Connect Remote Code Execution Vulnerability (CVE-2023-43208)
October 25, 2023
Mirth Connect, by NextGen HealthCare, is an open source data integration platform widely used by healthcare companies. Versions prior to 4.4.1 are vulnerable to an unauthenticated remote code execution vulnerability, CVE-2023-43208. If you’re a user of Mirth Connect, you’ll want to upgrade to the latest patch release, 4.4.1, as of this writing.
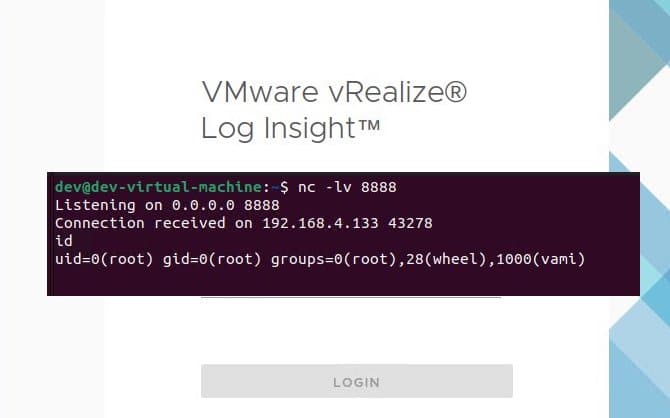
VMware Aria Operations for Logs CVE-2023-34051 Technical Deep Dive and IOCs
October 20, 2023
Introduction This report is a follow up to https://horizon3.ai/vmware-vrealize-log-insight-vmsa-2023-0001-technical-deep-dive/. Earlier this year we reported the technical details for VMSA-2023-0001 affecting VMware Aria Operations for Logs (formerly VMware vRealize Log Insight). In that report, we showed how an attacker could use three different CVEs to achieve remote code execution. During the course of that investigation, we…
Cisco IOS XE Web UI Vulnerability: A Glimpse into CVE-2023-20198
October 19, 2023
On Monday, 16 October, Cisco reported a critical zero-day vulnerability in the web UI feature of its IOS XE software actively being exploited by threat actors to install Remote Access Tools (RATs) and backdoor vulnerable devices exposed on the internet.
Apache Superset Part II: RCE, Credential Harvesting and More
September 6, 2023
Apache Superset is a popular open source data exploration and visualization tool. In a previous post, we disclosed a vulnerability, CVE-2023-27524, affecting thousands of Superset servers on the Internet, that enables unauthorized attackers to gain admin access to these servers. We also alluded to methods that an attacker, logged in as an admin, could use…